Google has released security updates for its Chrome browser to address a severe zero-day vulnerability, CVE-2024-7971, which is currently being actively exploited by attackers in real-world scenarios. This vulnerability is a ‘Type Confusion’ error in the V8 engine, responsible for executing JavaScript and WebAssembly.
According to the National Vulnerability Database (NIST), the flaw allows a remote attacker to cause memory corruption through a specially crafted HTML page. The issue was reported by Microsoft’s cybersecurity division on August 19, 2024.
Google has yet to disclose specific details about the nature of the attacks or the identities of those who may have exploited this vulnerability. This is to allow most users to update their browsers before the information becomes public. However, the company confirms that the vulnerability is already being actively exploited.
CVE-2024-7971 is the third ‘Type Confusion’ vulnerability in V8 that Google has fixed in 2024, following CVE-2024-4947 and CVE-2024-5274. In total, the company has addressed nine zero-day vulnerabilities in Chrome since the beginning of the year, some of which were demonstrated at the Pwn2Own 2024 hacking competition.
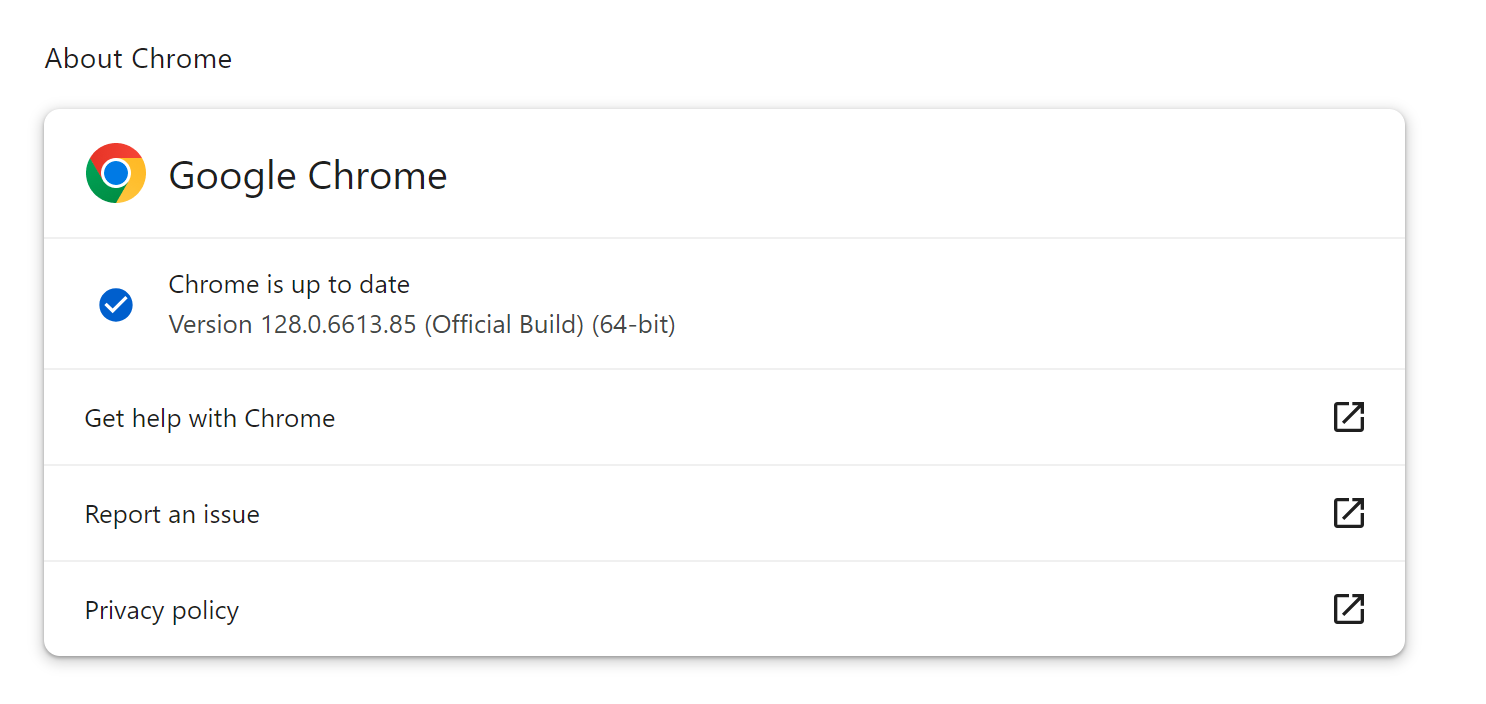
Chrome users on Windows, Linux, and macOS are strongly advised to update their browsers to version 128.0.6613.84 to protect against potential threats. Users of Chromium-based browsers, such as Microsoft Edge, Brave, Opera, and Vivaldi, should also install available updates when they are released.
Typically, browser updates are installed automatically, but it is advisable to manually check the current version of the software in use. These measures will help minimize the risks associated with the vulnerability and protect against potential attacks.


