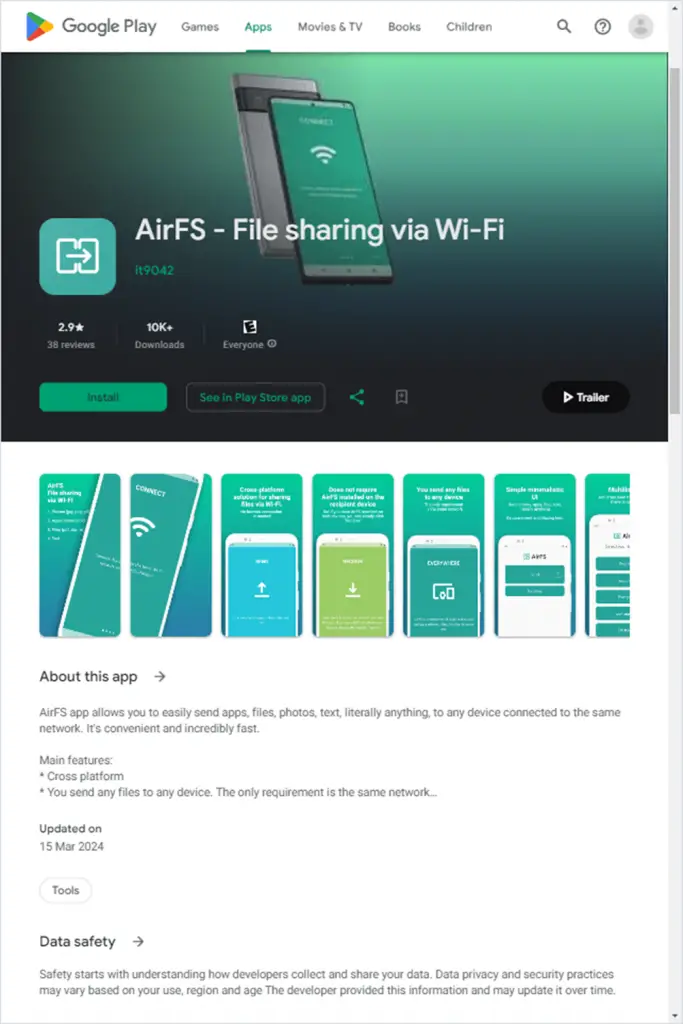
Recently, researchers from Kaspersky Lab reported a new version of the Mandrake spyware, which has infiltrated Google Play through five completely different applications uploaded back in 2022, using enhanced methods of concealment and evasion of security systems.
Mandrake was first documented by Bitdefender in 2020. At that time, the malware surprised experts, as it had successfully hidden in Google Play for four years before being detected.
Below is the list of malicious applications discovered by Kaspersky Lab. Notably, the most popular of these was only removed by Google in March of this year:
- AirFS — 30,305 downloads (from April 2022 to March 2024);
- Astro Explorer — 718 downloads (from May 2022 to June 2023);
- Amber — 19 downloads (from February 2022 to August 2023);
- CryptoPulsing — 790 downloads (from November 2022 to June 2023);
- Brain Matrix — 259 downloads (from April 2022 to June 2023).
The majority of downloads of these infected applications occurred in Canada, Germany, Italy, Mexico, Spain, Peru, and the United Kingdom.
Unlike most Android malware that places malicious logic in the app’s DEX file, Mandrake hides its initial stage in the native library “libopencv_dnn.so,” heavily obfuscated using OLLVM.
Upon installing the application, this library exports functions to decrypt and load the second stage from the DEX file. In the second stage, the app requests permissions to display overlays and loads a second native library, “libopencv_java3.so,” which decrypts the certificate for secure communication with the command server.
After establishing contact with the server, the application sends the device profile and receives the main Mandrake component if the device is suitable. Once activated, the spyware can perform a wide range of malicious actions, including data collection, screen recording, command execution, user gesture simulation, file management, and application installation.
The new version of Mandrake includes advanced evasion techniques, such as checking for the presence of Frida, a popular tool among security analysts, checking the device’s root status, and verifying if the system partition is mounted as read-only.
Android users are advised to install applications only from trusted publishers, check reviews before installation, avoid granting suspicious permissions, and ensure that Google Play Protect is activated on their devices. Google Play Protect is continually improved and automatically protects users from known versions of various spyware, warning or blocking apps with suspicious behavior.


