A new strain of Android malware, dubbed Octo2—a refined iteration of Octo (ExobotCompact)—is proliferating across Europe. According to experts at ThreatFabric, this new version may profoundly alter the cybersecurity landscape.
Octo2 represents an evolution of malware favored by cybercriminals, disseminated through the Malware-as-a-Service (MaaS) model. This iteration boasts augmented capabilities for remote manipulation of victims’ devices and employs novel obfuscation techniques, including Domain Generation Algorithms (DGA), enabling it to circumvent security measures and evade detection.
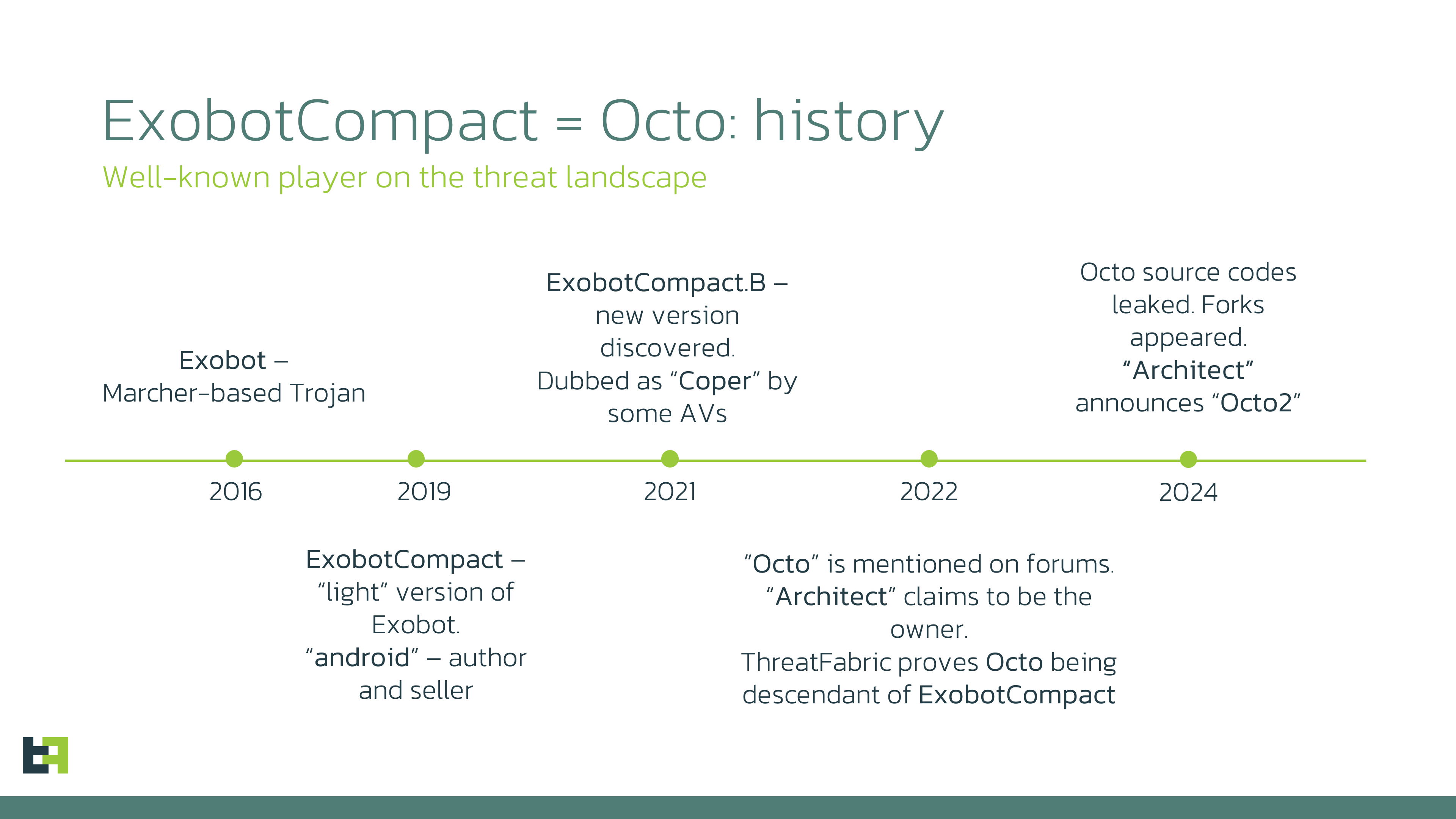
The Exobot family initially surfaced in 2016 as a banking Trojan adept at executing overlay attacks and intercepting calls and messages. In 2019, a streamlined version known as ExobotCompact emerged, followed by its enhanced variant, Octo, in 2021. This particular iteration laid the groundwork for subsequent developments.
In 2022, Octo became a focal point of discussion among cybercriminals on clandestine forums. Since that time, the malware’s activity has escalated, eventually being deployed across multiple regions globally, encompassing Europe, the United States, and Asia.
The pivotal development in 2024 pertains to the leakage of Octo‘s source code, culminating in the advent of several program forks. Nonetheless, the most formidable threat emanates from the original Octo2, crafted by the progenitor of Octo and disseminated among previous users of the initial version.
Octo2 has been endowed with substantial enhancements, notably the augmentation of remote device control stability and the introduction of techniques to circumvent analysis and detection systems. Moreover, Octo2 integrates a mechanism enabling the interception and concealment of push notifications from victims’ devices, thereby depriving users of critical alerts. This development imperils a vast array of mobile applications, as malefactors can effortlessly redirect data and execute fraudulent activities.
Initial campaigns employing Octo2 have been documented in nations such as Italy, Poland, Moldova, and Hungary. The malware camouflages itself as renowned applications like Google Chrome and NordVPN, thereby facilitating its surreptitious penetration of users’ devices.
In the observed campaigns, the Zombinder service functions as the initial installation phase: upon execution, Zombinder prompts the installation of an additional “plugin,” which is, in reality, Octo2, thereby adeptly circumventing the constraints of Android 13+.
A cardinal feature of Octo2 is the incorporation of a novel Domain Generation Algorithm (DGA), empowering the malware to dynamically alter its command and control (C2) servers. This development hampers the efforts of researchers and antivirus firms, as new domains are generated autonomously, rendering them more arduous to block.
Additionally, Octo2 employs a new data encryption system for transmissions to command servers, utilizing a dynamic key for each request, thereby fortifying its defenses against analysis and detection.
Considering its augmented remote access capabilities and stealthiness, Octo2 constitutes a grave threat to mobile users, particularly those utilizing banking applications. The malware can imperceptibly execute fraudulent transactions directly on the victim’s device, rendering it one of the most perilous mobile Trojans.


