Overview of CDK attack vector
Cybersecurity researchers have discovered a vulnerability in Amazon Web Services (AWS) Cloud Development Kit (CDK) that, under certain conditions, can lead to account takeover. According to a report from Aqua Security released recently, the issue enables attackers to gain administrative access to a target AWS account, allowing for full control over the account.
CDK is an open-source framework for defining cloud resources using Python, TypeScript, or JavaScript, and deploying them via CloudFormation. The vulnerability is tied to the use of predictable naming patterns for IAM roles and S3 buckets.
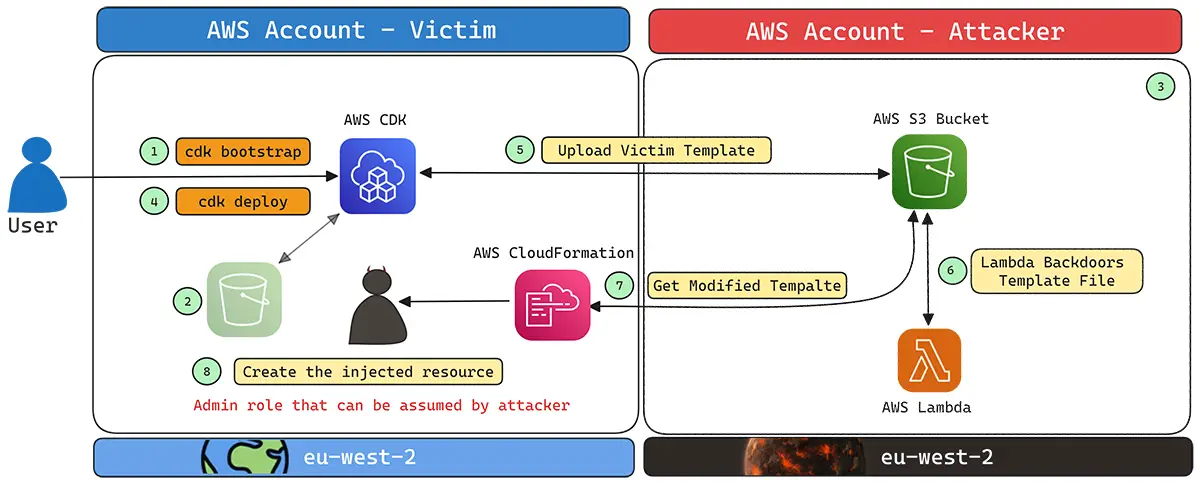
Aqua experts noted that the widespread use of the default identifier “hnb659fds” when creating S3 buckets during the bootstrapping process makes it possible for attackers to preemptively claim these buckets. This enables a type of attack known as “Bucket Sniping,” where the attacker creates an S3 bucket with the expected name before the user, thereby blocking access to the resource.
If a bucket is accidentally deleted and then recreated by an attacker with the same name, CDK may trust this bucket and use it for data reads and writes, allowing malicious CloudFormation templates to be injected. In such a scenario, the attacker could deploy resources with administrative privileges.
The vulnerability was patched in CDK version 2.149.0, released in July 2024, following notification of the issue on June 27. AWS noted that approximately 1% of CDK users were affected by this vulnerability.
The fix ensures that data is uploaded only to buckets owned by the account that initiated the bootstrapping. Additionally, users are advised to avoid using default identifiers and instead opt for unique identifiers for their buckets.
AWS has also urged users to update CDK to the latest version and re-run the bootstrapping command to mitigate the risk. As an added security measure, users are encouraged to configure IAM policies with restrictions on file uploads.


