Cybersecurity researchers have unveiled the details of a critical vulnerability that allowed attackers to hijack user accounts on a widely used online hotel and car rental booking service. Though recently patched, the flaw posed significant security risks to millions of travelers worldwide.
According to a Salt Labs report, the vulnerability enabled attackers to gain unauthorized access to user accounts, granting them the ability to:
- Book hotels and rental cars using victims’ loyalty points
- Modify or cancel existing reservations
- Act on behalf of compromised users
The flaw affected a service integrated with numerous commercial airline platforms, allowing travelers to seamlessly add hotel bookings to their itineraries.
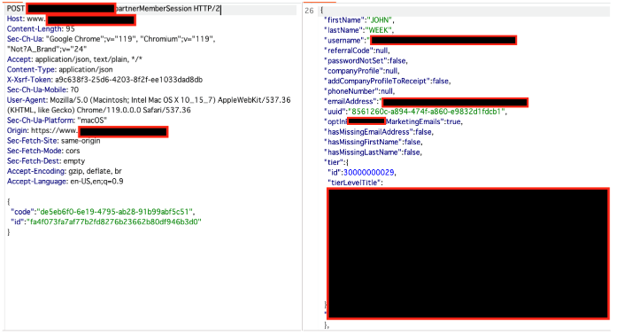
To exploit the vulnerability, a threat actor only needed to send the victim a crafted malicious link, which could be distributed via email, SMS, or compromised websites. Once clicked, the link intercepted session authentication, granting the attacker full control over the user’s account.
The affected booking system relied on OAuth-based authentication, allowing users to log in using their airline credentials. After authentication, users were redirected to the booking platform, where they could redeem their loyalty points for reservations.
The attack hinged on manipulating the “tr_returnUrl” parameter—which determines where the authorization response is sent—redirecting it to a maliciously controlled domain. This session token interception enabled attackers to gain unauthorized access to personal data and accounts.
One of the key challenges in detecting this attack was that it leveraged a legitimate domain, altering only URL parameters rather than modifying the domain itself. This approach evaded traditional domain validation techniques, making it difficult to identify and mitigate using conventional security measures.
Security experts at Salt Labs emphasized that the interconnected nature of digital services creates a lucrative attack surface for supply chain API threats. Such attacks allow adversaries to infiltrate trusted platforms, exfiltrate user data, and impersonate legitimate users.
Incidents like this underscore the urgent need for robust security enhancements, particularly in systems reliant on third-party integrations. Strengthening API security controls and enforcing strict validation on redirect parameters could help prevent similar exploits in the future.