Sequence diagram of C2 via QR codes
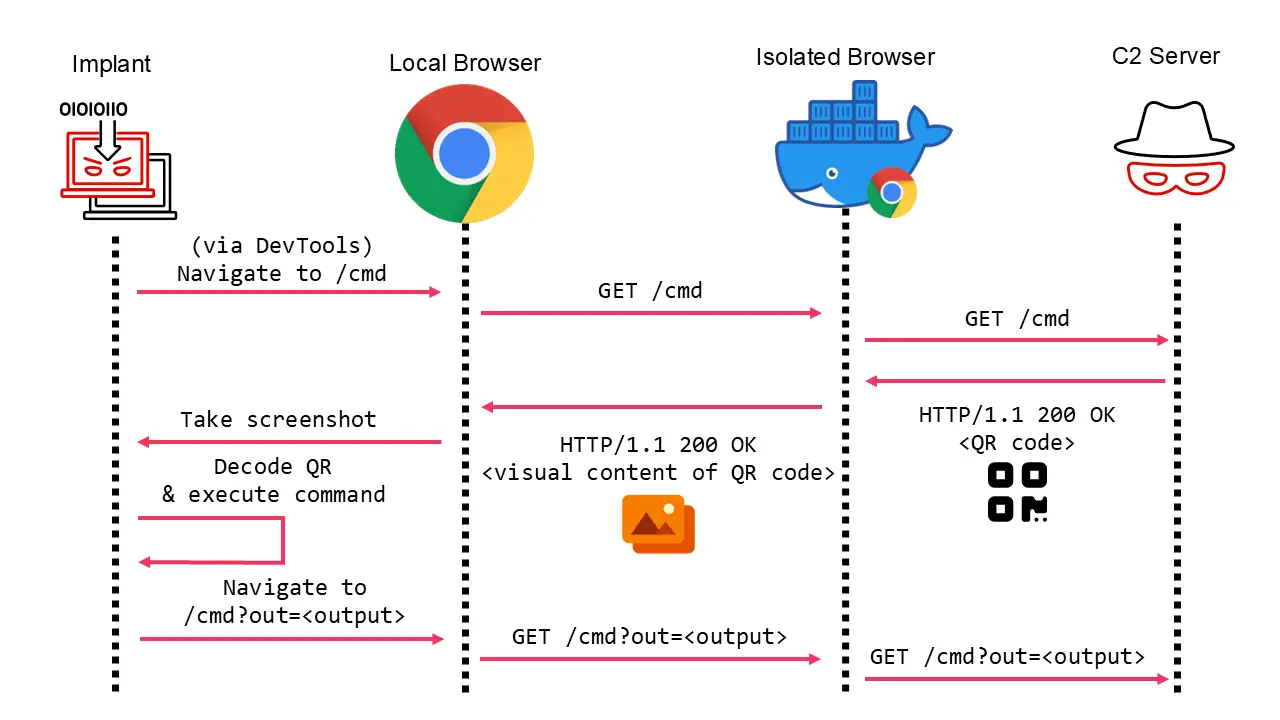
Experts at Mandiant have uncovered a novel method for bypassing browser isolation technologies, enabling attackers to establish command-and-control (C2) communications through the use of QR codes. This discovery highlights vulnerabilities within contemporary browser security systems.
Browser isolation technology is designed to enhance security by routing all local browser requests through remote browsers operating in cloud environments or virtual machines. Any code executed on visited websites runs remotely, transmitting only a visual representation of the webpage to the local device.
However, Mandiant identified a way to circumvent this safeguard. The new technique exploits QR codes to transmit commands. The visual rendering of a QR code on a webpage passes through browser isolation, allowing malware on an infected device to read and decode its contents.
Mandiant’s experiments demonstrated a successful bypass of protections in the current version of Google Chrome. Researchers utilized Cobalt Strike, a widely used penetration testing tool, to execute this attack.
The method, however, is not without its limitations. Firstly, the data payload of QR codes is capped at 2,189 bytes, complicating the transmission of large volumes of information. Secondly, high latency between requests renders the method relatively slow, with a transmission rate of approximately 438 bytes per second. This makes the technique unsuitable for large-scale attacks, such as SOCKS proxying.
Moreover, Mandiant emphasizes that additional security measures—such as domain reputation checks, URL scanning, and data leakage prevention—can effectively block this attack vector.
Despite these constraints, the threat remains significant. Administrators of critical systems are strongly advised to monitor anomalous traffic closely and implement detection mechanisms to identify automated browsers within their networks.


