ThreatFabric researchers have recently detected the activity of a new Android malware targeting banking users in Brazil. Security experts have identified this emerging threat as Rocinante, a sophisticated type of banking Trojan capable of seizing control of the victim’s device and stealing their data.
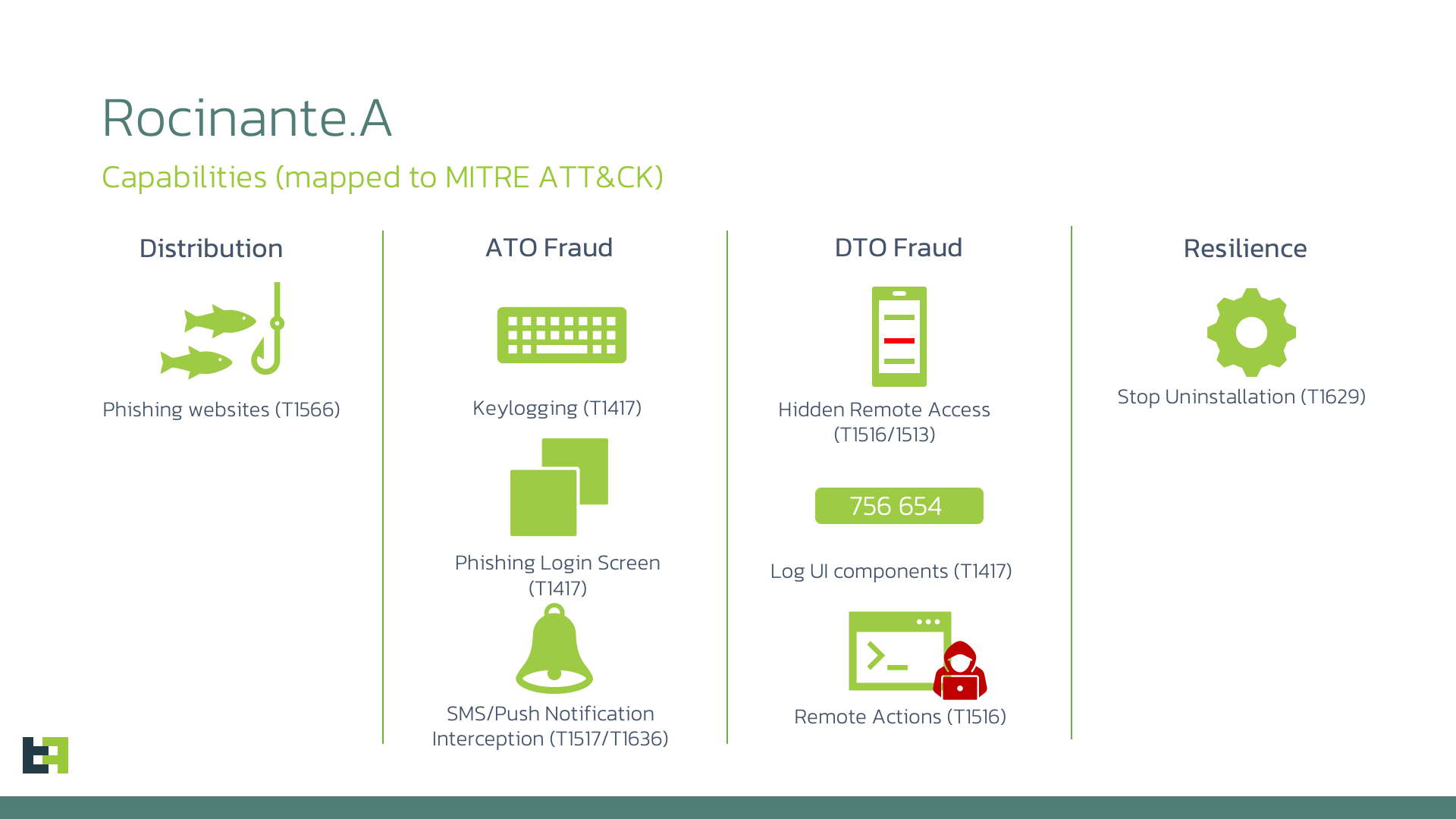
Rocinante, named after Don Quixote’s horse, is developed using advanced technologies that enable it to intercept input data, mimic banking app interfaces, and gain full access to the device by exploiting Android’s accessibility service privileges. The malware actively employs phishing screens to harvest sensitive information, which is then transmitted to the attackers.
Despite its unique characteristics, Rocinante is often confused with another infamous spyware—Pegasus. While the name Pegasus is used by the creators of Rocinante for internal purposes, this malware is not connected to the well-known spyware tool from NSO Group, which is designed for surveillance of journalists, activists, and political figures. The primary distinction of Rocinante lies in its focus on financial gain through the compromise of banking data from users in Brazil.
Rocinante spreads through phishing sites that offer malicious APK files disguised as legitimate banking or security applications. Once the user grants the app the necessary permissions, the malware begins to log all actions on the device and transmit the captured data to the attackers’ servers.
A notable feature of Rocinante is its ability to dynamically alter its attack targets, allowing the same malicious code to be used against different financial institutions depending on the region. However, in the case of Brazil, the list of targets is hardcoded and includes the country’s largest banks, such as Bradesco, Itaú, and Banco do Brasil.
Moreover, Rocinante integrates code from another notorious malware—Ermac—indicating the interest of Brazilian cybercriminals in leveraging the work of their international counterparts. Yet, despite these borrowings, Rocinante retains its uniqueness and danger, continuing to evolve and adapt to local conditions.
With its capabilities for keylogging, phishing, and remote access, Rocinante poses a significant risk to banking customers, as their confidential financial data, including account numbers, passwords, and transaction details, can be compromised. Armed with this information, attackers can initiate unauthorized transfers and drain bank accounts.
Additionally, the remote access feature allows attackers to maintain continuous control over the device, monitor activities, and potentially manipulate transactions in real-time, further escalating the financial risk for unsuspecting customers.
Experts warn of the need for increased caution when downloading applications and recommend verifying the authenticity of software before installation. It is crucial to remember that attackers are constantly seeking new ways to deceive users, and Rocinante is just one example of how modern cyber threats can evolve and adapt to various environments.


