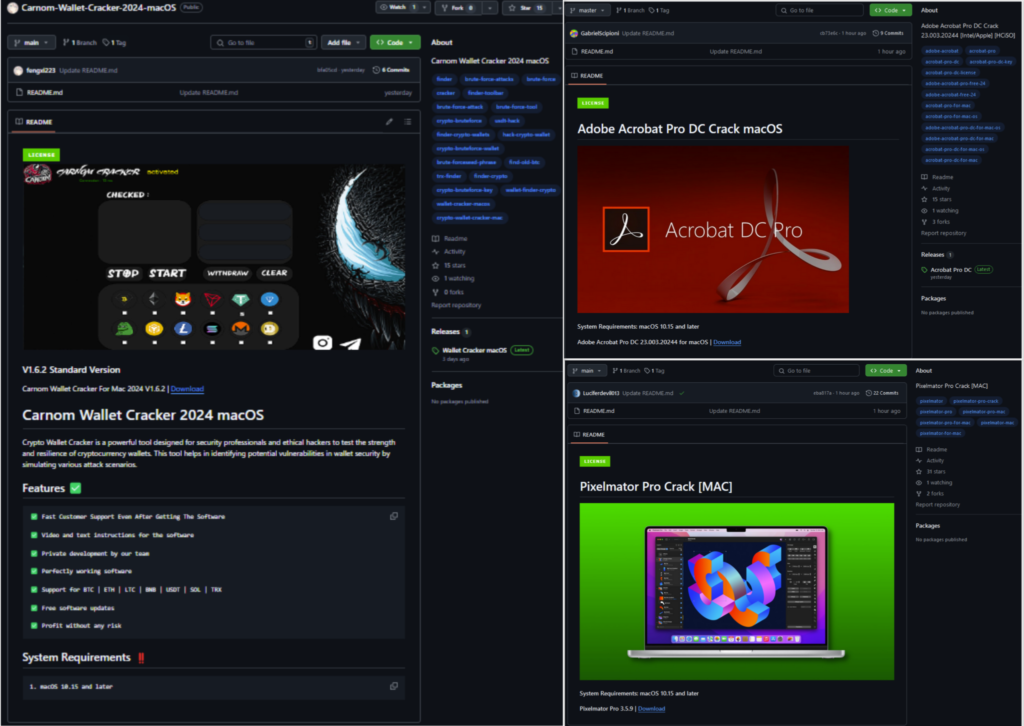
Repositories from first campaign
In recent months, researchers at Check Point have been monitoring a new iteration of the Banshee malware, specifically targeting macOS users. This information stealer is adept at exfiltrating browser data, cryptocurrency wallet credentials, and other sensitive information from devices. A notable feature of the update is its use of string encryption inspired by XProtect, macOS’s built-in antivirus system.
Banshee is distributed through phishing websites and malicious repositories on GitHub, masquerading as popular applications. The attackers have also leveraged the Windows-focused Lumma Stealer to broaden their campaigns.
Until November 2024, this “stealer-as-a-service” platform was priced at $3,000 and was actively promoted on Telegram and forums such as XSS and Exploit. However, a source code leak forced its creator to cease operations, though updated versions of the malware continue to circulate among cybercriminals.
To evade detection, the malicious code employs process forking, mimics system services, and operates discreetly in the background. Its targets include browsers like Chrome, Brave, Edge, and Vivaldi, as well as extensions for cryptocurrency wallets and two-factor authentication. Additionally, the malware tricks users into entering their passwords via system-like pop-up windows to steal critical credentials.
Banshee’s focus on macOS systems highlights a shift in priorities for cybercriminals. Historically considered secure due to its Unix architecture and lower market share, macOS is becoming increasingly attractive as its user base expands.
From September to November, Banshee remained undetected by antivirus software, enabling attackers to execute successful campaigns. Although the subsequent disclosure of its source code led to improved detection rules, it also heightened the risk of new forks emerging.
GitHub repositories played a pivotal role in the malware’s distribution. Malicious campaigns were executed in three waves starting in October, with infected files disguised as installers for popular applications like Telegram and TradingView. Some websites employed user operating system detection to ensure only macOS users were served the malicious payload.
Experts caution that macOS users should not rely solely on built-in security features. Regular updates, vigilance when clicking links, and the use of robust antivirus solutions remain crucial defenses. Moreover, increasing awareness of contemporary threats is essential to minimizing the risk of cyberattacks.


