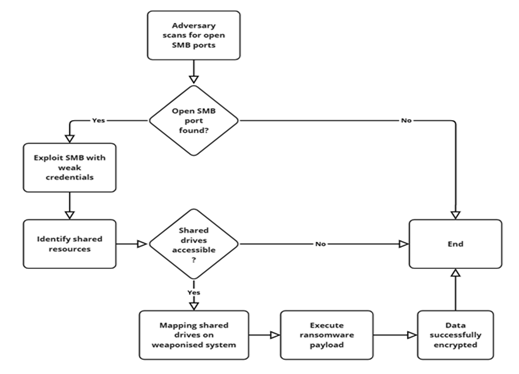
Ransomware attacks continue to evolve, exploiting overlooked vulnerabilities with increasing sophistication. One such weak point is the misconfigured Server Message Block (SMB) protocol, a widely used mechanism for file and resource sharing across networks. When left unprotected, SMB services become an easy target for cybercriminals.
According to researchers at Seqrite Labs, a hacker group known as WantToCry—though its connection to WannaCry remains unconfirmed—intensified its attacks in 2024 by leveraging vulnerabilities in SMB, SSH, FTP, and other network services. Their primary method of compromise involves credential stuffing, utilizing an extensive database of login credentials. Once access is obtained, attackers encrypt files on network drives and storage devices, leaving behind a ransom note with payment instructions.
Despite advancements in cybersecurity solutions and threat detection mechanisms, cybercriminals remain relentless. WantToCry not only employs brute-force attacks but also encrypts files remotely, without deploying malware onto local machines. This technique allows them to evade antivirus detection and complicates incident analysis.
Indicators of compromise point to active IP addresses that have been used in the attacks. Once a system is compromised, the attackers direct victims to communicate via encrypted channels such as Telegram and Tox. Encrypted files are appended with the “.want_to_cry” extension, and a text file containing ransom payment instructions is deposited within affected directories.
The core issue lies in SMB’s frequent exposure to the internet, often left accessible without authentication or secured with outdated credentials. This oversight enables attackers not only to encrypt files but also to move laterally within the network, compromising additional devices. Publicly exposed SMB services, particularly those with weak defenses, are prime targets for automated attacks.
To mitigate such risks, security experts recommend disabling SMB if it is not essential and restricting internet access to ports 445 and 139. Additionally, implementing strong passwords, regularly updating software, and enforcing multi-factor authentication are critical measures in strengthening network defenses.
The deployment of advanced antivirus solutions and network monitoring tools aids in detecting suspicious activity at an early stage. However, even the most sophisticated security measures cannot fully compensate for human error—proper network configuration remains a cornerstone of effective cybersecurity.


