Security researchers have identified a vulnerability in the RADIUS protocol, a cornerstone of modern network infrastructure. This flaw permits an attacker to access network devices and services without the need to guess passwords. The vulnerability has been named Blast-RADIUS.
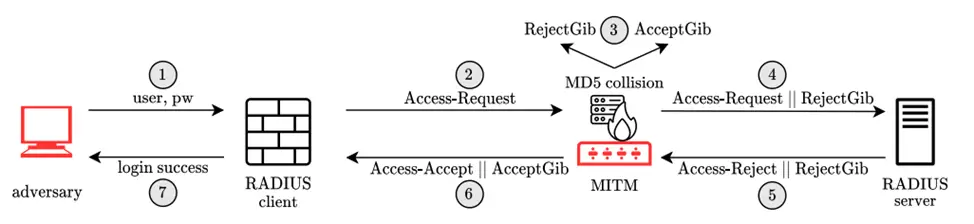
Blast-RADIUS (CVE-2024-3596) enables a Man-in-the-Middle (MiTM) attack by forging legitimate acceptance messages in response to failed authentication requests. Consequently, the attacker can gain access to network devices and services without the necessity of guessing passwords or shared secrets. Notably, user credentials remain unknown to the attacker.

The vulnerability affects all implementations of RADIUS using non-EAP authentication methods over the UDP protocol. This means all organizations employing RADIUS for network resource access management are at risk. These include large corporate networks, internet service providers, and telecommunications companies.
The RADIUS protocol, developed in 1991 for the dial-up internet era, continues to be the standard authentication protocol for remote access to network devices. RADIUS is supported by almost all switches, routers, access points, and VPN concentrators sold in the last 20 years.
In the protocol, the NAS server verifies user credentials via queries to a central server. The RADIUS client and server use a shared secret for data exchange. The server responds with an acceptance (Access-Accept) or rejection (Access-Reject) message. Requests and responses may include various parameters, such as username and password.
The primary cause of the vulnerability lies in the fact that the RADIUS protocol was developed before modern cryptographic standards emerged and is typically neither properly encrypted nor authenticated. The protocol attempts to authenticate server responses using the MD5 hash function and a fixed shared secret between the client and server.
The Blast-RADIUS attack exploits the protocol’s new vulnerability by combining it with an MD5 chosen-prefix collision attack and several novel speed and space enhancements. The attacker injects a malicious Proxy-State attribute into the client’s request, ensuring its return by the server in the response. This mechanism allows the attacker to ensure that the Response Authenticator values in the legitimate and forged responses match. Consequently, the NAS grants access to network devices and services without the need to guess passwords or secrets.
The attack is based on the MD5 vulnerability, which allows hash collisions to be computed. The attacker uses random strings so that the MD5 hashes for these strings match. Then, the attacker appends the strings to the client’s request, and the server returns them in the response.
Network administrators using RADIUS are strongly advised to check for patches from their vendors and follow configuration recommendations for RADIUS. Currently, end-users cannot take independent steps to protect themselves.
Developers and vendors are also advised to mandate that clients and servers always send and require Message-Authenticator attributes for all requests and responses. For Access-Accept or Access-Reject responses, the Message-Authenticator should be included as the first attribute. Patches with these mitigations have been implemented by all known RADIUS implementations.
Long-term mitigation involves using RADIUS within an encrypted and authenticated channel that offers modern cryptographic security guarantees. For example, the IETF has initiated work on standardizing RADIUS over (D)TLS.


