Recently, a security researcher known by the pseudonym @hyprdude published an in-depth report on the vulnerability CVE-2024-20017, discovered in the network daemon wappd. This daemon is utilized in SDKs from MediaTek and SoftAP drivers for chipsets that support Wi-Fi 6, and is commonly found in devices such as routers from Ubiquiti, Xiaomi, and Netgear.
The vulnerability is a buffer overflow caused by improper handling of data received from network packets. Exploiting this flaw enables an attacker to execute arbitrary code on vulnerable devices through various attack vectors. In the report, @hyprdude detailed four approaches to exploiting this vulnerability.
Method 1: Hijacking RIP and Executing ROP
The first exploitation method involves simply hijacking the return instruction pointer (RIP) using a ROP (Return-Oriented Programming) chain. This method is most effective on systems where modern protections, such as ASLR (Address Space Layout Randomization) and Stack Canaries, are not implemented.
The essence of this method lies in overflowing the stack to the point where the return address of a function on the stack can be overwritten with an address pointing to the payload. In this case, a ROP chain is employed, invoking the `system()` function with a pre-prepared command to execute on the device. This grants the attacker full control over the device. Although this method is the simplest, it has become outdated due to the widespread adoption of protective technologies.
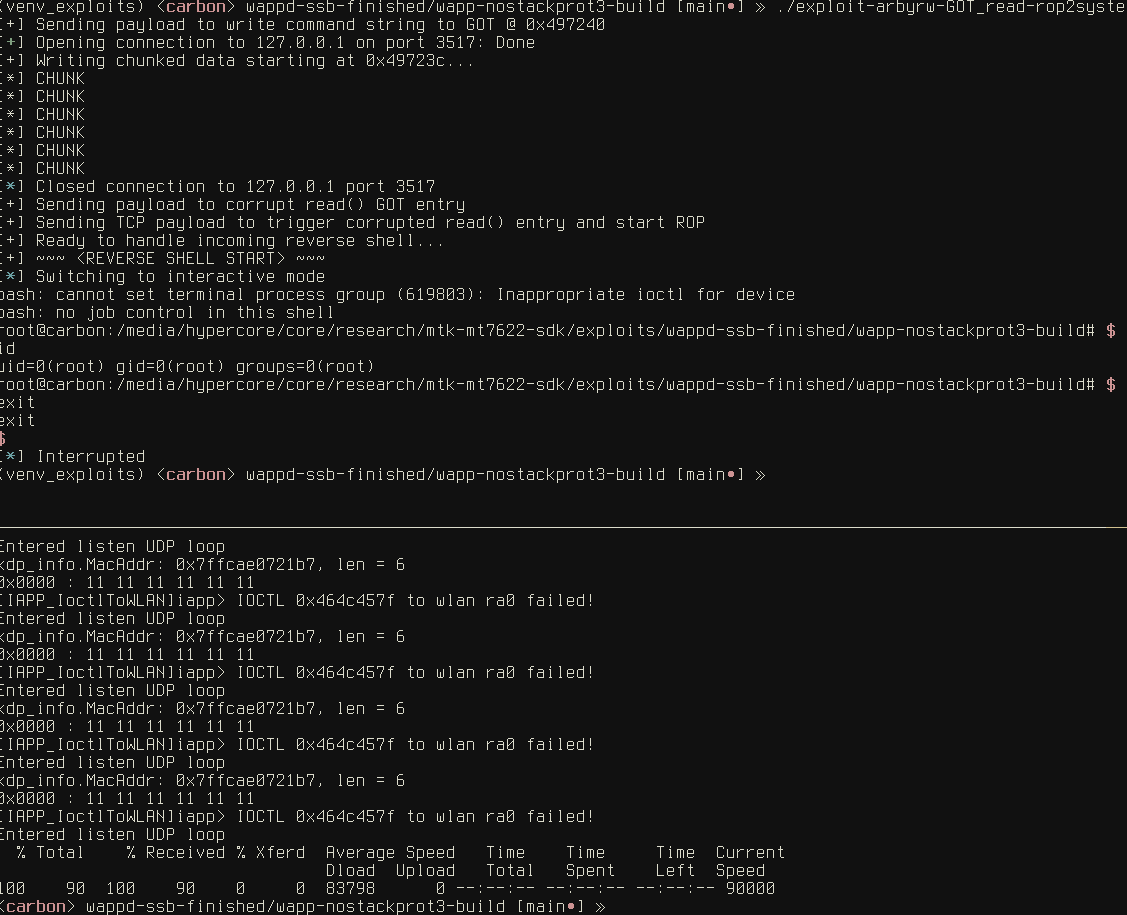
Method 2: Arbitrary Write Through Pointer Corruption
The second method is based on a more complex concept and requires the presence of protective mechanisms such as ASLR, Stack Canaries, and partial RELRO (Read-Only Relocation). In this scenario, the attacker leverages the stack overflow to corrupt pointers, enabling control over where data is written in memory.
By using this method, the attacker can overwrite the Global Offset Table (GOT), which holds the addresses of functions used by the program. By substituting addresses in the GOT, the attacker can redirect the program’s execution to their code, allowing them to execute arbitrary commands on the device. Although more challenging to implement, this method is significantly more effective on protected systems.
Method 3: Reverting to Return Address Overwrite and Utilizing ROP on Fully RELRO-Protected Systems
The third method is even more complex, as it targets a system with full RELRO protection, which makes it impossible to modify the GOT. Here, the attacker uses a combination of methods: first, achieving arbitrary write access, and then crafting a sophisticated ROP chain that bypasses protections and executes the desired command.
This ROP chain involves several sequential commands that manipulate registers and the stack to circumvent the system’s defensive mechanisms. At the end of the chain, the system calls the `system()` function, passing it the necessary command. This method is particularly difficult to execute as it requires a deep understanding of the operating system’s architecture and defenses.
Method 4: Exploitation on a Real Device with ARM64 Architecture
The fourth method was specifically developed to exploit the vulnerability on a real device—a Netgear WAX206 router with an ARM64 architecture. This device employs all modern protection methods, including ASLR, NX (No-Execute), full RELRO, and Stack Canaries. However, due to the peculiarities of the ARM64 architecture and code optimization techniques, the attacker found a way to bypass these defenses. Instead of ROP, JOP (Jump-Oriented Programming) was used to redirect the program’s execution.
This method involves several stages: first, the attacker gains the ability to write data to arbitrary memory locations; then they overwrite the return address and other critical structures in memory to prepare the execution of the `system()` command. This technique vividly demonstrates how complex exploiting vulnerabilities on real devices can be, especially considering the unique aspects of the ARM64 architecture.
Bonus: Exploiting Kernel Vulnerabilities via IOCTL Calls
In conclusion, the author presented another intriguing method that allows the exploit to be used against a kernel vulnerability. By using a JOP chain, the attacker can perform arbitrary IOCTL (Input/Output Control) calls, gaining access to critical kernel functions and extending their control over the device. This method is challenging to implement, but its use demonstrates how powerful a single exploit can be when targeted at different levels of a system.
Conclusion
This detailed analysis of the CVE-2024-20017 vulnerability underscores the importance of multi-layered protection in modern systems. The same bug can be exploited in various ways, and each of these methods requires deep knowledge and a creative approach to exploit development.
This example clearly illustrates that even a simple buffer overflow can become a significant security threat if the attacker has sufficient knowledge and resources to exploit it.


