GitHub is being exploited to disseminate the Lumma Stealer under the guise of fake patches, posted as comments in various projects.
This campaign was reported by a member of the teloxide library. In the discussions of the developer’s GitHub project, five comments appeared that masqueraded as fixes but were spreading malicious software.
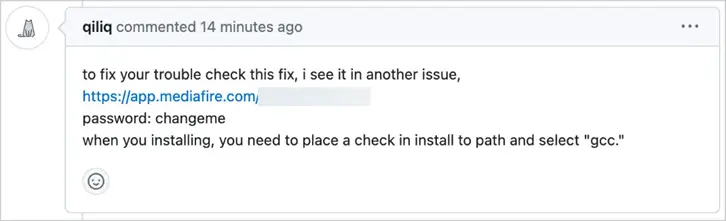
Further analysis revealed that similar comments had been left in thousands of other GitHub projects. All the comments contained “solutions” to problems, urging users to download a password-protected archive from “mediafire.com” or a shortened link via “bit.ly” and run the executable file inside. In every case, the password for the archive was the same—”changeme.”
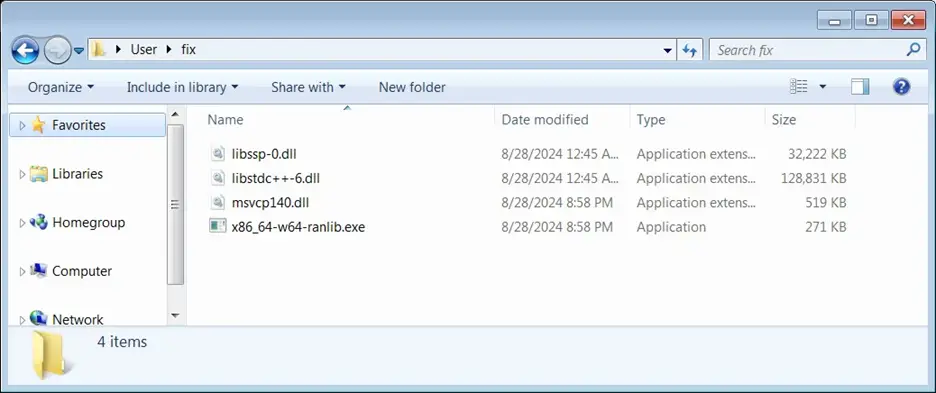
According to reverse engineer Nicholas Sherlock, more than 29,000 comments with malicious links were posted within three days. When users followed the link, they were directed to a download page for a file named “fix.zip,” which contained several DLL files and an executable file named “x86_64-w64-ranlib.exe.” Running the executable on Any.Run resulted in the activation of the Lumma Stealer malware.
Lumma Stealer is an advanced information-stealing malware that, upon execution, attempts to pilfer cookies, credentials, passwords, credit card data, and browsing history from Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium-based browsers.
Additionally, the malware is capable of stealing cryptocurrency wallets, private keys, and text files with names like seed.txt, pass.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, words, wallet.txt, as well as files with .txt and .pdf extensions, as they may contain private keys and passwords. The collected data is archived and sent to the attackers, who can use it for further attacks or sell it on cybercriminal markets.
Despite efforts by GitHub staff to remove such comments, many users have already fallen victim to the attack. Those who inadvertently executed the malware are advised to immediately change the passwords on all their accounts, using unique passwords for each site, and transfer their cryptocurrency to a new wallet.
In July, Check Point Research reported a similar campaign orchestrated by the group Stargazer Goblin, which used over 3,000 fake GitHub accounts to spread a stealer as part of a Distribution-as-a-Service (DaaS) scheme. However, it remains unclear whether these two campaigns are connected or if they were conducted by different groups.


