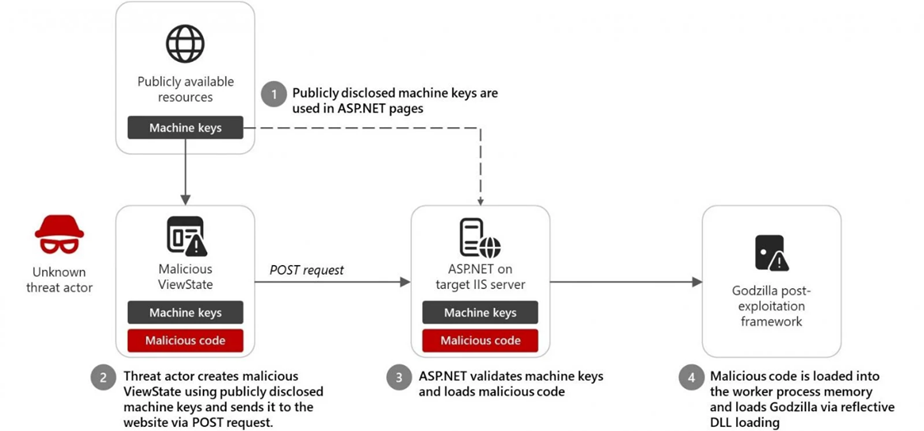
Microsoft has uncovered a novel cyberattack technique in which threat actors exploit a vulnerability in the ViewState mechanism to inject malicious code. The issue stems from developers utilizing static ASP.NET Machine Keys, which have been discovered in publicly accessible sources such as code documentation and repositories.
Machine Keys are intended to safeguard ViewState against tampering and data leaks. However, cybercriminals are leveraging publicly available keys to generate malicious ViewState payloads containing specially crafted Message Authentication Codes (MAC). When these ViewState objects are processed, the IIS server loads them into the worker process memory and executes them, enabling remote code execution and the deployment of additional malware.
In December 2024, an unidentified cybercriminal exploited one such publicly exposed key to deploy the Godzilla web shell, a post-exploitation tool designed for command execution and shellcode injection on IIS servers.
Microsoft has identified over 3,000 publicly available Machine Keys that could be leveraged in similar attacks. Unlike previously known ViewState forgery attacks, which relied on stolen keys traded on darknet marketplaces, this new threat is more insidious: the keys are openly accessible in repositories and can inadvertently become part of development environments without proper scrutiny.
To mitigate the risks, Microsoft advises developers to securely generate Machine Keys, avoid using keys sourced from public repositories, encrypt machineKey and connectionStrings in configuration files, and upgrade applications to ASP.NET 4.8 to enable Antimalware Scan Interface (AMSI). Additionally, organizations should implement security measures on Windows servers, including attack surface reduction rules.
Furthermore, Microsoft has provided guidelines for removing or replacing vulnerable keys via PowerShell and the IIS console, while also purging such key examples from its documentation to prevent misuse.
In the event of a successful compromise, merely rotating the keys may prove insufficient. Microsoft strongly recommends a thorough forensic investigation, and for internet-facing servers, a full system reformat and offline reinstallation, as these systems are at the highest risk.


