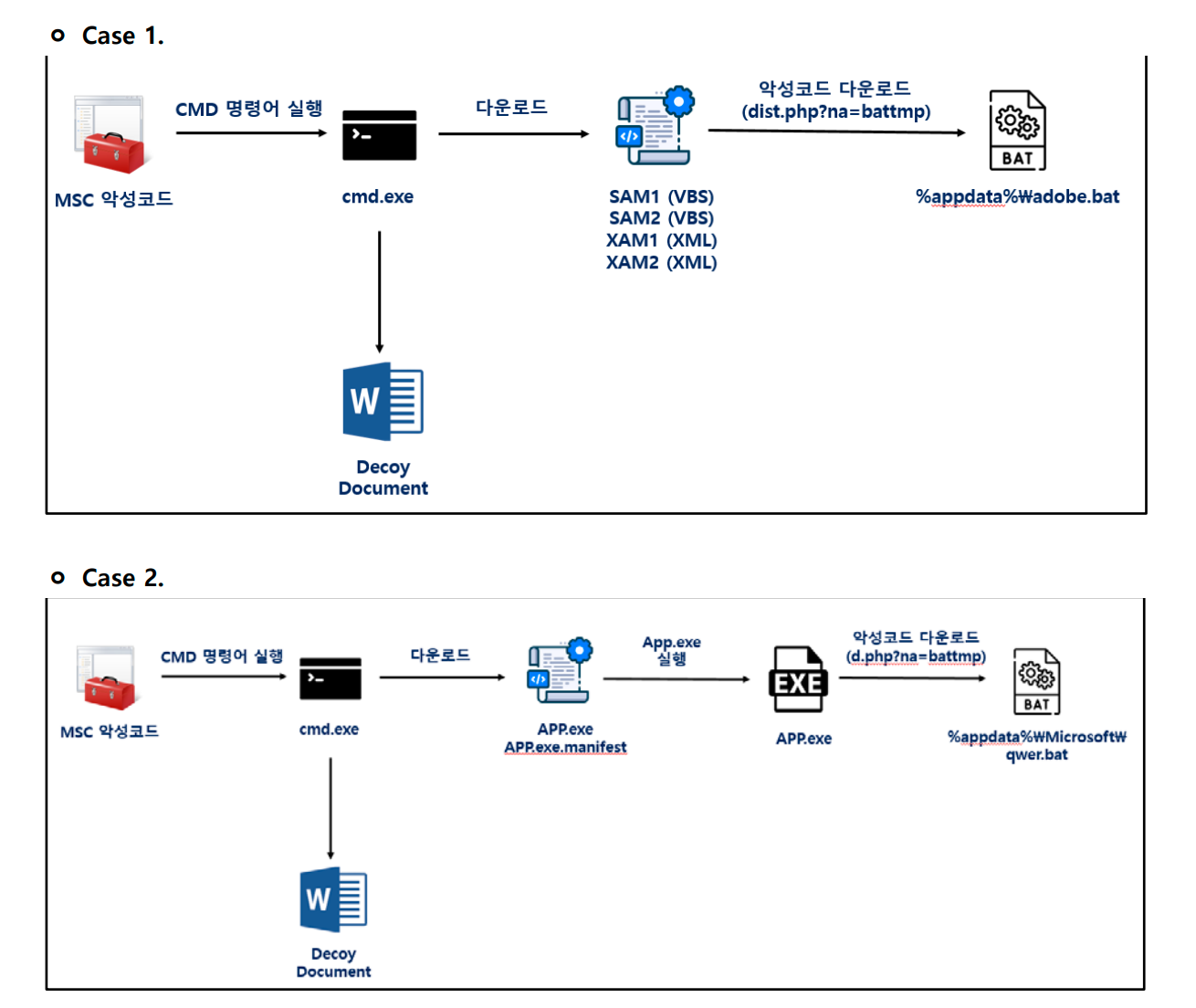
The North Korean hacker group Kimsuky continues to escalate its operations, employing increasingly sophisticated techniques to bypass security systems. Since 2018, the group’s malicious campaign, code-named BabyShark, has shown a constant evolution: where the attackers once used HWP and BAT files to distribute malicious code, they have now shifted to utilizing Microsoft Management Console (MSC) files and executing malicious code via the VbsEdit program.
The primary threat lies in the fact that MSC files, typically used for system administration, have become tools for disseminating malware. When such a file is launched, the user is prompted to click “Open,” which triggers malicious commands through the command line (CMD). These commands download malware from remote servers and disguise it as ordinary files, such as Google documents.
Particular attention from Hauri’s researchers was drawn to an incident where a downloaded document contained information about specific North Korean defectors, indicating a targeted attack. The attackers also employ VBS scripts, which, once executed via VbsEdit, connect to C2 servers to download and run additional malicious programs.
Kimsuky’s attacks have become even more intricate through the use of VbsEdit scripting software, allowing the attackers to evade standard detection methods, such as “wscript.exe” and “cscript.exe.” The use of VbsEdit to execute malicious code makes it more difficult for traditional antivirus solutions to detect.
A noteworthy aspect is the method of storing and executing the malware. Files downloaded from C2 servers are masked as harmless XML or VBS files and then registered in the Windows Task Scheduler to execute at precisely specified times. In some cases, the download of additional malware occurs through encrypted commands, further complicating their analysis and detection.
Given the complexity and targeted nature of these attacks, Hauri security experts strongly recommend that organizations bolster their system protection measures, paying particular attention to suspicious activity in the task scheduler and any unauthorized changes to system files.


