For over a year, malicious actors exploited a vulnerability in Windows that allowed the execution of malicious code before Microsoft finally addressed the issue. The vulnerability, identified as CVE-2024-38112, was present in both Windows 10 and Windows 11 and forced victim devices to open the obsolete Internet Explorer browser, which was retired in 2022.
Researchers from Check Point discovered that malicious code exploiting this vulnerability was actively distributed from January 2023 to May 2024. Microsoft, in turn, patched the vulnerability only last Tuesday as part of its monthly Patch Tuesday security update. The vulnerability was rated at a severity level of 7.0 out of 10 and was found in the MSHTML engine of Windows.
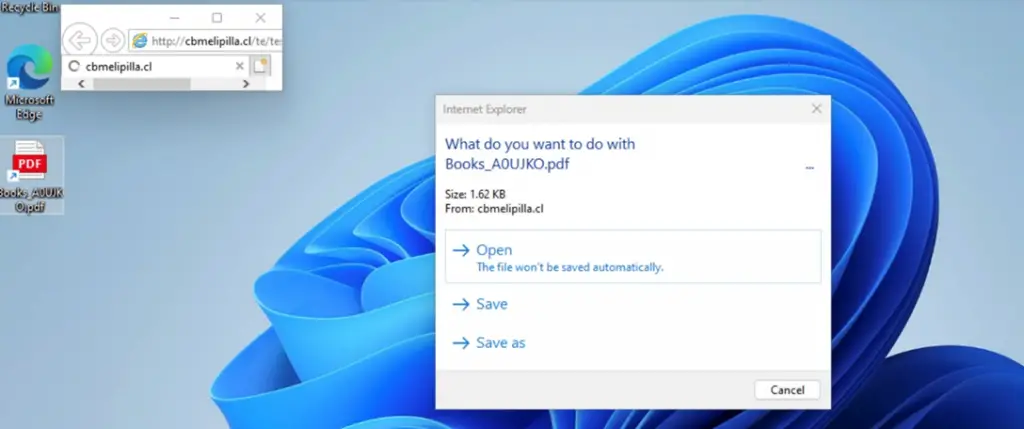
The attack employed previously unknown methods to deceive Windows users into executing malicious code on their devices. One example included a file named “Books_A0UJKO.pdf.url,” which appeared to be a PDF but was actually a link that opened a specified application.
The link in the file launched “msedge.exe,” responsible for opening the Edge browser, but used the “mhtml:” and “!x-usc:” attributes, which ultimately opened Internet Explorer instead of Edge. This trick allowed attackers to exploit unpatched vulnerabilities in IE to execute arbitrary code on the victim’s device.
Upon opening such a file, the user encountered a dialog box from Internet Explorer, suggesting they open a file disguised as a PDF.

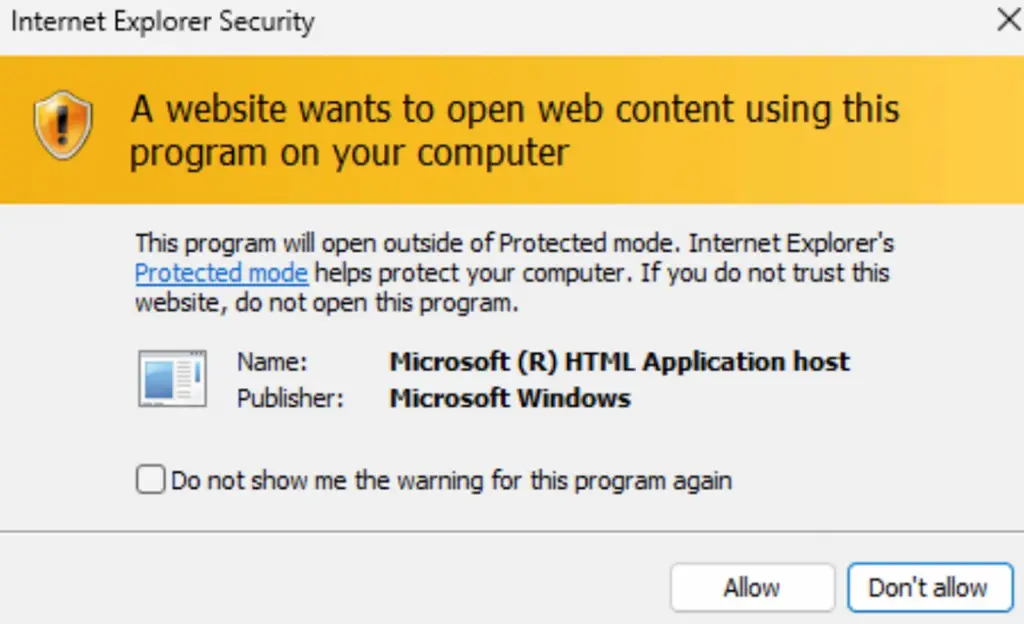
If the user agreed, Windows displayed a second dialog box warning about the content download. By clicking “allow,” Internet Explorer loaded an “.hta” file, which executed the malicious code.
Haifei Li, a researcher at Check Point, explained that the first attack technique involved using the “mhtml” trick to invoke Internet Explorer instead of more secure browsers like Chrome or Edge. The second technique deceived the user into thinking they were opening a PDF file when in reality, a dangerous HTA file was executed.
The researchers provided cryptographic hashes for six malicious URL files used in the identified malicious campaign. Windows users can use these hashes to check whether their devices were targeted by the described attack.


