A critical vulnerability has been discovered in several models of Xerox printers, allowing attackers to remotely execute arbitrary commands with elevated privileges. At risk are the EC80xx, AltaLink, VersaLink, and WorkCentre models, if they have not been updated to the latest firmware versions.
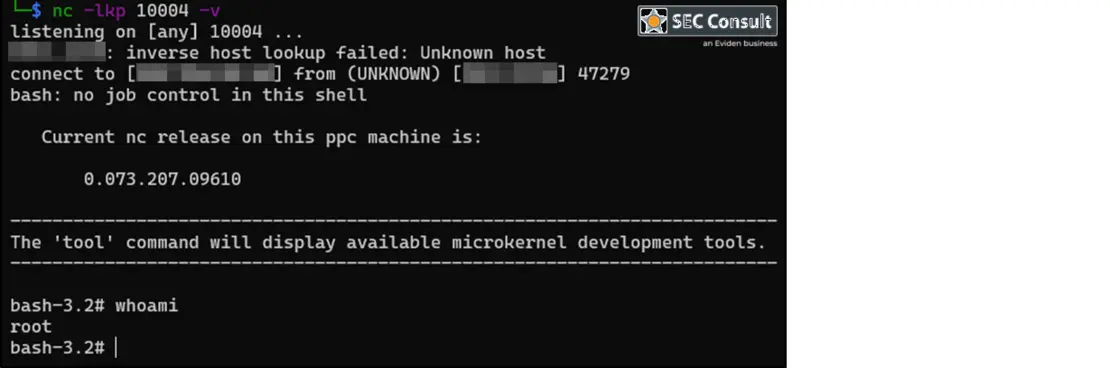
The vulnerability, tracked as CVE-2024-6333, enables attackers with administrative credentials to access the printer’s operating system through the web interface and execute commands as a superuser.
The flaw lies within the “Network Troubleshooting” section of the printer’s web interface, which utilizes the tcpdump utility. Due to insufficient input validation, attackers can inject their own commands into the string by mimicking IPv4 settings. An example of such an attack could involve altering the address to “0.0.0.0$(bash $TMP~cmd),” allowing the execution of commands stored in “/tmp/~cmd.”
Exploitation of this vulnerability could result in the installation of a reverse shell, granting the attacker full control over the printer’s system.
SEC Consult reports that the vulnerability has been confirmed on the Xerox WorkCentre 7970 (073.200.167.09610) and WorkCentre 7855 (073.040.167.09610) models. To prevent potential attacks, users are strongly advised to update their device firmware and review the remediation instructions provided in the official Xerox advisory XRX24-015.
Experts also recommend conducting a comprehensive security audit of Xerox products to identify other potential threats. In response to the identified issues, Xerox emphasizes its commitment to ensuring security and enhancing its clients’ workflows through innovative solutions.


