The Shadowserver Foundation has uncovered a botnet leveraging a zero-day vulnerability in obsolete GeoVision devices, exploiting them for DDoS attacks or cryptocurrency mining.
The vulnerability, CVE-2024-11120, carries a CVSS score of 9.8 and involves OS command injection, enabling unauthorized attackers to execute arbitrary commands on the system. Exploitation of this zero-day vulnerability is already underway, as reported by Taiwan’s CERT. Experts have identified several affected device models:
- GV-VS12: A two-channel H.264 video server that converts analog video signals into digital streams for network transmission.
- GV-VS11: A single-channel video server designed for digitizing analog video for streaming over a network.
- GV-DSP LPR V3: A Linux-based license plate recognition (LPR) system.
- GV-LX4C V2 and GV-LX4C V3: Compact video recorders intended for mobile surveillance.
All these models are discontinued and no longer supported by the manufacturer, leaving them particularly vulnerable as no security updates are forthcoming.
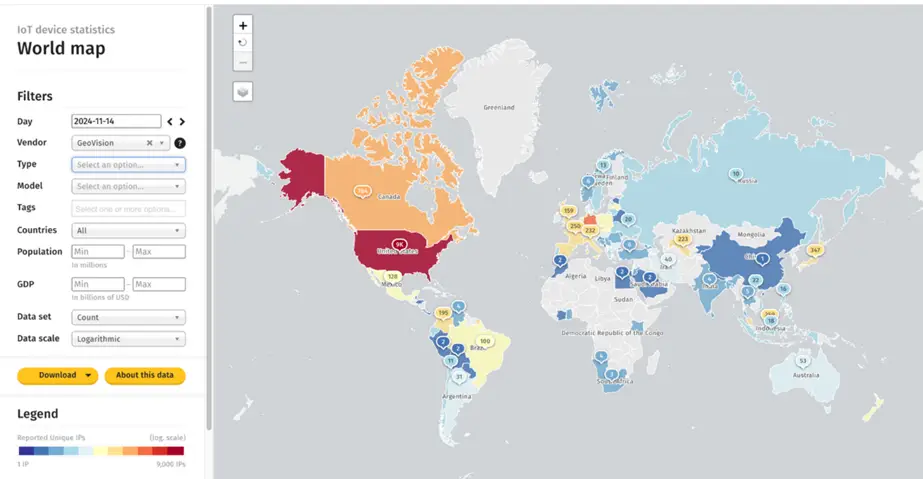
According to The Shadowserver Foundation, approximately 17,000 GeoVision devices remain publicly accessible online and are vulnerable to CVE-2024-11120. The highest concentration is in the United States (9,100), followed by Germany (1,600), Canada (800), Taiwan (800), Japan (350), Spain (300), and France (250).
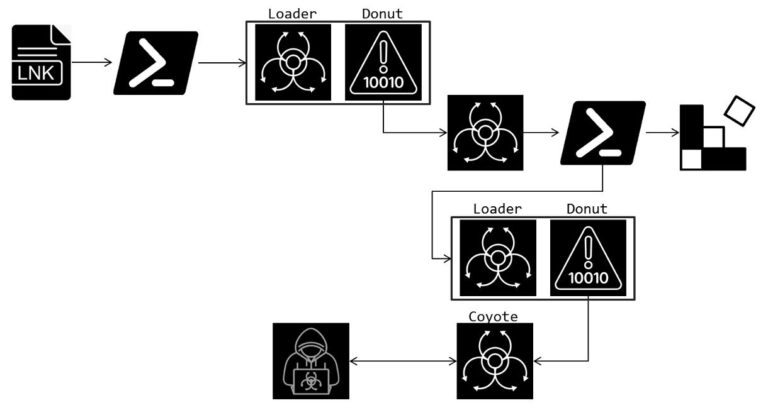
Security researchers suspect that a variant of the Mirai botnet is responsible for these attacks, commonly deployed for DDoS assaults or covert cryptocurrency mining.
Signs of Compromise
Indicators that a device may have been compromised by the botnet include:
- Overheating;
- Reduced performance or frequent crashes;
- Unexplained changes to configuration settings.
Mitigation Recommendations
To minimize risks, the following measures are advised:
- Perform a factory reset on the device.
- Replace default credentials with a strong, unique password.
- Disable remote access.
- Place the device behind a firewall.
If replacing outdated devices with supported models is not feasible, experts recommend isolating them in a separate network and closely monitoring their activity. However, replacing obsolete devices with modern, secure alternatives remains the most effective strategy for preventing such attacks.