Akamai specialists have uncovered a new vulnerability in the Common Unix Printing System (CUPS), which can be exploited to carry out DDoS attacks. To initiate an attack, an attacker merely needs to send a single packet to a vulnerable CUPS service exposed to the internet.
According to Akamai, more than 198,000 vulnerable devices are online, of which approximately 34% (over 58,000) could potentially be leveraged for DDoS attacks. The most alarming aspect is that launching a successful attack requires minimal resources: all vulnerable CUPS services can be compromised within seconds.
On September 26, the researcher evilsocket released information regarding vulnerabilities in CUPS that can be used for remote code execution (RCE). The attack involves a chain of four vulnerabilities, enabling command execution on a remote server via manipulations with IPP-URLs.
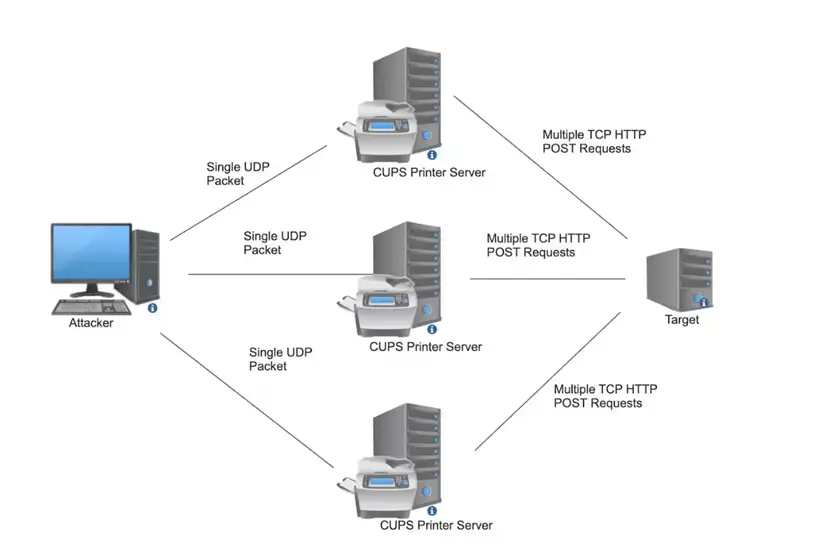
However, aside from remote code execution, CUPS can also be exploited to amplify DDoS attacks. The essence of the attack is that the attacker sends a modified packet, identifying the victim’s address as a printer to be added to the system. In response, the vulnerable CUPS server begins sending large IPP/HTTP requests to that address.
A simple script is all a hacker needs, directing a malicious UDP packet to the vulnerable CUPS. The CUPS server then begins sending requests to the victim’s IP address, overwhelming it with traffic and depleting its resources.
Akamai’s research found that among the 58,000 vulnerable devices, some exhibited “infinite loop” behavior—after receiving the initial requests, they continued sending thousands of queries, sometimes indefinitely. This behavior significantly burdens the resources of both the targeted servers and the vulnerable CUPS hosts.
Most of the vulnerable devices are running outdated versions of CUPS, such as version 1.3, released in 2007. The lack of updates heightens the risk of malicious exploitation of these servers for cyberattacks.
The analysis revealed that this type of attack could amplify traffic by an average of 600 times, and in the worst cases, by more than 100 times. Even if the amplification factor is not extraordinarily high, the sheer volume of data sent to the victim can overwhelm their servers.
Experts warn that hackers may soon begin exploiting this vulnerability, as outdated versions of CUPS remain widespread and system updates take time. Organizations that may be potential targets are advised to take protective measures, including updating CUPS software or blocking access to the service’s ports (UDP/631).


