A Taiwanese government-affiliated research institute fell victim to a cyberattack uncovered by Cisco Talos. The attack, which occurred in July 2023, resulted in the institute’s systems being infected with the ShadowPad malware and Cobalt Strike. Experts attribute this campaign to the hacker group APT41, which, according to American authorities, has ties to China.
Cisco Talos detected anomalous PowerShell commands connecting to an IP address to download and execute scripts. The ShadowPad malware exploited a vulnerable version of Microsoft Office IME to launch its loader. APT41 also created a custom loader to exploit the CVE-2018-0824 vulnerability, enabling local privilege escalation.
Researchers note that the methods and tools used align with those characteristics of APT41, including the use of ShadowPad, Bitdefender, and FileZilla. Although the final ShadowPad malware was not found, it is known that ShadowPad is exclusively used by Chinese hacker groups.
Cobalt Strike, discovered during the attack, was developed using the CS-Avoid-Killing loader, designed to evade antivirus detection. The loader, written in Go, contains strings in simplified Chinese, confirming the involvement of Chinese hackers.
During the attack, the perpetrators compromised three hosts in the target network and exfiltrated valuable documents. Hackers installed web shells and used RDP, and reverse shells to propagate the malware.
APT41 also employed tools for password collection, including Mimikatz and WebBrowserPassView. Hackers executed commands to obtain information about users, directory structures, and network configurations. For data exfiltration, the criminals compressed and encrypted files using 7zip before sending them to a command server.
The analysis of the campaign revealed two types of ShadowPad loaders. The first exploited an older version of Microsoft Office IME, while the second was developed using a vulnerable Bitdefender library. Both loaders utilized legitimate binary files to execute malicious code.
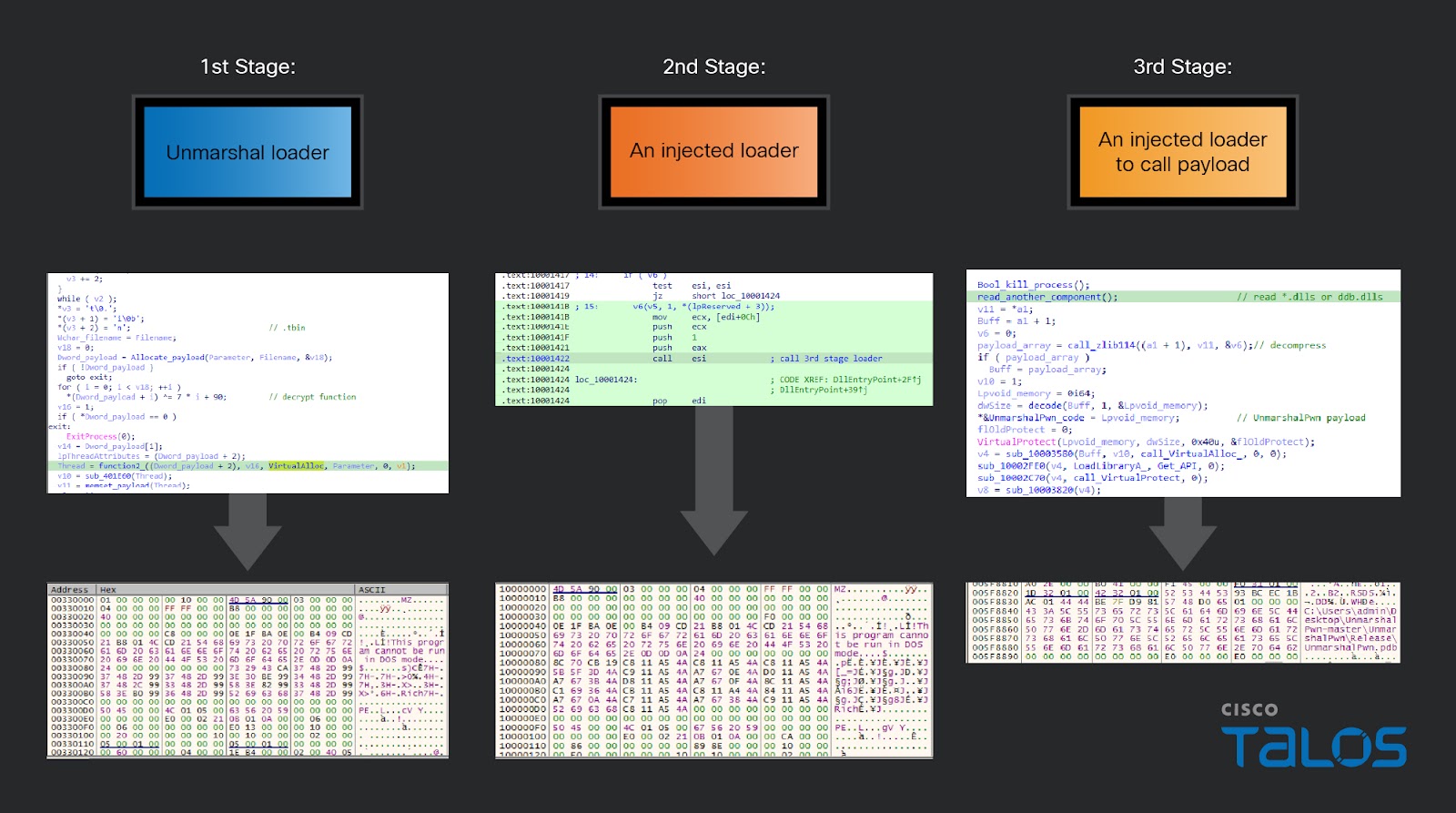
The investigation uncovered intriguing tools used by the hackers, including UnmarshalPwn to exploit CVE-2018-0824. Other components of the infrastructure used in different campaigns by the same hacker group were also identified.
The increasing sophistication of methods and tools employed by APT41 signals a growing threat to organizations worldwide. This incident underscores the critical necessity for companies and institutions to continually enhance their cybersecurity systems, regularly update software, and conduct vulnerability audits.


