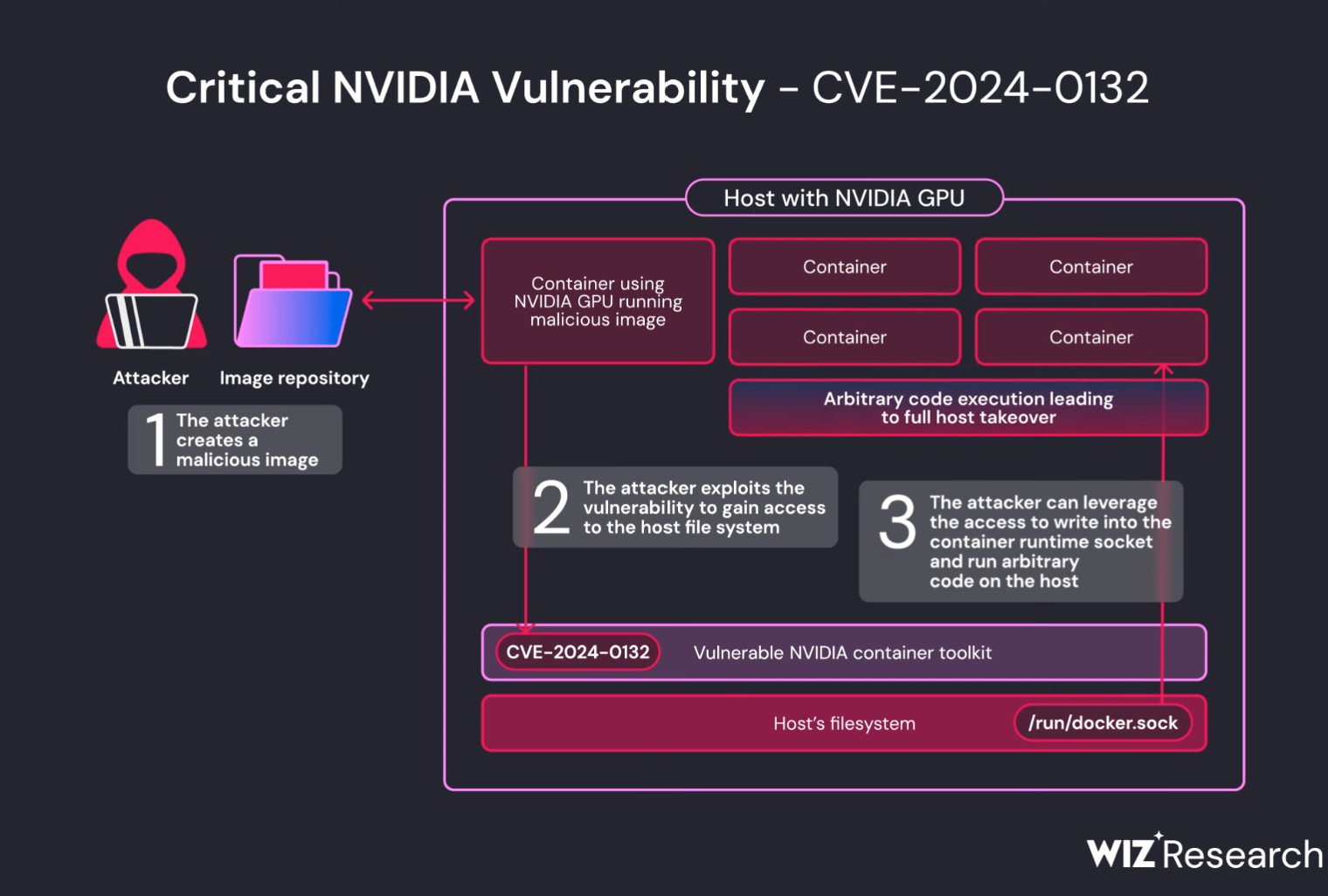
A critical vulnerability was recently discovered in NVIDIA Container Toolkit, enabling attackers to escape the container environment and gain full access to the host system. The vulnerability, identified as CVE-2024-0132, received a CVSS score of 9.0 out of 10.
The issue affects all versions of the NVIDIA Container Toolkit up to v1.16.1 and the NVIDIA GPU Operator up to version 24.6.1. The root cause lies in a Time-of-Check Time-of-Use (TOCTOU) flaw.
When used with default settings, a specially crafted container image can access the host’s file system. Exploiting this vulnerability could lead to arbitrary code execution, denial of service, privilege escalation, information disclosure, and data tampering. However, environments utilizing the Container Device Interface (CDI) remain unaffected.
The vulnerability was discovered by the security firm Wiz, which reported it to NVIDIA on September 1 of this year. According to researchers, the attack is feasible if the attacker has control over container images run through the Toolkit. In such a case, a potential attacker could execute what is known as a “container escape” and gain access to the host system.
A likely attack scenario involves the creation of a malicious container image. If this image is executed on a target platform, either directly or through services allowing shared GPU usage, the attacker could gain full access to the host file system, enabling attacks on the supply chain or shared-resource services.
With access to Container Runtime sockets (docker.sock/containerd.sock), the attacker would be able to execute arbitrary commands on the host system with root privileges, essentially seizing complete control of the device.
This vulnerability poses a particular threat to orchestrated multi-tenant environments, where an attacker could escape the container and access the data and secrets of other applications running on the same node or cluster.
The vulnerability has been patched in NVIDIA Container Toolkit v1.16.2 and NVIDIA GPU Operator v24.6.2. To prevent exploitation, technical details of the attack have not yet been disclosed. Users are strongly advised to apply the available updates as soon as possible.


