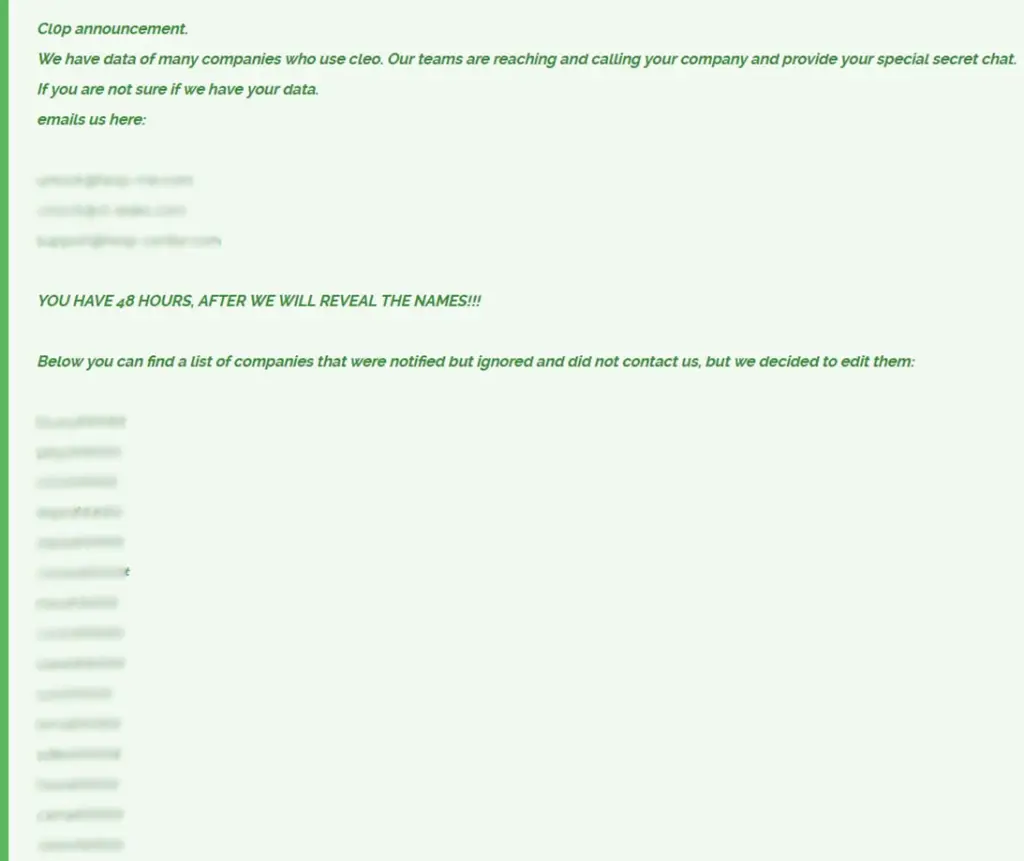
The ransomware group Clop has announced on its darknet portal the commencement of extortion targeting 66 companies impacted by a recent data breach involving Cleo products. The affected companies have been given a 48-hour deadline to respond to the group’s demands.
The attackers claim to be contacting victims directly, providing links to secure chatrooms for ransom negotiations. They have also shared email addresses through which companies can initiate contact on their own.
On Clop’s leak site, the names of some of the 66 companies have been partially revealed. Should these companies fail to respond within the stipulated 48 hours, the group has threatened to disclose their full names publicly.
Clop achieved this latest major breach by exploiting a zero-day vulnerability in Cleo’s LexiCom, VLTrader, and Harmony products. This vulnerability allowed attackers to infiltrate company networks and access sensitive data. Clop has previously used similar techniques in attacks on platforms such as Accellion FTA, GoAnywhere MFT, MOVEit Transfer, and SolarWinds Serv-U.
The vulnerability responsible for this breach, designated as CVE-2024-50623, permits unrestricted file uploads and downloads, ultimately enabling remote code execution. Cleo has since released updates for Harmony, VLTrader, and LexiCom (version 5.8.0.21), warning that hackers have already exploited the flaw to create reverse shells within compromised networks.
Huntress researchers have confirmed active exploitation of this vulnerability and have identified methods to bypass the released patch, presenting a proof-of-concept (PoC) exploit to validate their findings. Clop has acknowledged using CVE-2024-50623 in this campaign and stated that data from previous operations will be removed from their platform to focus entirely on this new wave of extortion.
According to Yutaka Seijiyama, a researcher at Macnica, the partially revealed company names could allow for the identification of certain victims by cross-referencing the data with owners of Cleo servers accessible online. While the exact number of affected organizations remains unclear, Cleo reports that its software is utilized by over 4,000 companies worldwide.
Once again, Clop has demonstrated how even rare, targeted attacks can inflict enormous damage. This operation serves as a striking example of how coordinated strikes can jeopardize hundreds of organizations simultaneously, leaving the global community in shock at the audacity and scale of such campaigns.