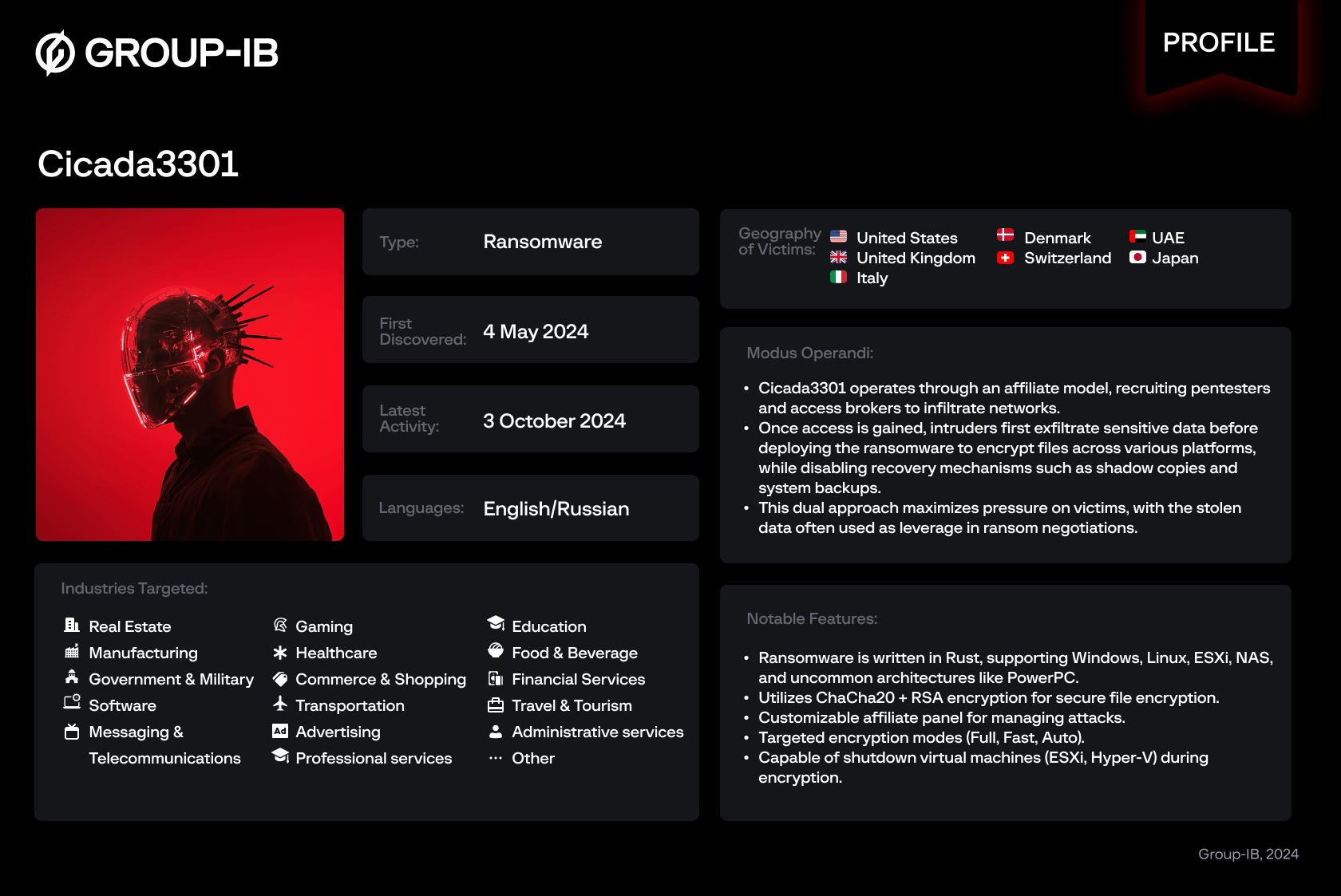
Cybersecurity researchers from Group-IB have unveiled new details about the hacker group Cicada3301, which operates under the RaaS (Ransomware-as-a-Service) model. The specialists gained access to the cyber gang’s affiliate panel on the dark web, allowing them to analyze its internal processes in detail.
Group-IB established contact with Cicada3301 via the cyber forum RAMP, using the Tox messenger, after the group posted an advertisement seeking new partners for its affiliate program.
Cicada3301 was first detected in June 2024. Researchers identified similarities in the group’s source code with the now-defunct ALPHV/BlackCat group. According to Group-IB, Cicada3301’s attacks have already impacted at least 30 organizations, primarily in critical sectors in the U.S. and the U.K.
The group’s malware is written in Rust and supports multiple platforms. It is capable of infecting devices running Windows and various Linux distributions, such as Ubuntu, Debian, CentOS, SUSE, and others, as well as ESXi and NAS systems.
Cicada3301 employs standard ransomware attack methods—file encryption, disabling virtual machines, terminating processes, deleting shadow copies, and encrypting network resources. These tactics make system recovery exceedingly difficult, thereby increasing pressure on victims.
One distinguishing feature of the group is its affiliate program, which attracts penetration testers and access brokers. Partners are offered a 20% commission and access to a web-based panel with extensive features. The panel includes sections for adding victims, conducting negotiations, and managing affiliate accounts.
For data encryption, Cicada3301 uses a combination of ChaCha20 and RSA algorithms and actively engages in data exfiltration prior to encryption to further intensify pressure on the affected entities.
According to experts, Cicada3301 has emerged as one of the most advanced threats in the modern ransomware landscape. Its sophisticated tactics and tools make its attacks both precise and destructive, positioning the group as a significant threat to organizations worldwide.


