The official website of Casio’s British division (casio.co.uk) was compromised in a cyberattack, resulting in user data exfiltration.
This incident forms part of a wider web skimming campaign detected across at least 17 Magento-based or similar platforms. Casio’s site hosted the malicious code from January 14th to 24th, with security specialists uncovering it on January 28th. The company remediated the threat within 24 hours of notification.
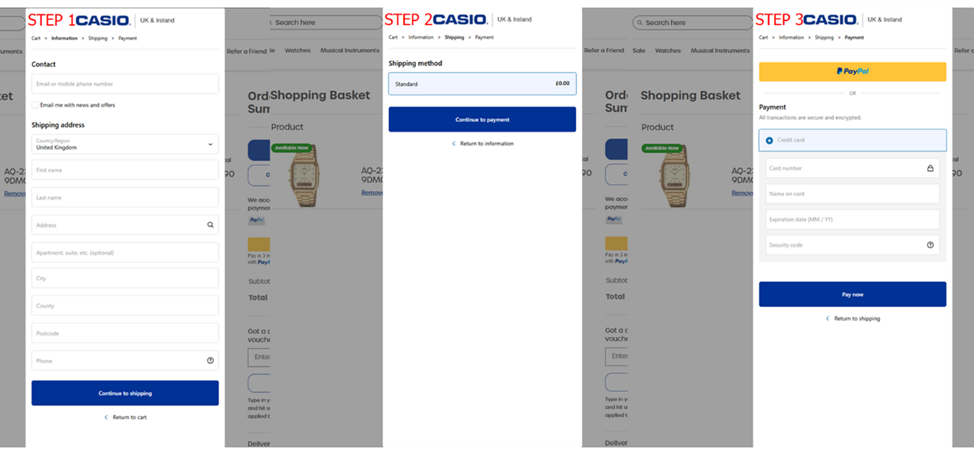
The malicious script, integrated into the site’s core code, deviated from standard web skimming techniques. While such attacks typically target the payment page, this instance spanned all site pages except “/checkout,” enabling data collection before checkout initiation. The shopping cart presented a counterfeit data entry form, mimicking the genuine purchase interface.
This fraudulent form solicited address, phone number, name, and bank card details, transmitting the entered information to a remote server via AES-256-CBC encryption. Uniquely, after data submission, users received an error message and were redirected to the legitimate checkout section, re-prompted to complete payment fields. This “Double Entry” method validates information authenticity for fraudsters.
The skimmer’s code employed multiple obfuscation layers, including a bespoke variable encoding mechanism and XOR-based string concealment, evading static analysis and WAF systems. The sporadic absence of the malicious script code hinted at built-in detection avoidance mechanisms.
All compromised sites loaded the malicious code from specific servers. Despite domain name variations, the core malicious code similarity suggests a single attack orchestrator or a unified generation tool. The use of long-registered yet inactive domains further facilitated cybercriminal evasion.
Casio UK’s security system included a Content Security Policy (CSP), but its reporting mode, lacking automatic violation blocking, permitted the malicious code’s unimpeded infiltration.
This incident underscores the need for both protection mechanism implementation and meticulous configuration and monitoring. Web skimming remains a significant threat to online businesses, particularly those handling customer payment data. Effective defense necessitates automated monitoring and attack prevention solutions, as manual security system management often proves inadequate.
This follows Casio’s October 2024 ransomware attack, which compromised thousands of employee, customer, and business partner data. Casio reported 6,456 affected employees, 1,931 business partners, and 91 customers, with investigations citing phishing emails as the initial intrusion vector on October 5th.