Synthesis of TTPs used by Helldown
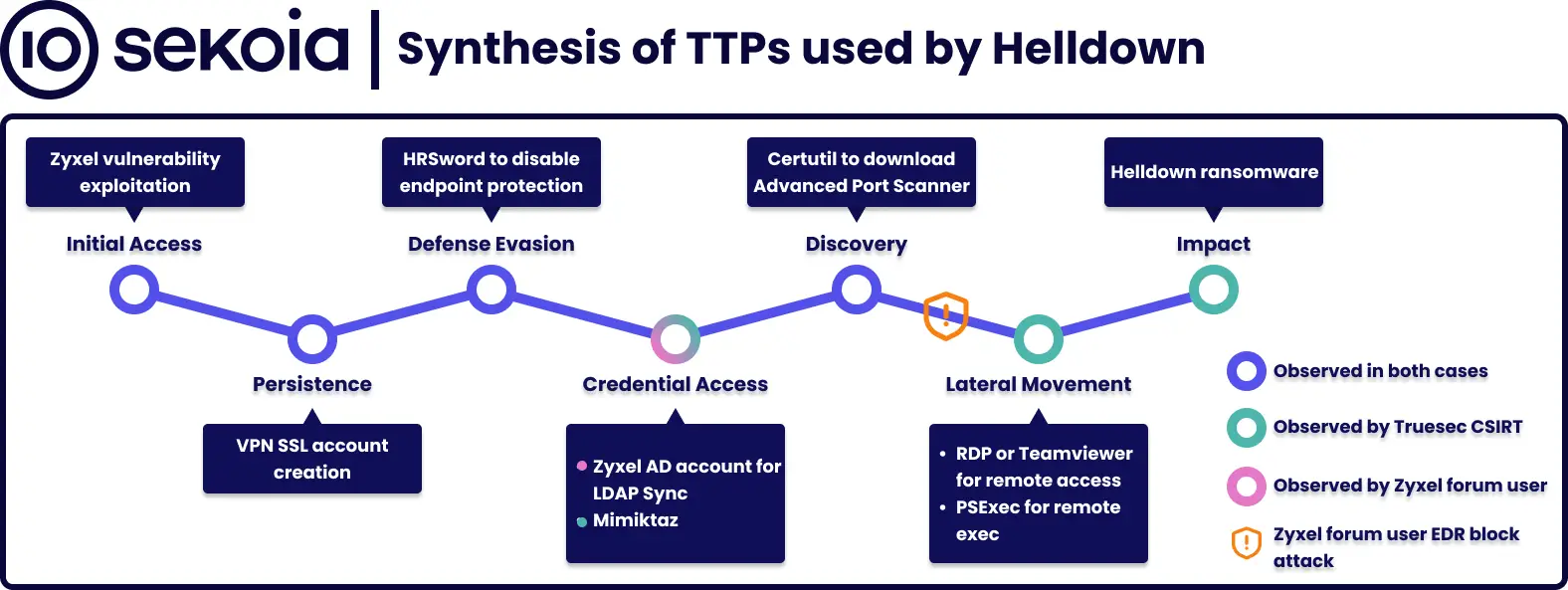
A new ransomware operation known as Helldown is gaining momentum in cyberspace, reportedly exploiting vulnerabilities in Zyxel firewalls to infiltrate corporate networks. According to the French cybersecurity firm Sekoia, these attacks enable criminals to encrypt devices and exfiltrate sensitive data.
Since its launch in the summer of 2024, Helldown has rapidly expanded its list of victims, publishing company data on its leak site. To date, 28 victims have been listed, primarily small and medium-sized enterprises in the United States and Europe.
Helldown was first documented by Cyfirma researchers on August 9 and subsequently analyzed by Cyberint in October. Notably, the Linux version of the malware targets VMware files, although its functionality remains partially inactive, suggesting it is still in development.
Sekoia reports that the Windows variant of Helldown is based on leaked LockBit 3 code and shares similarities with Darkrace and Donex. However, direct connections between them have not been established. Among the prominent victims is the European division of Zyxel, a provider of networking and cybersecurity solutions.
Unlike other ransomware groups, Helldown adopts a less selective approach to data exfiltration, indiscriminately stealing massive volumes of information. One breach reportedly included up to 431 GB of data. The ransomware’s encryption processes are executed via batch files, highlighting its relatively rudimentary technological sophistication.
During its investigation, Sekoia identified the use of the account “OKSDW82A” and a configuration file named “zzz1.conf” in attacks targeting Zyxel devices running vulnerable firmware version 5.38. The exploited flaw is believed to be CVE-2024-42057, which was patched in September with the release of firmware version 5.39.
Malware samples associated with Helldown were uploaded in October. Although the code appeared incomplete, experts are confident in its link to attacks on Zyxel devices. Zyxel has not responded to journalists’ inquiries for comments but issued a statement on November 21, assuring that firmware version 5.39 offers protection against all known threats.


