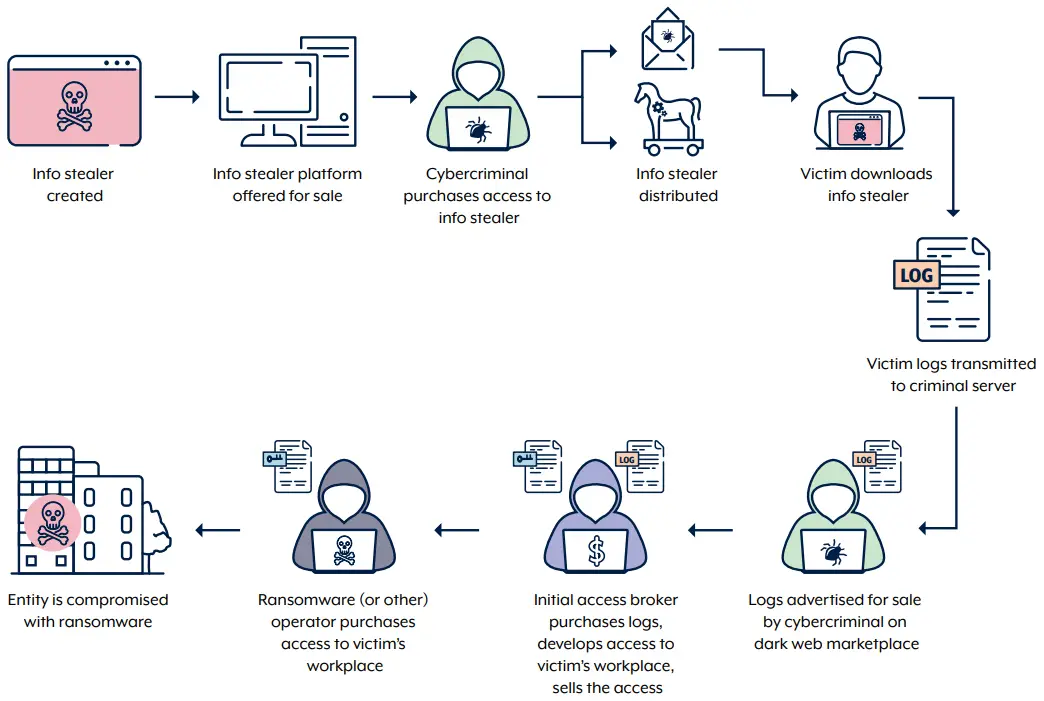
The Australian Cyber Security Centre (ACSC) has issued a warning to organizations about the escalating threat posed by malware known as “infostealers.” These malicious programs harvest sensitive data from users’ devices, including passwords, credit card information, cryptocurrency wallets, and browser data such as cookies and autofill forms. The stolen information is then leveraged by cybercriminals to gain unauthorized access to corporate networks and systems.
Infostealers are frequently distributed through phishing emails, pirated software, and malicious links on various platforms, including social media. Devices used for both work and personal purposes are particularly vulnerable due to lower security standards. This dual-use scenario often leads to the compromise of corporate networks and subsequent attacks, such as ransomware, business email compromise, and intellectual property theft.
Australian companies that permit employees to work remotely on personal devices must exercise heightened caution. Several incidents investigated by the ACSC have shown that data breaches and serious attacks on corporate networks originated from compromised personal devices. Cybercriminals exploited stolen credentials to gain access to privileged accounts.
Infostealers play a pivotal role in cybercrime, providing an easy-to-use tool for attackers with limited technical expertise. Some of these tools are sold under a “Malware-as-a-Service” (MaaS) model, enabling novice cybercriminals to effortlessly launch attacks on targeted systems.
Cybercriminals can remotely control victims’ devices, using infostealers to gather confidential information, including files and passwords. The stolen data is often sold on dark markets or used for extortion and blackmail. Additionally, attackers may deploy other types of malware on already infected devices.
To mitigate the risk, ACSC advises organizations to implement multi-factor authentication (MFA), restrict access to privileged accounts, and regularly train employees on cybersecurity fundamentals. These measures can help prevent phishing attacks and accidental downloads of malicious software.
Monitoring user activity, particularly for remote workers, and detecting anomalies in a timely manner is also crucial. Organizations are encouraged to adopt a “Bring Your Own Device” (BYOD) policy to enhance the security of employees’ personal devices used for work.
The ACSC strongly recommends that organizations establish an incident response plan and take necessary precautions to defend against infostealer attacks.


