Windows users in Brazil have encountered a novel cyberattack deploying the Coyote banking trojan. This malware pilfers data from over 70 financial applications through an intricate, multi-stage infection process.
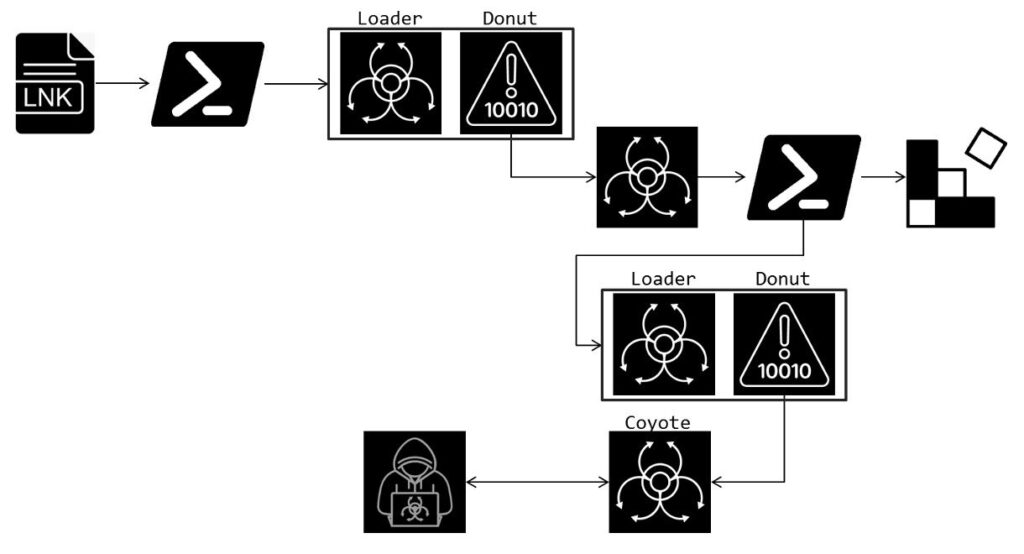
According to Fortinet specialists, the trojan is highly versatile: it logs keystrokes, captures screenshots, and manipulates banking website interfaces to seize login credentials. The malicious code is disseminated via Windows shortcuts (LNK) containing PowerShell commands.
Coyote was initially identified in early 2024 by Kaspersky Labs, when the attack employed a Squirrel installer that launched an Electron-based Node.js application and subsequently executed a Nim-based malicious loader.
In this updated infection scheme, the malware spreads through an LNK file executing a PowerShell command, downloading an additional script from a remote server. This script initiates an intermediate loader responsible for executing the primary malicious code.
The next phase involves Donut, a tool that decrypts and runs an MSIL (Microsoft Intermediate Language) executable file. For persistence, the trojan modifies the Windows registry, creating an entry in HCKU\Software\Microsoft\Windows\CurrentVersion\Run. This entry triggers a concealed PowerShell command, downloading and executing encrypted code from a remote resource.
Upon execution, Coyote gathers device information, a list of installed antivirus software, and transmits this data to the perpetrators. The malware also analyzes the system environment to evade detection in sandboxes and virtual machines.
This new version significantly broadens its target list, now attacking over a thousand web resources, including cryptocurrency exchanges and hospitality services. When a user visits a listed website, the malware connects with the attackers’ server and may activate a keylogger, capture a screenshot, or alter the page interface.
Researchers emphasize that Coyote’s multi-stage infection makes it particularly dangerous. The initial use of LNK files allows it to bypass traditional defenses, and the complex malware structure hinders detection and analysis. Experts advise users to exercise caution with suspicious system shortcuts and employ robust antivirus solutions.