Researchers at SquareX have uncovered a sophisticated cyberattack technique known as “Browser Syncjacking,” which enables threat actors to seize control of a victim’s browser through what appears to be a harmless Chrome extension. Despite the technical complexity of the attack, it requires minimal user permissions and interaction—all the victim needs to do is install the malicious extension.
The attack begins with the creation of a corporate domain within Google Workspace, where attacker-controlled accounts are set up without two-factor authentication. This domain is then used to bind the victim’s profile to the attacker’s infrastructure.
The next phase involves publishing the malicious extension on the Chrome Web Store, disguised as a legitimate tool. Using social engineering tactics, the attacker lures the victim into installing the extension. Once installed, it silently authenticates the victim into one of the compromised Google profiles prepared in advance.
The extension then injects a deceptive message into Google’s support page, exploiting its read and write permissions. This message urges the victim to enable Chrome Sync, making it appear as a routine security measure. The moment the victim grants synchronization access, all of their saved credentials, browsing history, and other sensitive data are automatically transferred to the attacker.
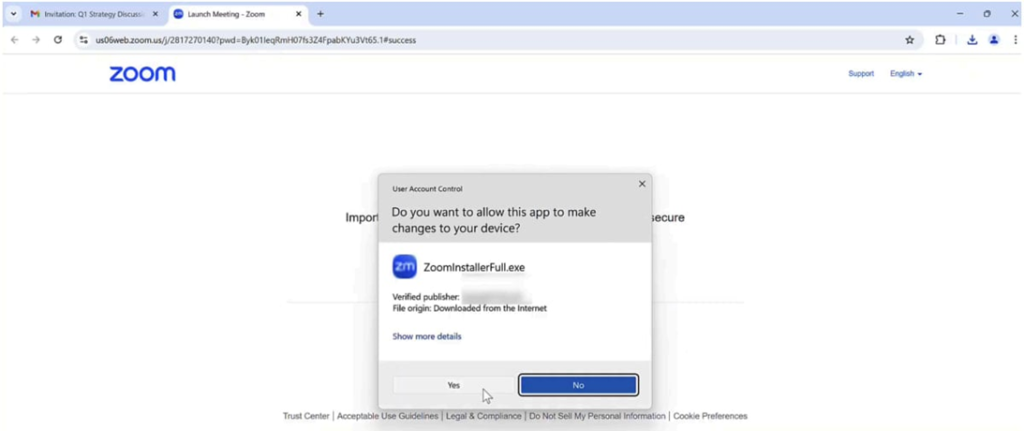
Once the profile is compromised, the attacker gains complete control over the browser through a variety of techniques. In one demonstration scenario, SquareX researchers showed how the malicious extension replaced Zoom’s update page, prompting users to download what appeared to be a new version of the Zoom client.
However, instead of a legitimate update, the victim downloads an executable file embedded with a registration token, which binds the device to the attacker-controlled Google domain, granting full access to the browser.
At this stage, the attacker can:
- Install and manage additional browser extensions;
- Redirect users to phishing sites;
- Log keystrokes to steal credentials;
- Upload, modify, or delete files on the device;
- Access the victim’s Google Drive;
- Remotely activate the webcam and microphone without the victim’s knowledge.
The only potential indicator of this compromise is a small notification in Chrome’s settings, displaying “Managed by your organization.” However, most users fail to notice or recognize the significance of this setting.
“Unless the victim is highly security-conscious or technically proficient enough to regularly inspect Chrome’s settings for managed browser indicators, there are virtually no visible signs that their browser has been hijacked,” the SquareX researchers explain.
Experts warn that this method of exploitation could become a powerful tool for cyber espionage and data exfiltration. Google has been notified of the vulnerability, but has yet to release an official statement or provide a security patch.