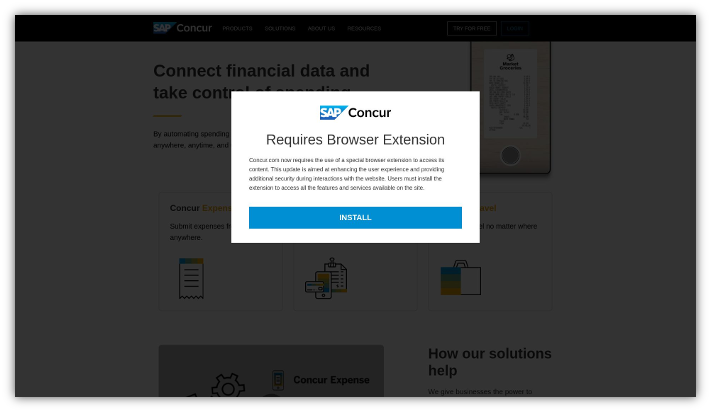
Example of FIN7 live IP hosting an SAP Concur phishing page
Researchers at Silent Push have uncovered a new fraudulent scheme orchestrated by the cybercriminal group Fin7. The perpetrators created multiple websites allegedly offering services to generate fake nude images using artificial intelligence. In reality, these platforms are designed to distribute malware that steals users’ credentials.
Experts identified seven distinct websites marketing themselves as services for creating deepfakes or nude images. Most of them operate under the name “AINude.AI,” with minor variations in domain names. The trap sites are indistinguishable from legitimate platforms offering similar services, featuring a comparable interface design and function set.
Some of the fake sites even allow users to upload images, creating the illusion that the service is functioning. After the image is uploaded, the site offers a download link purportedly containing a “nude” version of the image. However, instead of the promised content, the user receives the RedLine malware, currently one of the most prevalent information stealers.
Once RedLine infects a victim’s computer, it extracts data stored in the browser, including login credentials and cryptocurrency wallet information. This grants the attackers access to the user’s sensitive data.
According to Zak Edwards, Senior Threat Analyst at Silent Push, the scammers primarily target men interested in cutting-edge technologies and cryptocurrencies. The attackers expect that potential victims will refrain from reporting the crime due to the questionable nature of the service they attempted to use.
Following inquiries by journalists from 404 Media, Hostinger, the domain registration provider for most of the fake websites, blocked access to them. However, the threat remains, as one of Fin7’s websites was listed as a recommended resource on a major adult content aggregator.
Fin7 is notorious for its professional approach to cybercrime. The group uses corporate software, such as Hipchat for conducting interviews with recruits and JIRA for task tracking. In the past, Fin7 even created fake companies to hire penetration testing specialists who were unknowingly involved in criminal operations.
Despite the arrests of several group members in 2018 and 2020, Fin7 continues its activities. Earlier this year, SentinelOne discovered that a tool developed by Fin7 to bypass security systems is being advertised in criminal circles and used by various groups involved in ransomware distribution.
Apple and Google previously blocked access to Fin7-related websites through their browsers. However, the malicious sites identified in the latest investigation were accessible in both Chrome and Safari. Representatives from both companies stated that they are reviewing the situation.


