WHOIS Information Diagram of AS51381
The Knownsec 404 team has uncovered a vast network operated by the hosting provider ELITETEAM, which supplies infrastructure for cybercriminal activities. These services enable malicious actors to evade legal oversight while supporting malware operations, phishing sites, spam campaigns, and other illicit enterprises. Experts emphasize that “bulletproof” hosting providers pose a significant threat to global cybersecurity due to their operation in jurisdictions with weak legal frameworks and their resilience to law enforcement actions.
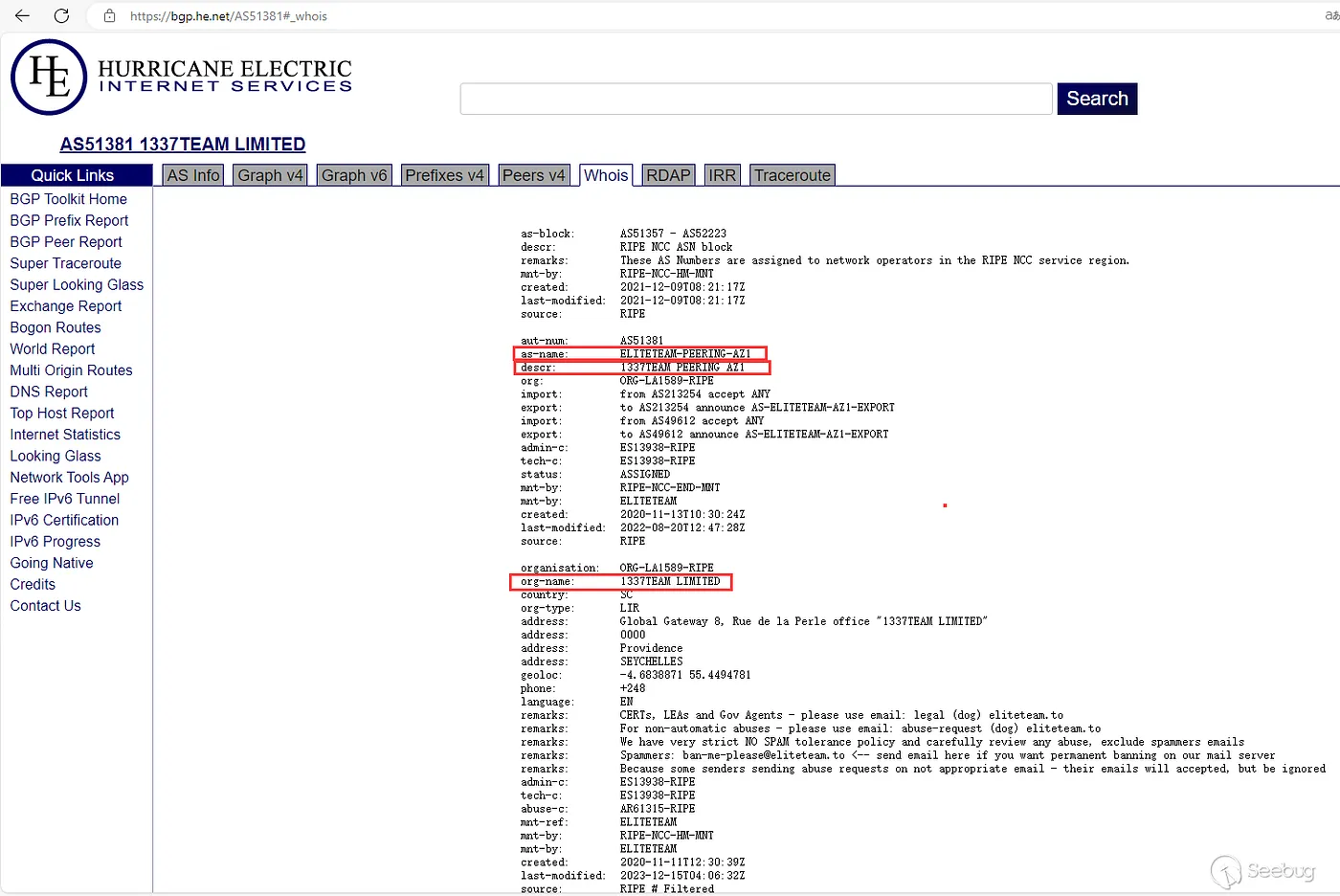
According to the report, ELITETEAM was registered in Seychelles in November 2020 under the name “1337TEAM LIMITED.” The provider owns the autonomous system AS51381 and offers services facilitating phishing sites, malware hosting, botnet command-and-control servers, and cryptocurrency scam infrastructure. Such providers deliberately choose jurisdictions with minimal regulatory oversight to shield their activities.
Research from Interisle on phishing networks in 2021 revealed that a single segment of ELITETEAM’s network, comprising 256 IP addresses, ranked eighth globally for malicious activity. VirusTotal flagged all 256 IPs as malicious, confirming their active role in cyberattacks. ThreatFox further identified multiple IPs in 2024 linked to Indicators of Compromise (IOCs) for malware such as Amadey and RedLine, demonstrating their involvement in phishing and malware distribution.
Cloudflare researchers discovered that ELITETEAM’s IP addresses are actively employed in attacks targeting WordPress sites. These assaults focus on login pages and XML-RPC interfaces, where attackers exploit vulnerabilities to gain unauthorized access to systems.
Trend Micro connected ELITETEAM’s infrastructure to the distribution of ransomware such as Quakbot and Emotet. In the first quarter of 2023 alone, over 200,000 instances of malicious traffic associated with ELITETEAM were detected, with 140,000 traced back to Seychelles. These ransomware campaigns were used to encrypt corporate networks’ data for extortion purposes.
The ELITETEAM infrastructure was also utilized to support cryptocurrency scams on the Hydra dark web marketplace, facilitating illegal transactions and money laundering. These activities drew the attention of Interpol, which has issued multiple investigative requests regarding the company’s operations.
An analysis of the 185.215.113.0/24 network segment via the ZoomEye platform revealed key characteristics: open ports for remote access (22/3389), web services (80/443), spam (25/465/587), and C2 servers (7766). Ten IP addresses in this segment had open mail ports, suggesting their use in spam campaigns. Unique SSL fingerprints and HTTP content further confirmed the network’s role in coordinating cyberattacks.
The study also linked the subnet 185.208.158.0/24 to ELITETEAM’s primary network. Of the 256 addresses in this subnet, 95 were flagged as malicious. Both networks are registered in Seychelles and share technical connections through common SSL certificates. Eight IPs across the two networks displayed identical SSL fingerprints between September and November 2024, indicating control by a single hacker group.
The detailed investigation identified five suspicious IP addresses: 185.208.158.114, 185.208.158.115, 77.91.68.21, 147.45.47.102, and 109.107.182.45. These were highlighted due to unique SSL certificate attributes and HTTP content. For instance, the SSL fingerprint C416E381FAF98A7E6D5B5EC34F1774B728924BD8 appeared in both the 185.208.158.0/24 subnet and ELITETEAM’s primary network.
Experts warn that the operations of such hosting providers create a safe haven for cybercriminals. Since 2015, the APT28 group has conducted over 80 attacks using bulletproof hosting services for phishing, data theft, and espionage. By situating their infrastructure in jurisdictions with lax regulations, these actors evade prosecution and sustain their activities over the long term.


