A single installed application on a freshly reset iPhone can secretly collect and transmit personal user data, even if the user has explicitly denied tracking permissions. This alarming discovery was made by an independent security researcher known under the pseudonym Tim.
Apple’s “Ask App Not to Track” feature is intended to protect users’ privacy, preventing apps from accessing the device’s Identifier for Advertisers (IDFA). For years, Apple has assured users that this setting also blocks developers from tracking individuals through alternative means, such as email addresses. However, Tim’s investigation suggests otherwise.
To test Apple’s claims, Tim wiped an iPhone 11 to factory settings and installed only one game from KetchApp, a developer with over 200 apps available in the App Store. He then set up a proxy server to monitor all outgoing network traffic.
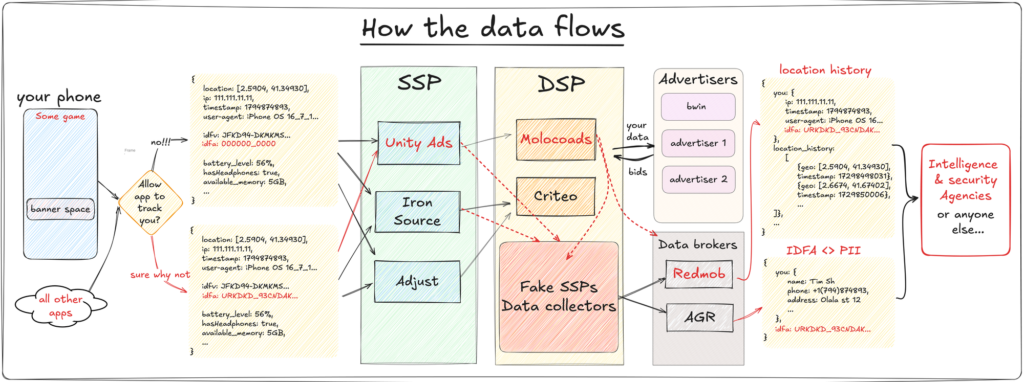
What he discovered is enough to unsettle even the most devoted Apple enthusiasts—the app transmitted data every fraction of a second, embedding over 200 different parameters in each packet, including the device’s geolocation. All of this information was sent directly to the developers of the Unity game engine, on which the game was built. Although Tim noted that the location data was somewhat imprecise—since the iPhone was operating without a SIM card and solely on Wi-Fi—the implications were still concerning.
Even more troubling was the discovery that timestamped data and IP addresses were being relayed to Facebook’s servers—despite the absence of any Meta apps on the phone and without the user’s consent. While the “Ask App Not to Track” feature did indeed reset the advertising identifier, the app continued harvesting a vast array of other sensitive data.
Each outgoing request contained more than 20 unique identifiers, including:
- Identifier for Vendor (IFV)
- Transaction ID (TID)
- Session ID (SID)
- Device ID
- User ID (UID)
The app also logged screen brightness, available memory, battery level, and even whether headphones were connected.
This data was then forwarded to Moloco, a company that operates as a Demand-Side Platform (DSP), claiming to reach 6.7 billion devices across more than 190 countries. Such platforms do more than merely connect advertisers with ad placements—they aggregate massive datasets to enable hyper-targeted advertising. Moreover, any participant in the ad auction ecosystem can potentially access some or all of this collected data.
Tim identified hundreds of companies trading in this kind of data, with some explicitly offering to link advertising IDs (MAIDs) to real-world identities, continuously updating this information. Alarmingly, he even found one firm that directly associates advertising IDs with full names, email addresses, phone numbers, and home addresses.
When Tim attempted to purchase his own data, he was deterred by the cost—access to databases containing information on millions of users was priced between $10,000 and $50,000. Worse yet, these databases are not limited to law enforcement or intelligence agencies—anyone with enough money can buy them. According to the researcher, these databases store detailed movement histories of anyone who has played even briefly with free-to-play applications.
Tim’s findings quickly gained traction on Hacker News, where his post garnered a record number of upvotes over the weekend. In the comments, many acknowledged a grim reality: as long as companies and data brokers profit from this ecosystem, true privacy remains unattainable without systemic change. Even without a unique advertising identifier, applications still collect enough metadata to identify individuals with 99% accuracy.
Experts recommend:
- Denying location access to apps whenever possible
- Spoofing GPS data to provide misleading location information
- Using private DNS filters (such as Pi-Hole or encrypted DNS services)
- Enabling ad blockers to minimize data exposure
However, some analysts argue that complete protection is nearly impossible—developers have mastered circumventing privacy defenses, such as by embedding hardcoded IP addresses within their apps to bypass traditional blocking mechanisms.