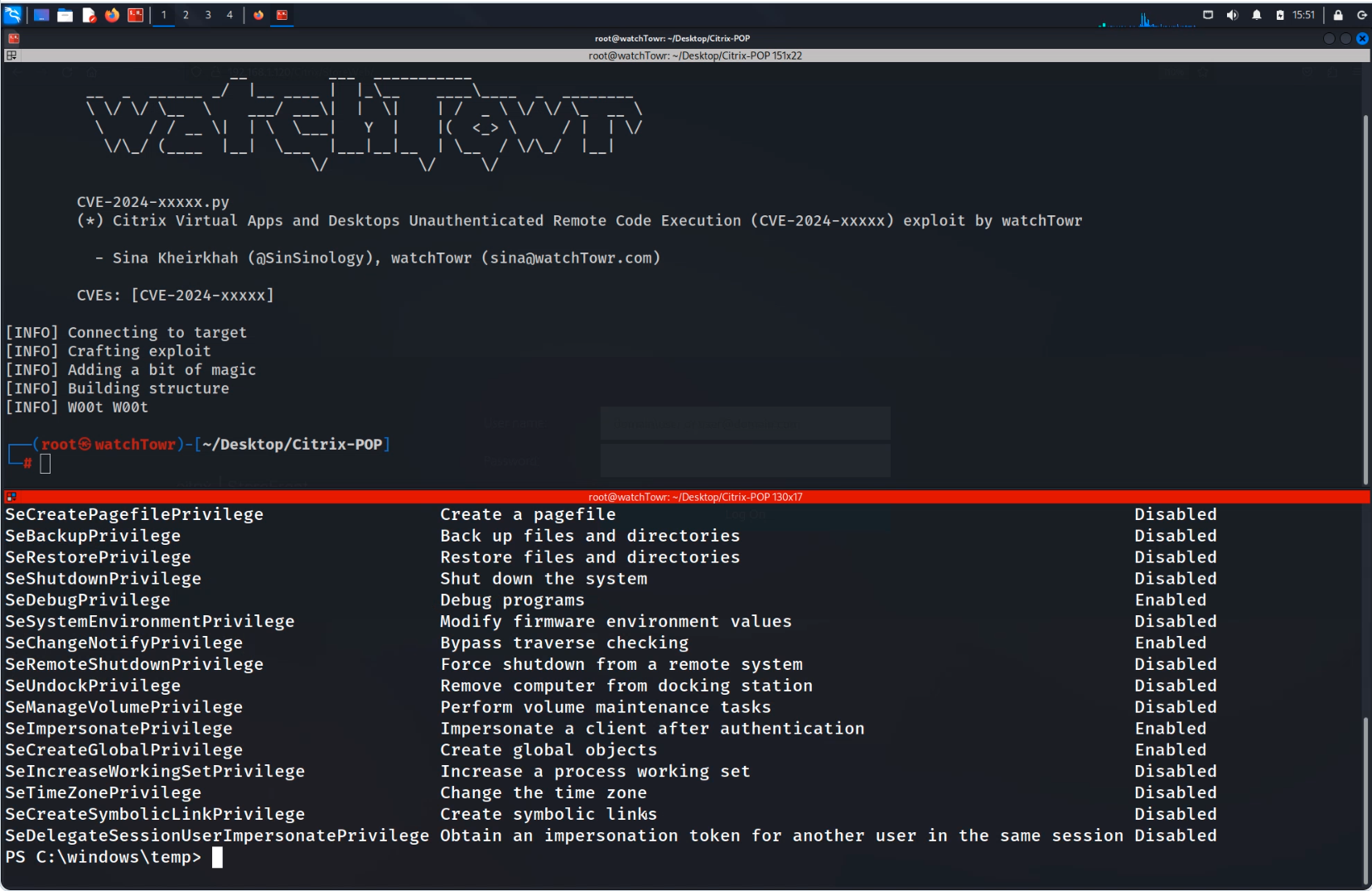
Specialists at watchTowr have released a proof of concept (PoC) demonstrating the exploitation of a remote code execution (RCE) vulnerability in Citrix Virtual Apps and Desktops. The flaw allows attackers to gain system privileges by sending a single HTTP request, potentially exposing Citrix’s virtual desktop infrastructure (VDI) to compromise.
While Citrix has already issued patches and urged users to apply them, the company maintains that the identified vulnerability is not an “unauthenticated RCE.” According to Citrix, exploitation requires an authenticated user operating with NetworkService-level access.
However, watchTowr disputes this assessment, arguing that the vulnerability is significantly more severe. It enables attackers to escalate their privileges to gain full system control over the server managing all applications and user sessions. This could allow malicious actors to impersonate users, including administrators, and monitor their activities covertly.
The vulnerability resides in the Session Recording Manager module, which captures video streams of user sessions, along with keystrokes and mouse movements, for monitoring and diagnostic purposes. These sessions are transmitted to a server and stored in a database using Microsoft Message Queuing (MSMQ).
Researchers discovered that the queue initialization process in MSMQ is configured with overly permissive access controls, allowing unauthorized insertion of messages. A more critical issue arises from the use of the outdated and insecure BinaryFormatter class for data deserialization. Microsoft’s documentation explicitly warns that BinaryFormatter is “unsafe and should not be used.”
The vulnerability can be exploited via a simple HTTP request, although MSMQ typically operates over TCP port 1801. Researchers were surprised to find that Citrix had enabled MSMQ over HTTP, a feature unnecessary for the product’s functionality.
Following the PoC’s publication, Citrix promptly issued recommendations and updates to mitigate the vulnerability. Patches address the following versions:
- Citrix Virtual Apps and Desktops (pre-2407): Hotfix 24.5.200.8
- Citrix Virtual Apps and Desktops 1912 LTSR (pre-CU9): Hotfix 19.12.9100.6
- Citrix Virtual Apps and Desktops 2203 LTSR (pre-CU5): Hotfix 22.03.5100.11
- Citrix Virtual Apps and Desktops 2402 LTSR (pre-CU1): Hotfix 24.02.1200.16
Citrix has assigned two CVE identifiers to the vulnerabilities:
- CVE-2024-8068 (CVSS score: 5.1): A privilege escalation vulnerability allowing access to a NetworkService account. Exploitation requires authentication within the same Active Directory domain as the session recording server.
- CVE-2024-8069 (CVSS score: 5.1): A limited RCE vulnerability requiring both NetworkService access and authentication within the victim’s internal network.
Citrix contends that additional conditions and authentication requirements significantly reduce the risks associated with these vulnerabilities. However, watchTowr maintains that their PoC demonstrates far more severe potential consequences.


