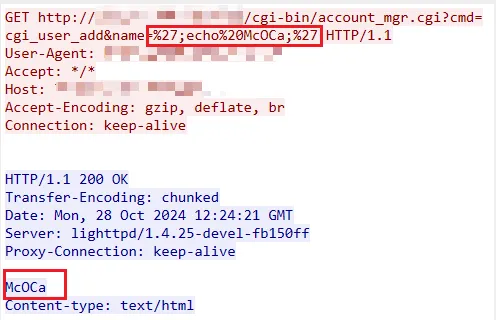
Over 60,000 D-Link data storage devices, which have reached their end of life (EoL), have been rendered vulnerable due to a critical Command Injection flaw. This vulnerability, designated CVE-2024-10914, carries a severe CVSS rating of 9.2 and is tied to insufficient sanitization of the name parameter in the “cgi_user_add” command.
An unauthorized attacker could exploit this vulnerability to execute arbitrary commands by sending specially crafted HTTP requests to affected devices. The flaw impacts several popular NAS models from D-Link frequently used by small businesses: DNS-320 (version 1.00), DNS-320LW (version 1.01.0914.2012), DNS-325 (versions 1.01 and 1.02), and DNS-340L (version 1.08).
A cybersecurity researcher from Netsecfish has published details on how to exploit this vulnerability, which involves sending a specially crafted HTTP request to the NAS device with malicious commands embedded within the name parameter. The researcher also provided a cURL command example illustrating the exploitation process.
During its analysis, Netsecfish identified over 61,000 vulnerable D-Link devices across 41,097 unique IP addresses, exposing an extensive array of data to potential risk due to their public accessibility.
In a recent security bulletin, D-Link confirmed that a patch for CVE-2024-10914 will not be issued, advising users to either retire these devices or restrict their internet accessibility.
Earlier this year, in April, the same researcher uncovered a similar vulnerability—CVE-2024-3273—also related to Command Injection and an embedded backdoor affecting the same D-Link NAS models. At that time, online scans indicated more than 92,000 vulnerable devices. D-Link previously confirmed the cessation of its NAS product line, along with the discontinuation of further support.


