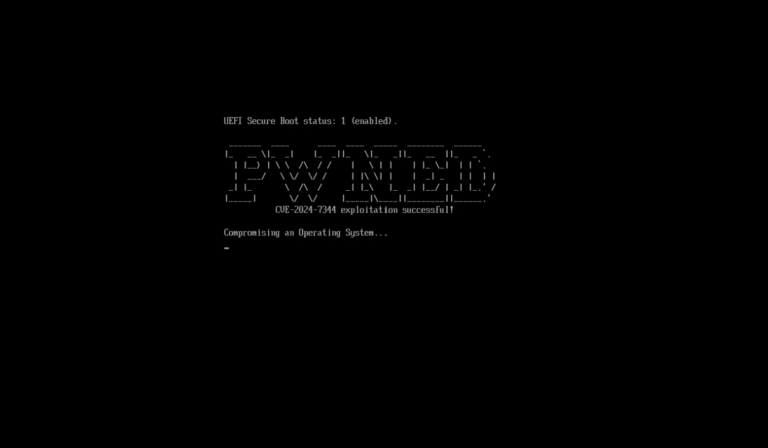
The CVE-2024-7344 vulnerability, associated with bypassing UEFI Secure Boot protection, presents a significant threat by enabling attackers...
Vulnerabilities
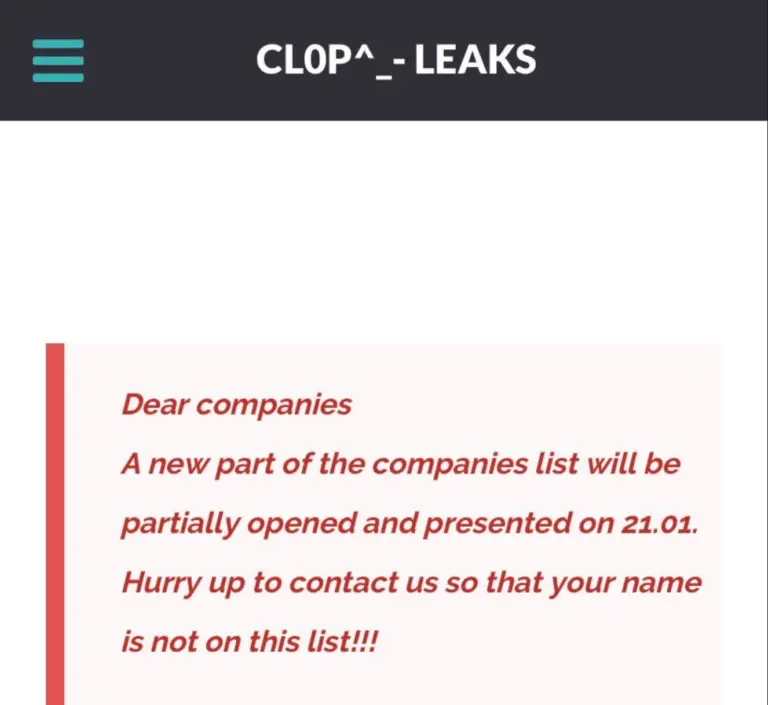
The Clop ransomware group has claimed responsibility for compromising the data of 59 companies by exploiting a...
Microsoft experts have conducted a comprehensive analysis of the security of over 100 company products using generative...
The Cybersecurity and Infrastructure Security Agency (CISA) has added a second vulnerability affecting BeyondTrust’s Privileged Remote Access...
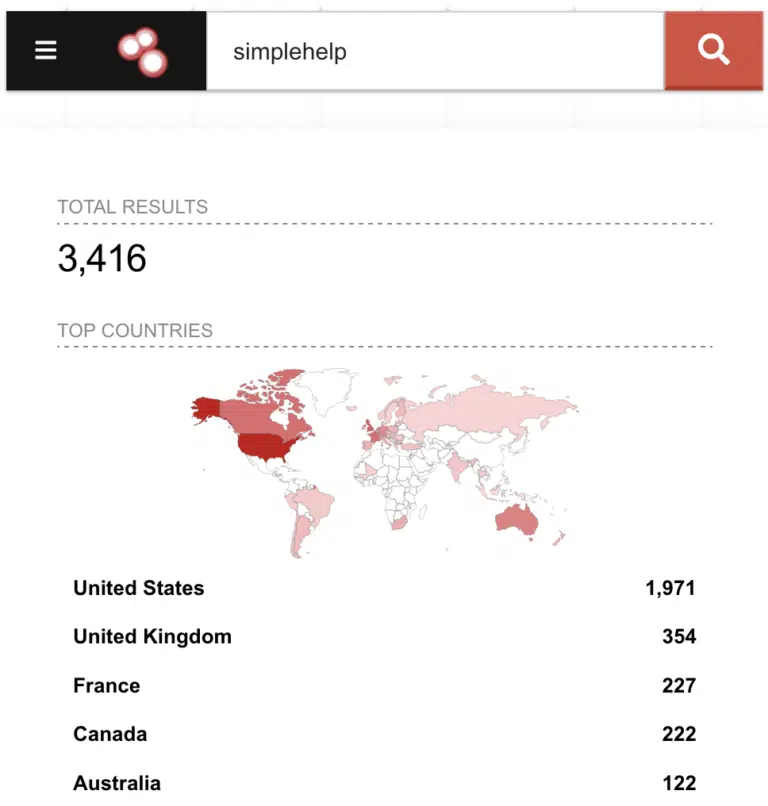
Researchers have disclosed three critical vulnerabilities in SimpleHelp, a widely-used remote support software. These vulnerabilities, identified as...
Six security vulnerabilities have been identified in Rsync, a widely-used file synchronization tool for Unix-based systems, some...
Cybersecurity experts have identified widespread exploitation of a critical vulnerability in Fortinet’s FortiGate firewalls. The manufacturer has...
Microsoft commenced 2025 with a comprehensive update, addressing 161 vulnerabilities in its software as part of its...
A vulnerability in the “Sign in with Google” authentication system has left millions of Americans at risk...
Researchers at Microsoft have uncovered a vulnerability in Apple macOS that enables the bypassing of System Integrity...
Researchers have uncovered a method to compromise the ACE3 USB-C controller, a proprietary component integral to Apple’s...
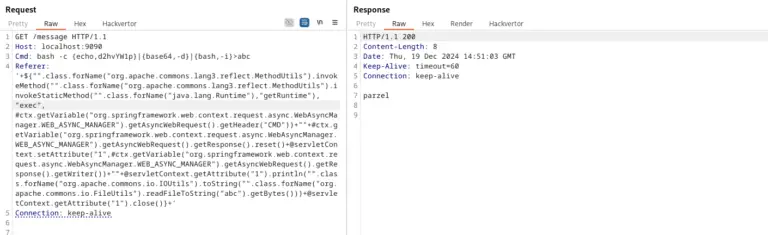
A security researcher demonstrated the exploitation of a Server-Side Template Injection (SSTI) vulnerability in Spring Boot 3.3.4...