In a new report, Group-IB highlights that the impact of ransomware attacks is set to intensify from 2024 onwards. The growing complexity of these attacks is driven by the development of the “Ransomware-as-a-Service” (RaaS) market, the proliferation of stolen data on specialized websites, and the increasing number of affiliate programs.
The most prominent trend in the ransomware landscape is the emergence of the DragonForce group, discovered in August 2023. Initially, the hackers exploited the leaked LockBit 3.0 code, and later, in July 2024, developed their own variant of the malware based on this leak. The group’s arsenal also includes a modified version of Conti with enhanced capabilities. A notable feature of DragonForce is its RaaS model, allowing affiliates to use ready-made software for attacks, receiving 80% of the ransom.
DragonForce’s tactics are built on the method of double extortion: after encrypting data, they threaten to publish the stolen information if the victim refuses to pay. Since June 2024, the group has launched an affiliate program on the underground forum RAMP, offering tools for attack management and automation, as well as the ability to create unique versions of the malware.
DragonForce actively employs the BYOVD (Bring Your Own Vulnerable Driver) technique, which allows them to disable security processes and evade detection. Additionally, the cybercriminals erase Windows event logs after data encryption, complicating subsequent incident analysis.
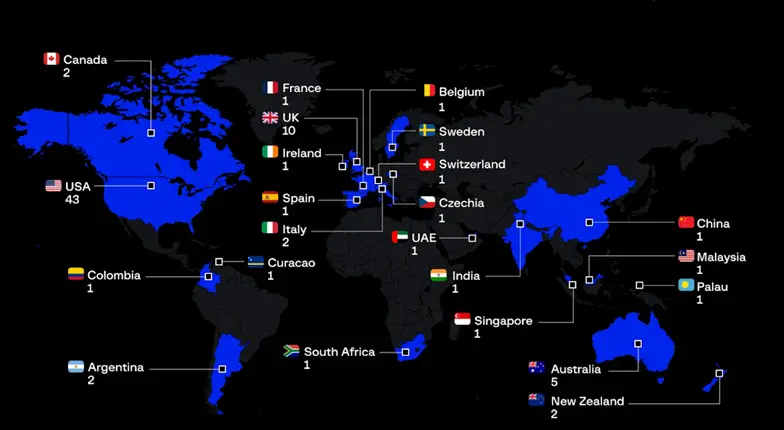
Between August 2023 and August 2024, the group targeted 82 companies across various industries, with manufacturing, real estate, and transportation being the most affected sectors. The majority of attacks were directed at the United States (52.4%), the United Kingdom (12.2%), and Australia (6%). Among the group’s past attacks are breaches of the Ohio state lottery systems and the government of Palau.
In addition to LockBit 3.0 and Conti, DragonForce uses other tools: the SystemBC backdoor to maintain persistence in the system, Mimikatz and Cobalt Strike to harvest credentials, and Cobalt Strike for lateral movement within networks.
Experts describe DragonForce as a “formidable adversary,” targeting key industries with advanced tools and tactics. While Group-IB has not yet linked DragonForce’s attacks to any specific country or group, previous research suggests the group may have originated in Malaysia.


