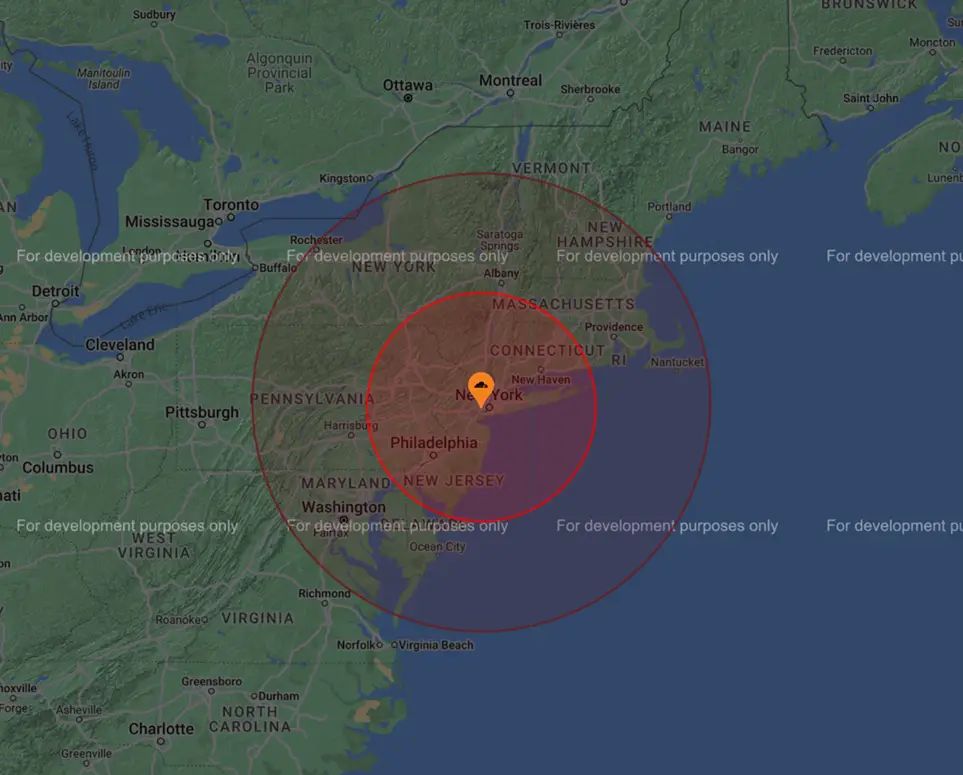
Example Map Depicting the Target User's Geolocation (404 Media)
The vulnerability in Cloudflare’s system enables the identification of the specific data center used by messaging platforms to cache images, allowing for an approximate determination of users’ locations on services such as Signal, Discord, X, and others. In some cases, executing the attack requires nothing more than sending an image, enabling an attacker to retrieve location data without any user interaction.
Although the obtained data is relatively imprecise—limited to the level of a city or state during experiments—this case highlights the critical need to safeguard not only the content of messages but also users’ network activity, especially those in high-risk groups.
The issue lies within Cloudflare’s Content Delivery Network (CDN), which accelerates data loading by utilizing a distributed network of servers. The CDN caches content on servers closest to the user, potentially revealing where the caching occurred. With data centers in 330 cities worldwide, Cloudflare provides the infrastructure relied upon by numerous popular applications for content delivery.
A 15-year-old security researcher named Daniel demonstrated the vulnerability by sending images to users and employing his custom tool, Cloudflare Teleport, to analyze where the images were cached. Using Burp Suite, Daniel extracted the image’s URL and sent requests to all of Cloudflare’s data centers to identify the one returning a “HIT” result. This indicated the nearest data center to the user, effectively revealing the target’s location with an accuracy of several hundred kilometers.
Experiments revealed that the attack could succeed even if the user did not open the message—in some instances, a push notification alone sufficed. Daniel tested the vulnerability on platforms like Signal, Discord, and X. For example, after sending an image, the attacker was able to pinpoint a Signal user’s approximate city location.
Cloudflare has confirmed that the vulnerability was resolved through its Bug Bounty program. A representative from Discord clarified that the issue stemmed from a third-party provider’s services. Signal emphasized that this CDN behavior does not compromise message encryption but recommended that activists and users requiring high levels of anonymity utilize tools such as VPNs, WireGuard, or Tor.
Daniel further noted that a similar attack could be executed through alternative methods. According to him, one could leverage specific tools to route traffic to various locations and subsequently send requests to Cloudflare’s data centers.