Google has observed a significant reduction in vulnerabilities within the Android operating system, thanks to its transition to more secure programming languages, such as Rust. Over six years, the percentage of memory-related security vulnerabilities has decreased from 76% to 24%. This shift is part of the “Secure by Design” initiative, which the company now actively adheres to.
The emphasis on secure development has reduced the overall risk associated with code protection and made the transition to new technologies more scalable and cost-efficient. Over time, these changes lead to a reduction in memory-related vulnerabilities and the predominance of secure coding practices in new developments.
Interestingly, the reduction in vulnerabilities is occurring despite the increased volume of new code, which is not always fully secure. Research shows that most vulnerabilities are found in newly written or recently modified code. Thus, the more mature the code becomes, the fewer vulnerabilities are discovered, affirming the necessity for fundamental changes in development approaches.
Google began supporting Rust for Android in 2021, prioritizing the shift to secure languages starting in 2019. As a result, over the past five years, the number of identified memory security issues has dropped from 223 in 2019 to fewer than 50 in 2024.
Advanced methods to combat these vulnerabilities, including the use of Clang sanitizers, have also contributed significantly to their reduction. In the future, the company plans to evolve its memory security strategy, focusing more on “high-efficiency” methods of prevention and integrating security principles at every stage of development.
A key milestone for Google has been establishing compatibility between Rust, C++, and Kotlin, enabling a practical and gradual approach to adopting secure languages without the need for complete code rewrites. This approach effectively leverages the “diminishing” of vulnerabilities: as the addition of new issues ceases, their overall number rapidly declines.
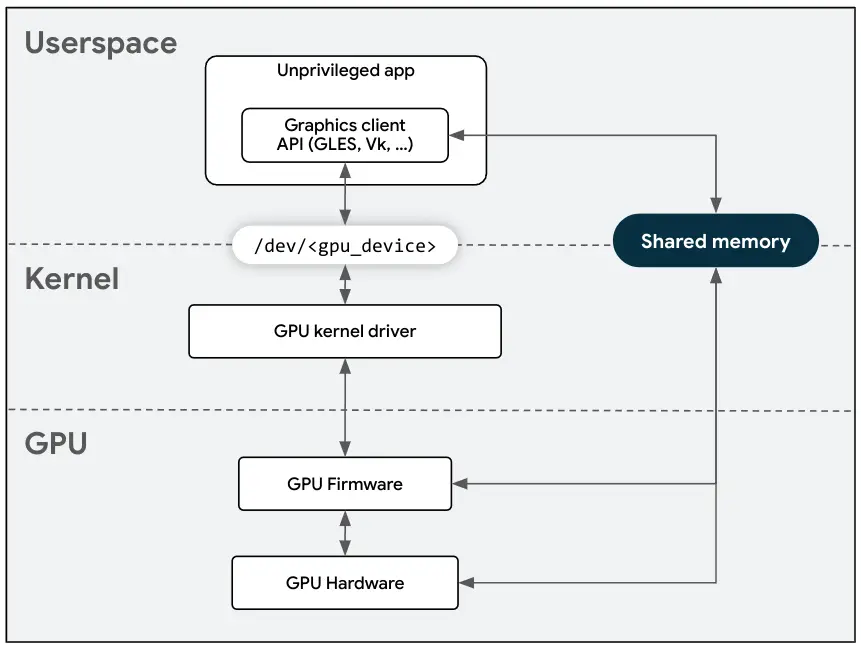
Recently, Google also announced an expanded collaboration with Arm’s security team, aimed at enhancing the security of the GPU stack within the Android ecosystem. This partnership has led to the identification and remediation of several vulnerabilities, including two issues in the Pixel drivers’ customization (CVE-2023-48409 and CVE-2023-48421), as well as a flaw in the Arm Valhall GPU firmware (CVE-2024-0153).
Thus, proactive testing and new approaches to secure coding are helping Google mitigate risks and efficiently address vulnerabilities before they can be exploited.