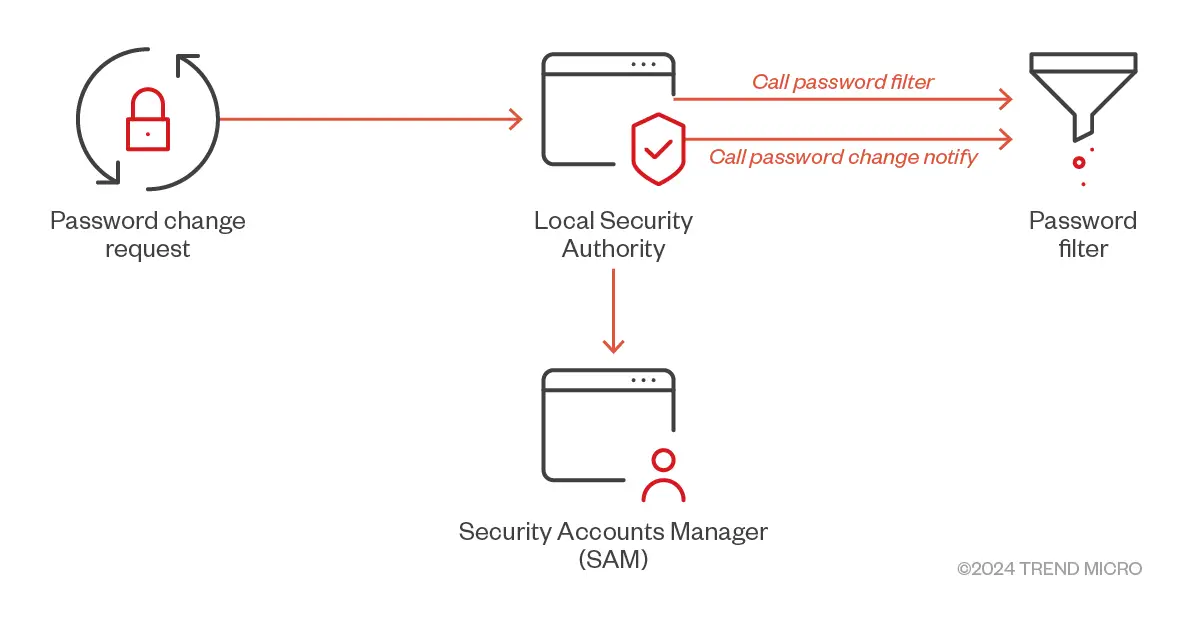
Registering the DLL with the LSA
The Iranian hacker group OilRig (also known as APT43 or Cobalt Gipsy) has intensified its attacks on organizations and personal systems in the United Arab Emirates and other Gulf countries. Cybersecurity experts from Trend Micro have reported that the attackers are targeting credentials to gain access to servers, which they subsequently use to deploy malicious code.
The attacks are focused on vulnerable servers, where hackers deploy web shells that enable the execution of PowerShell scripts and the installation of malware. A key element of the attack is the exploitation of the CVE-2024-30088 vulnerability, which Microsoft patched in June 2024. This vulnerability, classified as critical with a base score of 7.0, pertains to privilege escalation in the Windows kernel.
The malicious software known as STEALHOOK plays a pivotal role in these attacks. This malware gathers and transmits data to a command-and-control (C2) server under the hackers’ control. A notable feature of STEALHOOK is its ability to disguise stolen information as legitimate data, sending it through Microsoft Exchange servers, making detection significantly more challenging.
Experts emphasize that OilRig is a state-sponsored hacker group backed by Iran. It remains one of the most active groups in the Middle East region and is likely linked to another Iranian group, FOX Kitten, previously observed in ransomware attacks. A large portion of these attacks are aimed at the energy sector, raising serious concerns, as any disruptions to these operations could cause substantial harm not only to the organizations but to the general population as well.
Despite evidence of CVE-2024-30088 being exploited, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has yet to include it in their catalog of known exploited vulnerabilities.


