A new Linux backdoor, dubbed WolfsBane, has been discovered, which researchers believe to be a port of Windows malware previously deployed by the China-based hacking group Gelsemium. Analysis reveals WolfsBane to be a sophisticated tool comprising a dropper, a loader, and a backdoor, augmented by a modified open-source rootkit to evade detection.
Additionally, another Linux malware variant, named FireWood, has been identified. It is linked to a Windows counterpart known as Project Wood. FireWood appears to be a shared tool employed by multiple Chinese APT groups rather than a proprietary creation of Gelsemium.
Experts have noted an increasing focus by hacker groups on Linux systems, driven by the growing security measures implemented on Windows platforms. These shifts are attributed to the widespread adoption of endpoint protection tools and the default disabling of VBA script execution, prompting threat actors to explore new attack vectors, including exploiting vulnerabilities in Linux environments.
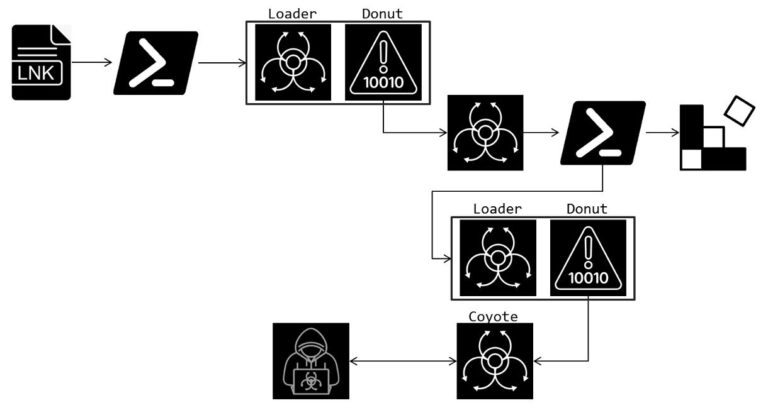
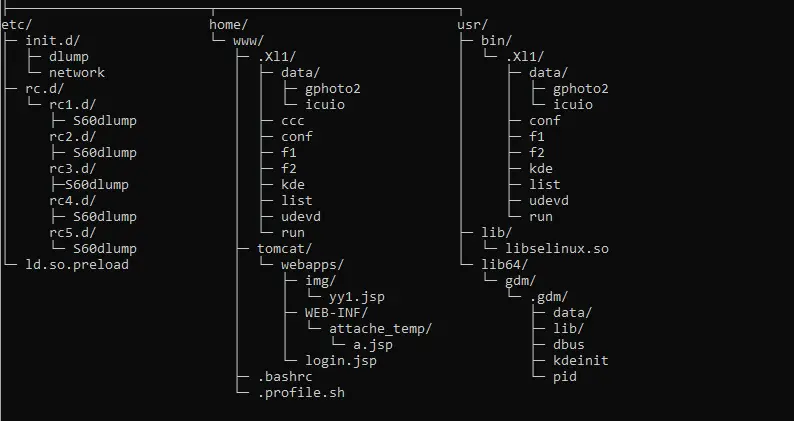
WolfsBane infiltrates targeted systems via a dropper named “cron”, masquerading as a KDE desktop component. Based on privilege levels, the dropper disables SELinux, modifies system configuration files, or creates service files to establish persistence. It then triggers a loader, which activates the malware by loading three encrypted libraries containing its core functionalities and command-and-control configuration.
For stealth, WolfsBane employs a modified BEURK rootkit, injected through the /etc/ld.so.preload file, enabling the concealment of processes, files, and network traffic. Its primary functions include executing commands from the command-and-control server, allowing attackers to manipulate files, exfiltrate data, and gain control over the system.
Though less explicitly tied to Gelsemium, FireWood is another formidable tool tailored for extended espionage campaigns. It provides operators with capabilities such as command execution, file operations, library loading and unloading, and process hiding through rootkit mechanisms. To ensure persistence, FireWood creates an autostart entry within the .config/autostart/ directory, executing commands upon system startup.
Both WolfsBane and FireWood underscore the concerted efforts of APT groups to broaden their operations to Linux platforms. A comprehensive list of Indicators of Compromise (IoCs) associated with these campaigns is available on GitHub.