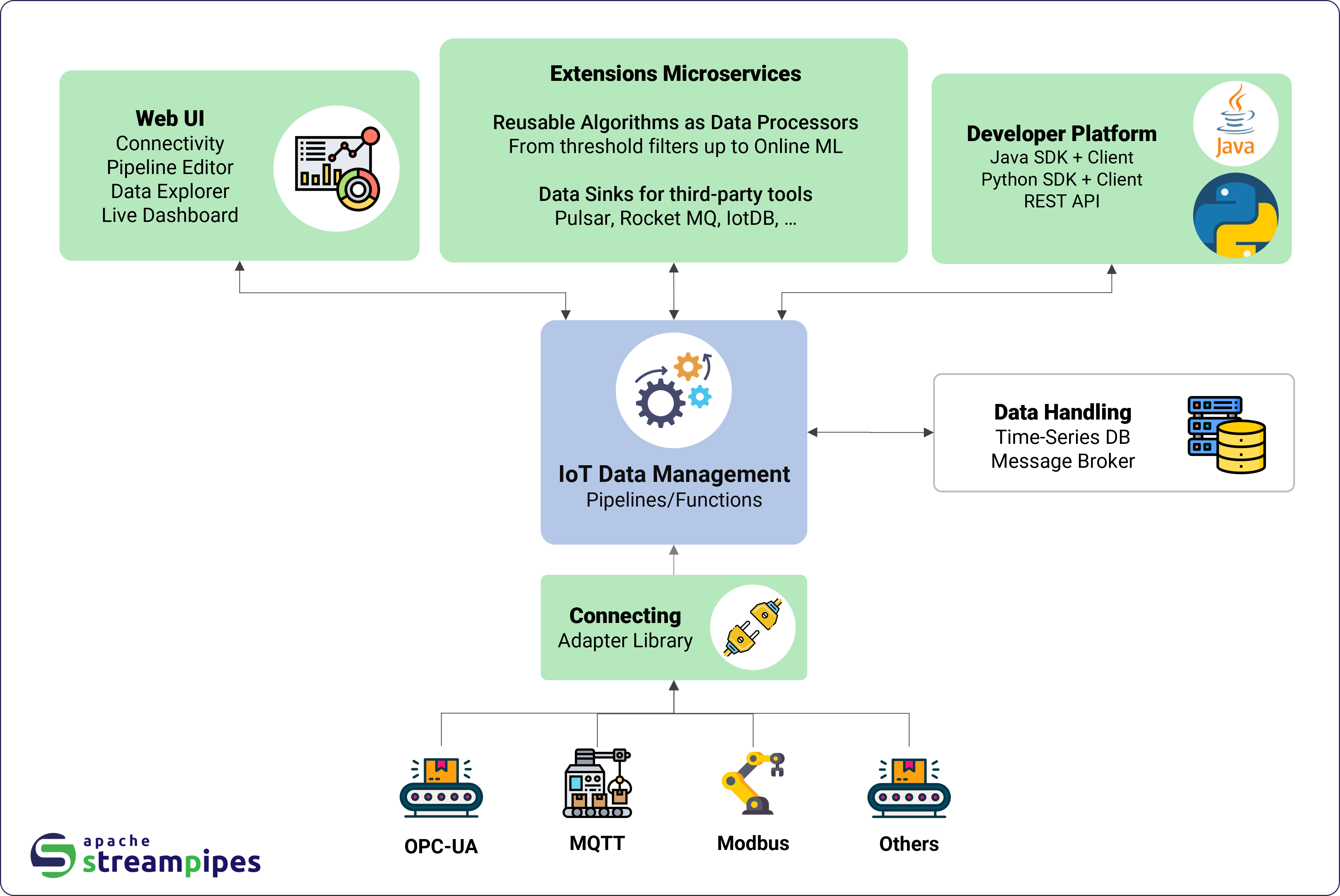
Apache StreamPipes, a widely-used Industrial IoT toolbox, has addressed three vulnerabilities that could expose users to serious security risks, including remote code execution, account hijacking, and server-side request forgery (SSRF).
Race Condition Leads to Account Duplication (CVE-2024-30471)
A time-of-check to time-of-use (TOCTOU) race condition in the user self-registration process could allow attackers to create multiple identical accounts with the same email address. This could lead to user management corruption and potentially compromise system integrity.
Unrestricted File Uploads Enable Remote Code Execution (CVE-2024-31411)
An unrestricted file upload vulnerability could allow authenticated and authorized users to upload executable files, potentially leading to remote code execution. Attackers exploiting this flaw could gain control over the StreamPipes system, jeopardizing sensitive data and operational processes.
SSRF Vulnerability in Pipeline Element Installation (CVE-2024-31979)
A server-side request forgery (SSRF) vulnerability in the pipeline element installation process could allow attackers to trick StreamPipes into sending HTTP GET requests to arbitrary addresses. This could expose internal systems or sensitive information to unauthorized access.
Upgrade to StreamPipes 0.95.0 for Enhanced Security
To mitigate these vulnerabilities, Apache StreamPipes has released version 0.95.0. Users are strongly encouraged to upgrade to this latest version as soon as possible. Upgrading will patch the identified vulnerabilities and strengthen the overall security posture of your StreamPipes environment.


