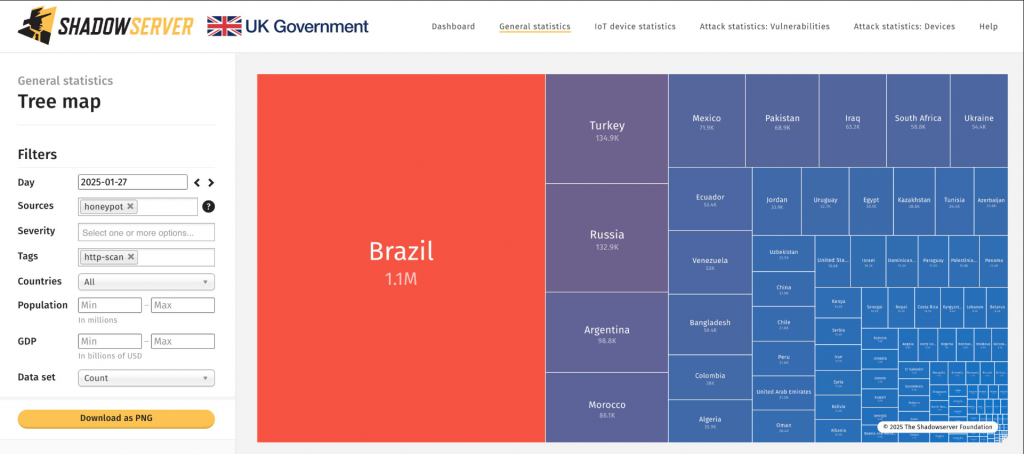
A large-scale brute-force attack has compromised millions of network devices worldwide. According to Shadowserver, cybercriminals are employing nearly 2.8 million IP addresses daily in attempts to breach credentials for devices from Palo Alto Networks, Ivanti, SonicWall, and other manufacturers.
A significant portion of the attacking IP addresses originate from Brazil (1.1 million), followed by Turkey, Russia, Argentina, Morocco, and Mexico. However, thousands of other countries are also involved, underscoring the global scope of the attack. The primary targets are perimeter security devices—firewalls, VPN gateways, and remote access solutions.
Shadowserver reports that while the attack has been ongoing for several weeks, its intensity has surged dramatically in recent days. The campaign leverages routers and IoT devices from MikroTik, Huawei, Cisco, Boa, and ZTE, all of which are commonly exploited in botnets. The use of these devices suggests the involvement of a large network of compromised nodes or a sophisticated residential proxy service.
Residential proxies enable attackers to mask their activities by routing traffic through IP addresses assigned to legitimate internet users. This obfuscation complicates detection and mitigation efforts, as malicious requests appear indistinguishable from normal user traffic. Additionally, hackers can reroute their attacks through corporate networks, leveraging them as exit nodes to further conceal their presence.
Experts strongly recommend enhancing the security of at-risk devices by implementing the following measures:
- Replacing default passwords with strong, unique credentials.
- Enabling multi-factor authentication (MFA) to prevent unauthorized access.
- Restricting access to trusted IP addresses only.
- Disabling web-based administrative interfaces when not in use.
Keeping software up to date with the latest security patches remains one of the most effective defenses. Vulnerabilities in outdated firmware could allow attackers to seize control of devices without even resorting to password brute-forcing.
This incident follows a series of high-profile brute-force attacks targeting network infrastructure. In April last year, Cisco warned of a large-scale credential-stuffing attack aimed at devices from Cisco, CheckPoint, Fortinet, SonicWall, and Ubiquiti. Later, in December, Citrix reported a similar operation targeting NetScaler appliances.
These attacks reflect an alarming surge in cybercriminal activity targeting critical networking infrastructure, reinforcing the urgent need for heightened security measures and continuous monitoring of vulnerable devices.