A group of European researchers has uncovered a vulnerability in AMD’s Secure Encrypted Virtualization (SEV) mechanism, designed to protect virtual machines. The experts demonstrated that the system’s defenses could be bypassed using equipment costing as little as $10. Their findings will be presented at the IEEE Symposium on Security and Privacy in 2025.
SEV encrypts the memory of virtual machines to safeguard it against unauthorized access. The updated SEV-SNP version, which includes protections against memory remapping attacks, was also scrutinized. The results revealed a flaw that enables attackers to circumvent the protection and access sensitive data.
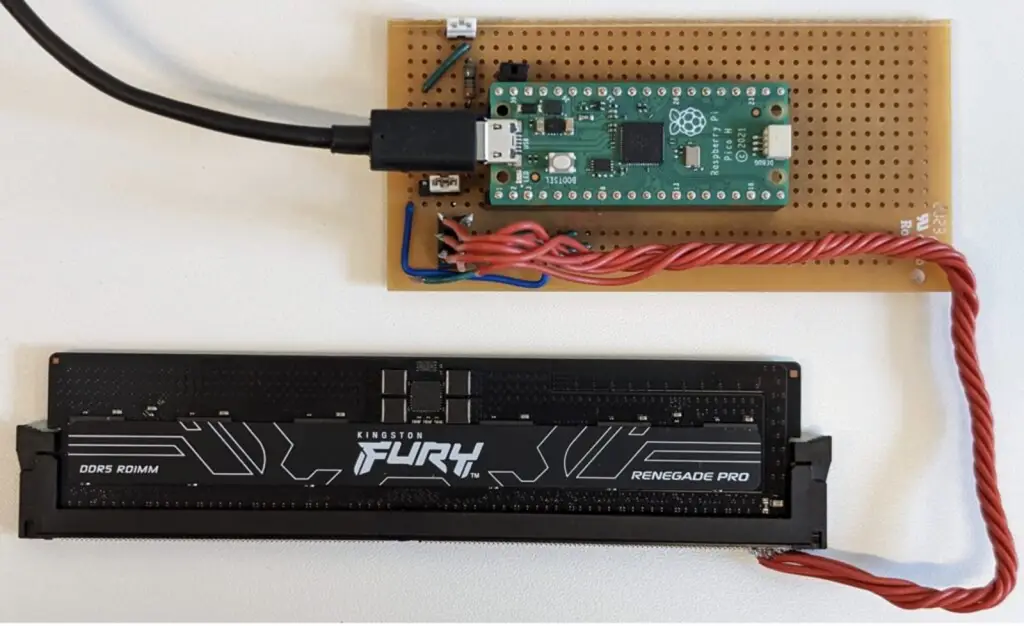
The attack exploits manipulation of the Serial Presence Detect (SPD) chip embedded in DDR4 and DDR5 memory modules. This chip provides basic information about memory modules to the system during boot. The technique, dubbed BadRAM, allows the SPD chip to supply false data about available memory, creating so-called “phantom” addresses. These addresses grant access to protected memory regions that SEV-SNP is designed to secure.
Conducting the attack requires only inexpensive hardware, such as a Raspberry Pi, costing less than $10. The device is briefly connected to the SPD chip to alter memory data. In some cases, the attack can even be executed through software alone, significantly increasing its threat level.
Once the SPD chip is modified, “phantom” memory addresses are created, which the system fails to recognize as protected. An attacker can reconfigure the operating system to bypass these addresses while retaining access to actual data. For instance, in Linux, the memmap kernel parameter can be manipulated to make the compromised addresses appear legitimate within the system.
Certain memory modules, such as DDR4 from Corsair, remain vulnerable due to the lack of built-in SPD protection. Even older modules like DDR3 can be exploited through SPD manipulation. The vulnerability affects AMD’s highly secure Epyc 7003 processors, widely used in cloud services such as Amazon AWS, Google Cloud, and Microsoft Azure. By contrast, solutions from Intel (SGX, TDX) and Arm (CCA) are immune to similar attacks thanks to integrated countermeasures.
BadRAM enables attackers to access sensitive data, such as cryptographic hashes that verify the integrity of virtual machines (VMs). By altering these hashes, an attacker can compromise the VM’s boot process and covertly install backdoors, gaining full access to the encrypted memory of the VM.
The researchers disclosed the vulnerability to AMD on February 26 and released a proof-of-concept (PoC). AMD is tracking the issue under CVE-2024-21944 (CVSS: 5.3) and AMD-SB-3015. The company has confirmed the vulnerability and recommended using SPD-protected memory modules, maintaining physical security of systems, and applying firmware updates to mitigate the risk.


