Seven years after the emergence of the Ngioweb botnet, it remains one of the foremost cybersecurity threats. This proxy server is actively exploited by cybercriminals to seek out vulnerable devices, such as routers and IoT gadgets, which are then transformed into “resident” proxies and sold through the Nsocks platform. Access to these compromised IP addresses is priced as low as $0.20 per day, and the global availability of such proxies enables hackers to obscure their activities.
Nsocks offers clients access to around 30,000 IP addresses at prices reaching $1.50 for 24-hour access. Approximately 75% of infected devices belong to private users, making them a prime target. The most frequently attacked devices include Zyxel routers, Linear eMerge systems, and Neato robotic vacuums. Specialized scanners for each type of vulnerable device allow cybercriminals to conceal their full array of exploits, complicating detection efforts.
Since Ngioweb was first reported by Check Point in 2018, its code has undergone minimal changes. The command-and-control channels, which attackers use to monitor infected devices, have also remained intact. Despite researchers’ efforts to disrupt Ngioweb’s operations, criminals have introduced unique checks to help evade detection.
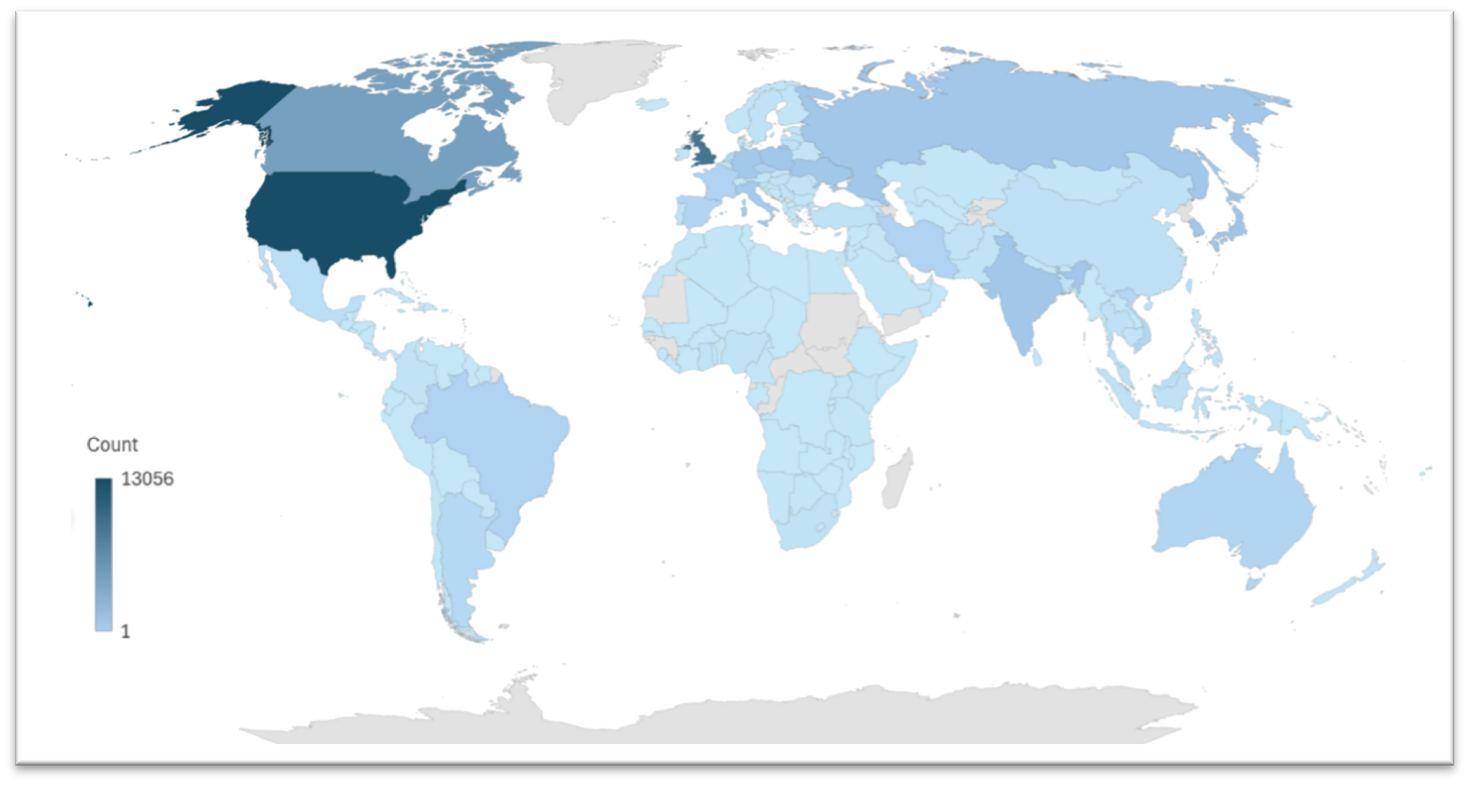
Last year saw a sharp increase in the number of proxies operating via Ngioweb, driven by the discovery of new vulnerabilities and the frequent use of low-profile IP addresses. For instance, LevelBlue Labs recently documented infections in Linear eMerge and Zyxel devices, which are exploited to access IP addresses worldwide, including in the United States, the United Kingdom, and Canada.
Operating since 2022, Nsocks markets infected systems as SOCKS5 proxies, allowing cybercriminals to select devices by location, connection speed, and device type. Payments are exclusively in cryptocurrency, ensuring anonymity for both the attackers and their clients.
The extensive use of consumer devices, such as Neato and Zyxel products, underscores the growing victimization of private users. These devices continue connecting to the internet, often unaware of the threat, and serve as conduits for anonymizing malicious activities by cybercriminals.


