In the latest ClickFix campaigns, cybercriminals lure users onto counterfeit Google Meet pages, where they are presented with fake connection errors designed to spread malware capable of infecting both Windows and macOS systems.
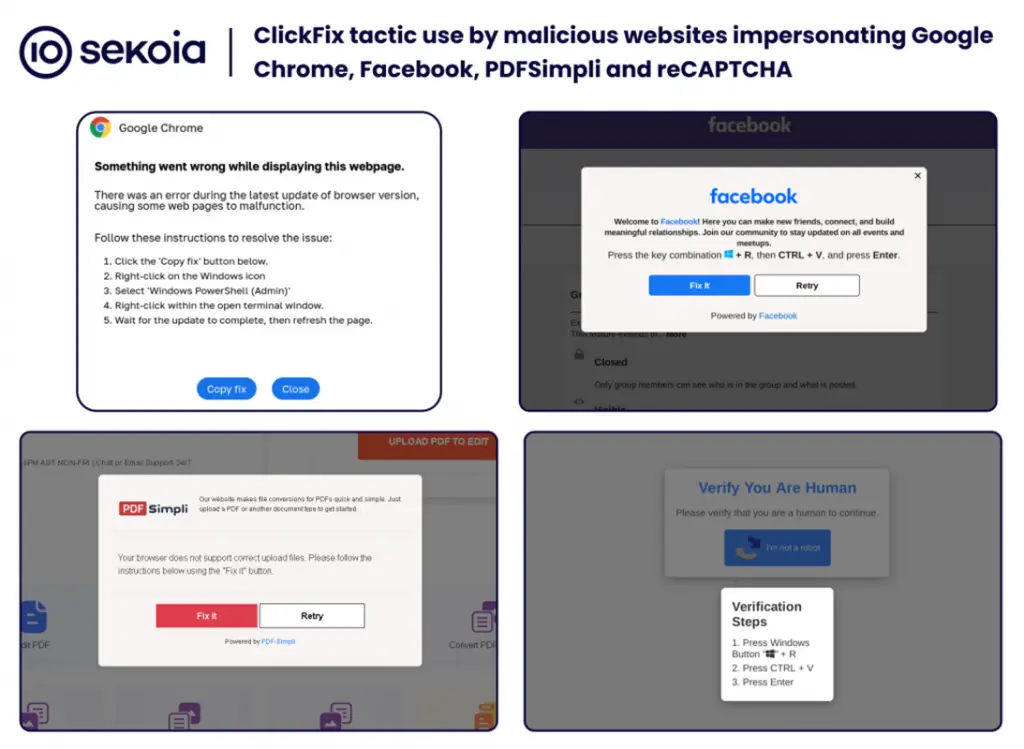
ClickFix emerged in May when Proofpoint first reported its use by the TA571 group. The attacks involved fraudulent error messages in Google Chrome, Microsoft Word, and OneDrive. Victims were prompted to insert PowerShell code into the command line to resolve an alleged issue, which ultimately led to the infection of their devices.
Through this method, malware such as DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, Lumma Stealer, and others were distributed. In July, McAfee noted a rise in the frequency of these attacks, particularly in the US and Japan.
According to a new report from Sekoia, ClickFix tactics have recently evolved: now, attackers use fake Google Meet invitations and send phishing emails targeting transportation and logistics companies. Among their new tricks are counterfeit Facebook pages and fake discussions on GitHub.
Sekoia also links recent campaigns to two groups—Slavic Nation Empire (SNE) and Scamquerteo—believed to be part of the cryptocurrency scam rings Marko Polo and CryptoLove.
The attacks using Google Meet are particularly convincing: the attackers send emails with counterfeit links mimicking official URLs:
- meet[.]google[.]us-join[.]com
- meet[.]google[.]web-join[.]com
- meet[.]googie[.]com-join[.]us
After visiting these pages, users are shown a message about a supposed problem with their microphone or headphones. Attempting to “fix” the issue activates the standard ClickFix script: a malicious PowerShell code is executed via the command line, downloading malware from the domain “googiedrivers[.]com”.
For Windows devices, Stealc or Rhadamanthys is downloaded, while on macOS, AMOS Stealer is installed in the “.DMG” format under the name “Launcher_v194.” Besides Google Meet, attackers are also using other platforms to spread malware, including Zoom, fake PDF readers, counterfeit video games, and web3 projects.


