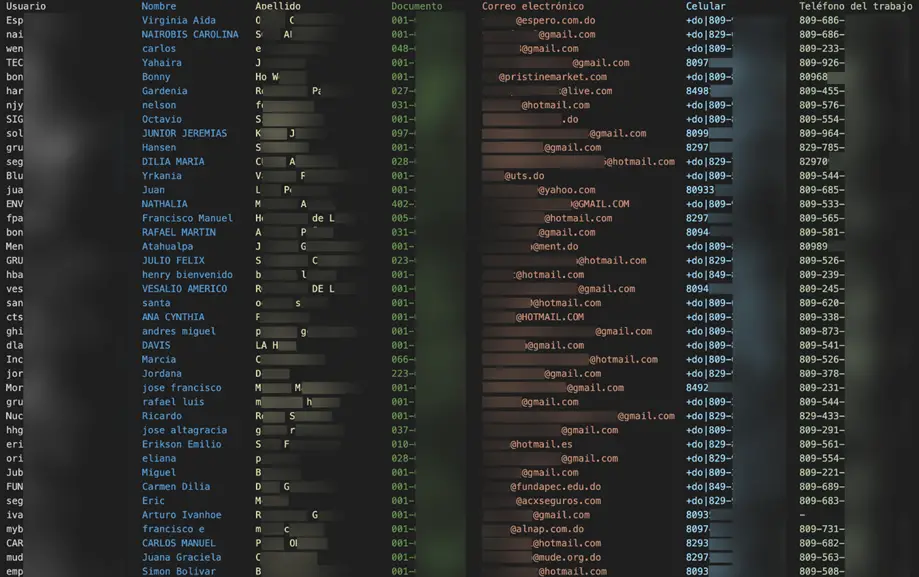
The online banking platform Bankingly suffered a data breach affecting seven financial institutions, impacting customers across Central and South America.
On May 24, the Cybernews team discovered seven Azure Blob Storage repositories that lacked the necessary authentication. Due to this vulnerability, the personal information of nearly 135,000 clients in Latin America was exposed.
The breach impacted residents of the Dominican Republic, Mexico, Ecuador, El Salvador, Bolivia, and Costa Rica. Notably, the majority of those affected—approximately 100,000—are citizens of the Dominican Republic.

Bankingly is a fintech platform that provides web services and mobile applications for financial institutions in Latin America. Based in Uruguay, the company primarily serves small to medium-sized banks, credit unions, and microfinance organizations, most of which are located in rural regions of Latin America.
Bankingly utilized the storage repositories to hold client data, including personal information and banking credentials, enabling financial organizations to offer software solutions.
The compromised data includes:
- Full names;
- Usernames for financial applications;
- Email addresses;
- Phone numbers;
- Work phone numbers.
The affected institutions include:
- “San Martín de Porres” (COSMART);
- “La Nacional de Ahorros y Préstamos” (ALNAP);
- Caja Buenos Aires;
- Caja Mitras;
- Coac Puellaro;
- Credecoop;
- AMC.
The concern extends beyond reputational damage to the financial organizations involved. The breach also poses significant risks to the security of customer data. Although the exposed information does not grant direct access to financial transactions, it could serve as the foundation for carefully crafted phishing attacks.
Typically, more sensitive information—such as identification details, social security numbers, or passwords—is required for such operations. Nonetheless, the availability of personal data increases the risk of phishing and social engineering attacks. For instance, fraudsters could send emails purporting to be from the victim’s bank or make phone calls impersonating bank representatives to deceitfully obtain more personal information or credentials.
Another potential risk involves “credential stuffing” attacks, in which criminals use already compromised accounts to access other platforms if clients reuse the same passwords.
As of now, Bankingly’s vulnerability has been addressed, and access to the databases has been sealed. However, the company has not yet provided an official statement. Cybernews has also reached out to the affected financial institutions and is awaiting their responses.


