Cybercriminals linked to China continue to expand their attacks on government institutions in Southeast Asia as part of a new wave of espionage activity, codenamed Crimson Palace, according to Sophos, a company specializing in threat monitoring.
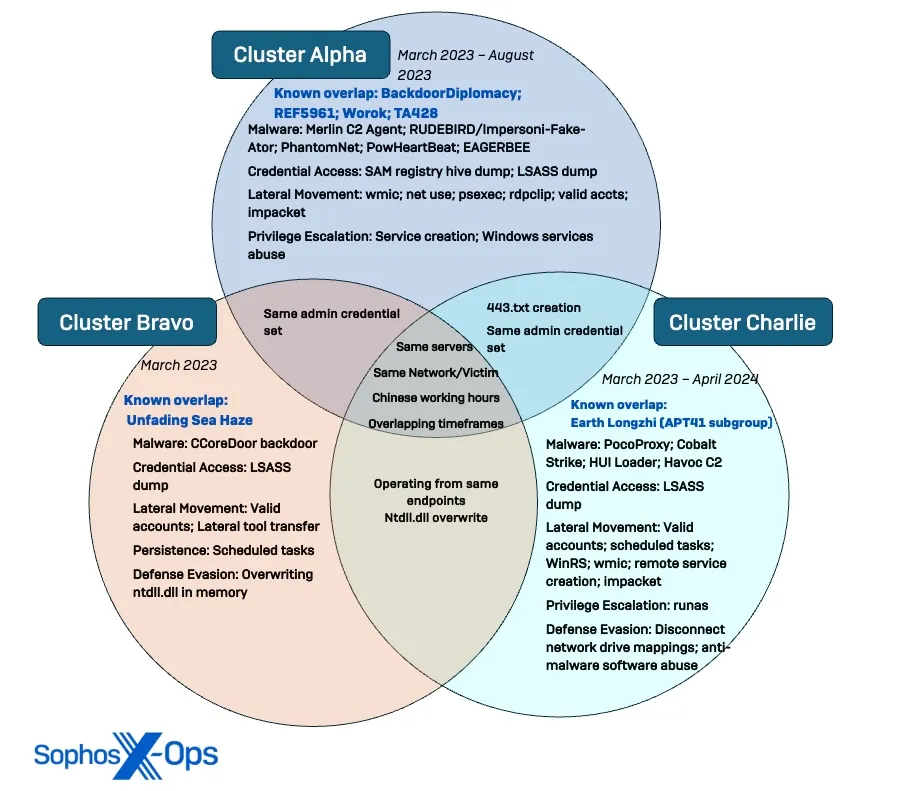
The attacks involve three groups identified by researchers as Cluster Alpha (STAC1248), Cluster Bravo (STAC1870), and Cluster Charlie (STAC1305), each following distinct operational patterns. According to the Sophos report, the attackers are leveraging networks of already compromised organizations to deliver malware, disguised as trusted sources.
The Crimson Palace operation was first detected by Sophos in June 2024, though the attacks began as early as March 2023, continued through to April 2024. Notably, the most recent activities connected to Cluster Bravo were observed between January and June 2024, affecting 11 organizations in the region.
Of particular interest is Cluster Charlie, also known as Earth Longzhi. This group was active from September 2023 to June 2024, utilizing a variety of tools to compromise networks, including well-known platforms like Cobalt Strike and Havoc, enabling deeper infiltration and further damage to systems.
Researchers have highlighted that the primary objective of these attacks is not only to gather valuable intelligence but also to solidify footholds within victim networks. The hackers sought to bypass security systems and regain access to infrastructure, even after their malware had been neutralized.
It is also noteworthy that Cluster Charlie has been actively employing Dynamic Link Library (DLL) hijacking techniques, a method previously used by Cluster Alpha, underscoring similar approaches across the different groups.
Additionally, the hackers’ arsenal includes programs such as RealBlindingEDR and Alcatraz, which assist in evading antivirus detection and concealing malicious files. One of the most dangerous tools at their disposal is the newly developed keylogger TattleTale, capable of stealing data from Google Chrome and Microsoft Edge browsers.
This malicious software can also gather information about the victim’s systems, including domain controller names and security settings, making it particularly dangerous.
All three groups operate in concert, with each playing a specific role in the attack chain: Cluster Alpha handles network infiltration and reconnaissance, Cluster Bravo deepens system penetration, while Cluster Charlie focuses on data exfiltration.
Experts recommend that organizations in vulnerable regions strengthen their cybersecurity measures, including regular software and security system updates, network traffic monitoring, and the implementation of threat detection and prevention solutions.
Particular attention should be given to protecting email servers and other critical infrastructure elements, as these are prime targets for attack. Continuous vulnerability assessments and the adoption of proactive defense methods will help mitigate the risks and minimize damage from such cyber espionage operations.


