Cybersecurity researcher Marcus Hutchins, known as MalwareTech, has released an automated scanner designed to detect vulnerable Linux and UNIX servers susceptible to attacks via the CUPS vulnerability, tracked as CVE-2024-47176. This tool can assist system administrators in locating devices with the cups-browsed service enabled, which under certain conditions may be exposed to remote code execution (RCE).
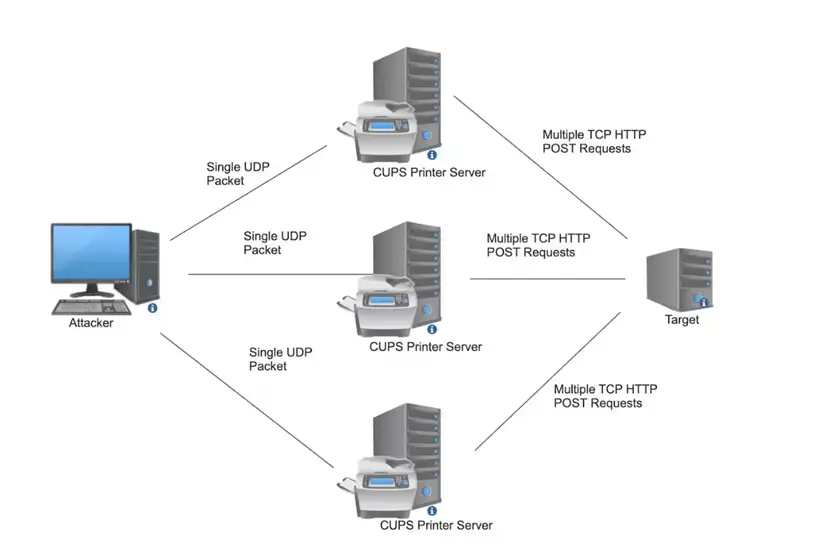
The vulnerability was first brought to light last month by security researcher Simone Margaritelli, who discovered the issue. Although the potential for real-world RCE exploitation is limited, researchers from Akamai stated that this vulnerability could also be exploited to amplify DDoS attacks by up to 600 times.
The core of the issue lies in the fact that the cups-browsed service binds its control port (UDP 631) to any available network interface, making it accessible to any system. Without proper authentication, any network user could send commands through this port.
Hutchins’ scanner uses a Python script to help system administrators scan local networks and identify devices running vulnerable versions of CUPS. According to the developer, even if the port is not accessible via the internet due to firewalls or NAT, it can still be reachable within the local network, presenting opportunities for privilege escalation and lateral movement.
The scanner works by sending specially crafted UDP packets to network addresses within a specified range. Vulnerable devices respond with a request to the server, indicating the presence of the issue. The scan results are saved in two logs: the first contains the IP addresses and CUPS versions of vulnerable devices, while the second provides detailed information about the HTTP requests sent, enabling deeper analysis.
By using this scanner, system administrators can plan patches in advance and mitigate the risk of exploitation of CVE-2024-47176.
This case with CUPS clearly illustrates the importance of regularly checking network devices for vulnerabilities. In today’s landscape, even seemingly minor errors can become tools for large-scale attacks that threaten the integrity of entire systems.


