The APT-C-60 group, known as “Pseudo-Hunters,” continues to conduct cyber-espionage campaigns targeting government institutions, businesses, and cultural organizations in South Korea.
Cybersecurity experts at the 360 Advanced Threat Research Institute first detected APT-C-60’s activity in 2018, yet retrospective analysis indicates that the group has been carrying out attacks since at least 2014. The primary objectives of these threat actors are covert surveillance of compromised systems and the exfiltration of sensitive data.
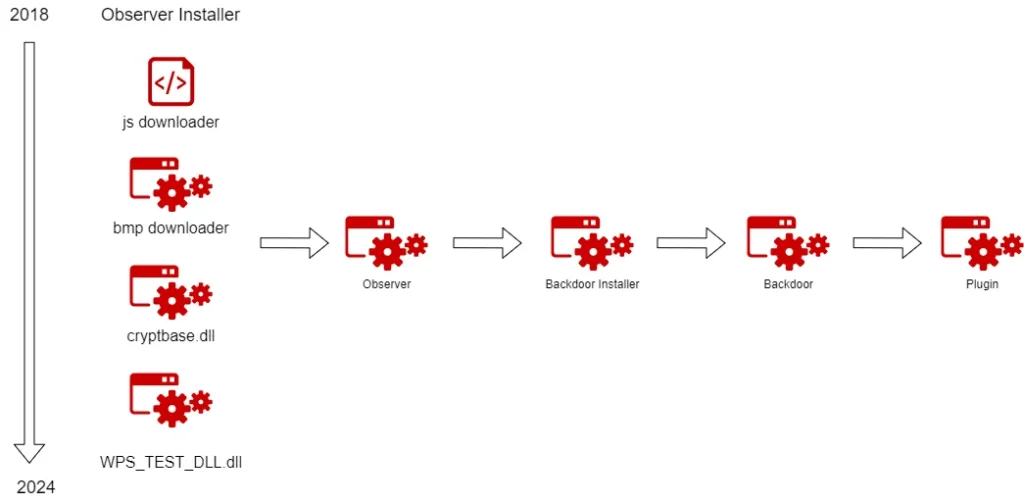
Over the past six years, researchers have analyzed thousands of malicious samples, identifying significant evolution in the group’s attack arsenal. The tools employed by APT-C-60 can be categorized into five distinct components:
- Observer Installer
- Observer
- Backdoor Installer
- Backdoor
- Plugin
These elements facilitate initial system infiltration, persistence, data collection, and remote command execution.
- Observer Installer serves as the initial infection vector, deploying malicious payloads while ensuring stealthy execution within the system. Until 2023, the group primarily relied on JavaScript (JS) and BMP-based loaders, but in the past year, it has adopted new evasion techniques to enhance threat resilience.
- Observer is a reconnaissance module responsible for collecting system information and transmitting it to the attackers, who then determine whether to escalate the attack. Analysis of Observer versions from 2018 to 2024 reveals continuous improvements in data harvesting, encryption methodologies, and anti-detection techniques.
- Backdoor Installer and Backdoor provide long-term control over compromised systems. Installation occurs covertly through system file manipulation and advanced encryption methods. These components support core functionalities, including information gathering, remote command execution, process management, and file exfiltration.
- Plugins expand the malware’s capabilities, enabling keystroke logging, screenshot capture, file extraction, and even the deployment of additional exploits within the system.
As APT-C-60 has evolved, so have its methods of obfuscating malicious code. In 2018, the group primarily relied on standard AES encryption, whereas by 2024, its preferred techniques include complex XOR algorithms, modified Base64 encoding, and steganographic payload delivery via BMP files.
Despite ongoing cybersecurity advancements, APT-C-60 remains a highly active and technically adept player in the cyber-espionage landscape. Experts strongly advise organizations to enhance their cybersecurity posture, implement behavioral threat analysis, and routinely update defensive mechanisms to counteract such evolving threats.


