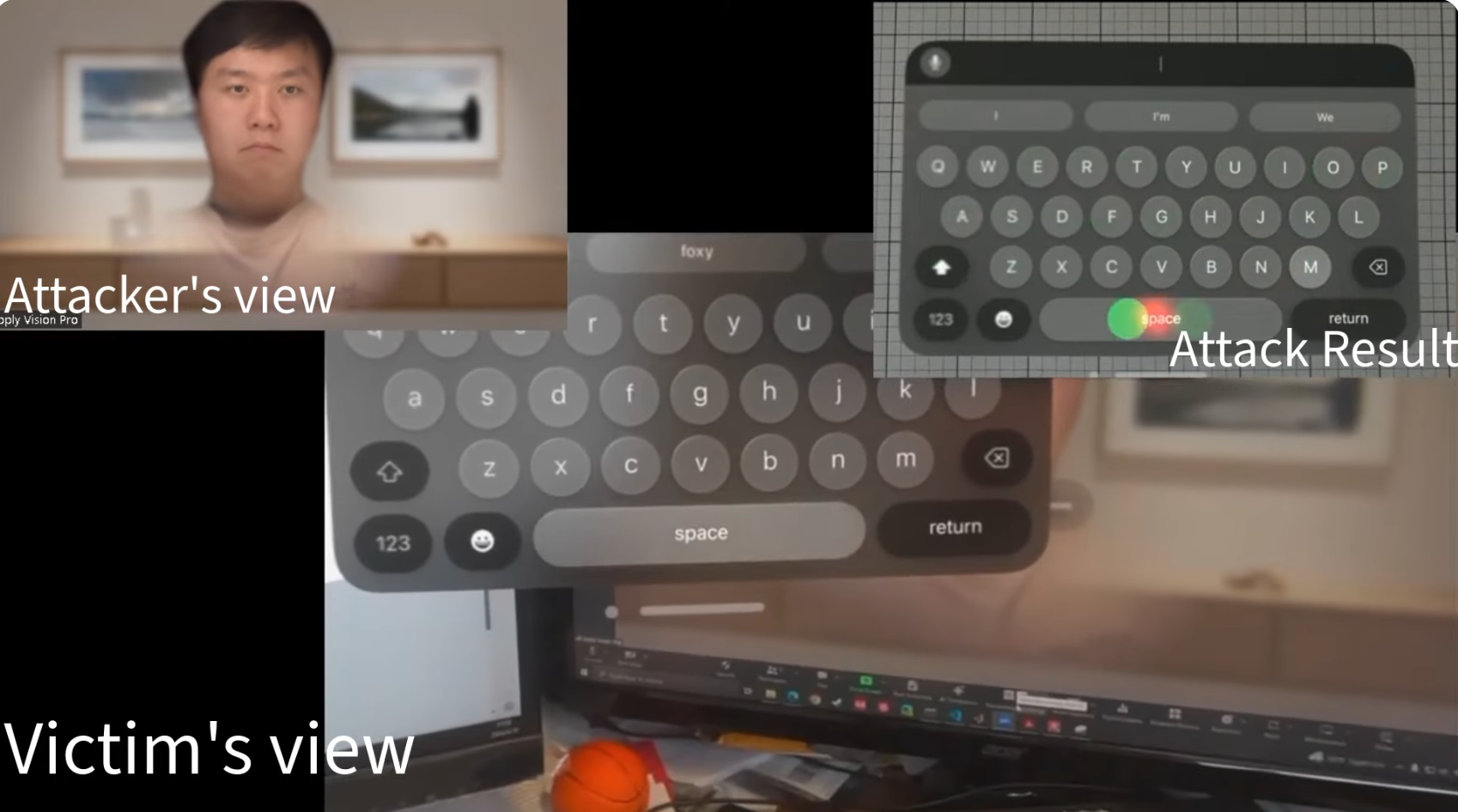
A vulnerability was recently discovered in Apple’s mixed reality headset, Apple Vision Pro, allowing attackers to intercept data from the virtual keyboard. The attack, named GAZEploit, has been registered as CVE-2024-40865, though its exact rating on the CVSS scale has yet to be determined.
The attack exploits the ability of a potential adversary to analyze the user’s eye movements through a virtual avatar, which is utilized during device interaction. If a malicious actor gains access to the avatar’s image, they can deduce which characters are being typed on the virtual keyboard, thereby enabling the theft of sensitive data.
Apple addressed the issue in the visionOS 1.3 update, released on July 29, 2024. The vulnerability was linked to a component called Presence, responsible for managing avatars within the system. According to Apple, the issue was resolved by temporarily suspending the avatar’s activity when data is being entered via the virtual keyboard.
The attack became possible through the use of a trained AI model that analyzed recordings of the avatar, as well as the user’s eye movements, to pinpoint moments when data was entered on the virtual keyboard. The algorithm then correlated gaze directions with specific keys on the keyboard, allowing it to reconstruct the typed text.
Researchers emphasized that GAZEploit is the first known attack of its kind, using eye movement data to remotely recover input information.
This case highlights the critical importance of security in emerging technologies, where even a glance can be weaponized for cyberattacks. Protecting personal data in virtual reality is becoming a matter of utmost urgency, and the GAZEploit incident underscores the need for swift action to mitigate such threats, ensuring users feel safe in the digital spaces of the future.


